Exam Details
Exam Code
:NSE4_FGT-7.2Exam Name
:Fortinet NSE 4 - FortiOS 7.2Certification
:Fortinet CertificationsVendor
:FortinetTotal Questions
:185 Q&AsLast Updated
:Aug 11, 2025
Fortinet Fortinet Certifications NSE4_FGT-7.2 Questions & Answers
-
Question 131:
Refer to the exhibits.
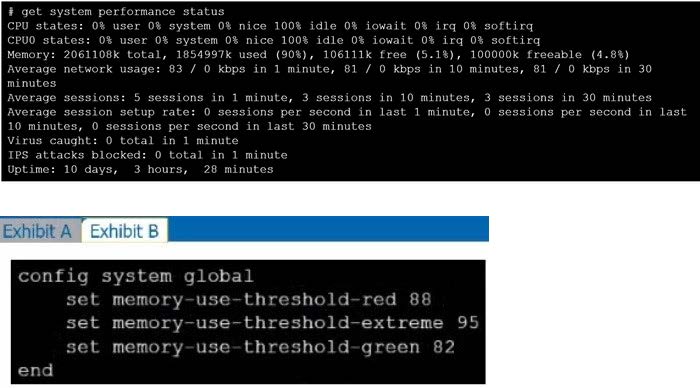
Exhibit A shows system performance output. Exhibit B shows a FortiGate configured with the default configuration of high memory usage thresholds. Based on the system performance output, which two statements are correct? (Choose two.)
A. Administrators can access FortiGate only through the console port.
B. FortiGate has entered conserve mode.
C. FortiGate will start sending all files to FortiSandbox for inspection.
D. Administrators cannot change the configuration.
-
Question 132:
Refer to the exhibits.
The exhibits show the firewall policies and the objects used in the firewall policies.
The administrator is using the Policy Lookup feature and has entered the search criteria shown in the exhibit.
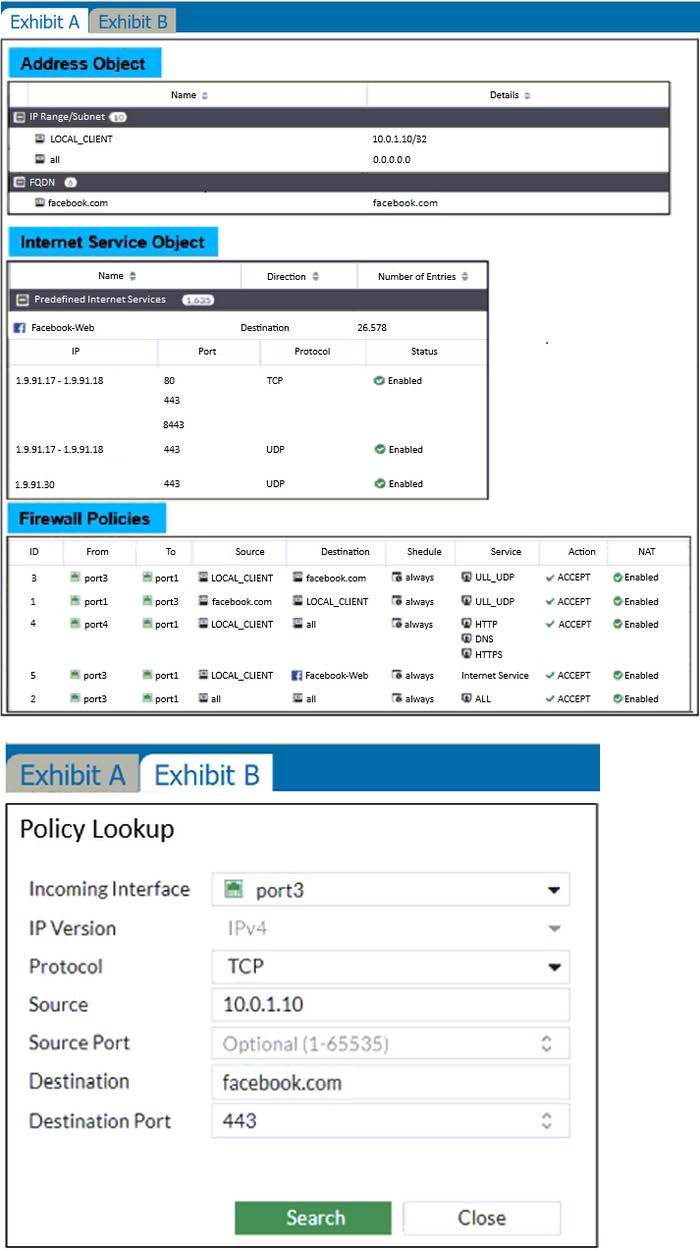
Which policy will be highlighted, based on the input criteria?
A. Policy with ID 4.
B. Policy with ID 5.
C. Policies with ID 2 and 3.
D. Policy with ID 4.
-
Question 133:
If Internet Service is already selected as Source in a firewall policy, which other configuration objects can be added to the Source filed of a firewall policy?
A. IP address
B. Once Internet Service is selected, no other object can be added
C. User or User Group
D. FQDN address
-
Question 134:
Which three statements explain a flow-based antivirus profile? (Choose three.)
A. Flow-based inspection uses a hybrid of the scanning modes available in proxy-based inspection.
B. If a virus is detected, the last packet is delivered to the client.
C. The IPS engine handles the process as a standalone.
D. FortiGate buffers the whole file but transmits to the client at the same time.
E. Flow-based inspection optimizes performance compared to proxy-based inspection.
-
Question 135:
On FortiGate, which type of logs record information about traffic directly to and from the FortiGate management IP addresses?
A. System event logs
B. Forward traffic logs
C. Local traffic logs
D. Security logs
-
Question 136:
A network administrator is troubleshooting an IPsec tunnel between two FortiGate devices. The administrator has determined that phase 1 fails to come up. The administrator has also re-entered the pre-shared key on both FortiGate devices to make sure they match.
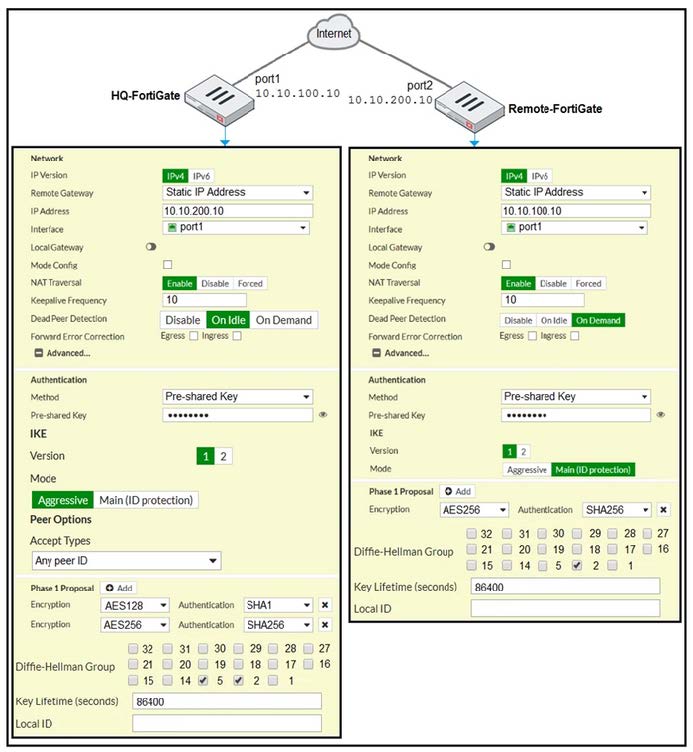
Based on the phase 1 configuration and the diagram shown in the exhibit, which two configuration changes will bring phase 1 up? (Choose two.)
A. On HQ-FortiGate, set IKE mode to Main (ID protection).
B. On both FortiGate devices, set Dead Peer Detection to On Demand.
C. On HQ-FortiGate, disable Diffie-Helman group 2.
D. On Remote-FortiGate, set port2 as Interface.
-
Question 137:
Which feature in the Security Fabric takes one or more actions based on event triggers?
A. Fabric Connectors
B. Automation Stitches
C. Security Rating
D. Logical Topology
-
Question 138:
Which timeout setting can be responsible for deleting SSL VPN associated sessions?
A. SSL VPN idle-timeout
B. SSL VPN http-request-body-timeout
C. SSL VPN login-timeout
D. SSL VPN dtls-hello-timeout
-
Question 139:
The IPS engine is used by which three security features? (Choose three.)
A. Antivirus in flow-based inspection
B. Web filter in flow-based inspection
C. Application control
D. DNS filter
E. Web application firewall
-
Question 140:
Refer to the exhibits.
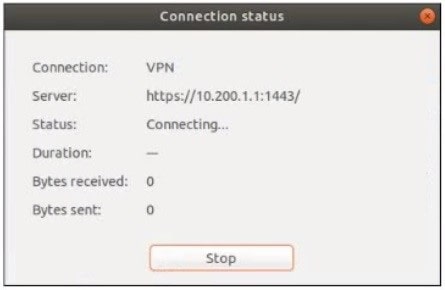
The SSL VPN connection fails when a user attempts to connect to it. What should the user do to successfully connect to SSL VPN?
A. Change the SSL VPN port on the client.
B. Change the Server IP address.
C. Change the idle-timeout.
D. Change the SSL VPN portal to the tunnel.
Related Exams:
FCP_FAZ_AD-7.4
FCP - FortiAnalyzer 7.4 AdministratorFCP_FGT_AD-7.4
FCP - FortiGate 7.4 AdministratorFCP_FGT_AD-7.6
FortiGate 7.6 Administrator FCP_FGT_AD-7.6FCP_WCS_AD-7.4
FCP - AWS Cloud Security 7.4 AdministratorFCSS_EFW_AD-7.4
FCSS - Enterprise Firewall 7.4 AdministratorFCSS_NST_SE-7.4
FCSS - Network Security 7.4 Support EngineerFCSS_SASE_AD-24
FCSS - FortiSASE 24 AdministratorNSE4_FGT-5.6
Fortinet NSE 4 - FortiOS 5.6NSE4_FGT-6.0
Fortinet NSE 4 - FortiOS 6.0NSE4_FGT-6.4
Fortinet NSE 4 - FortiOS 6.4
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Fortinet exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your NSE4_FGT-7.2 exam preparations and Fortinet certification application, do not hesitate to visit our Vcedump.com to find your solutions here.