NSE4_FGT-7.2 Exam Details
-
Exam Code
:NSE4_FGT-7.2 -
Exam Name
:Fortinet NSE 4 - FortiOS 7.2 -
Certification
:Fortinet Certifications -
Vendor
:Fortinet -
Total Questions
:185 Q&As -
Last Updated
:Jan 13, 2026
Fortinet NSE4_FGT-7.2 Online Questions & Answers
-
Question 1:
What is a reason for triggering IPS fail open?
A. The IPS socket buffer is full and the IPS engine cannot process additional packets.
B. The IPS engine cannot decode a packet.
C. The IPS engine is upgraded.
D. The administrator enabled NTurbo acceleration. -
Question 2:
What are two scanning techniques supported by FortiGate? (Choose two.)
A. Machine learning scan
B. Antivirus scan
C. Ransomware scan
D. Trojan scan -
Question 3:
What is the primary FortiGate election process when the HA override setting is disabled?
A. Connected monitored ports > Priority > HA uptime > FortiGate serial number
B. Connected monitored ports > System uptime > Priority > FortiGate serial number
C. Connected monitored ports > Priority > System uptime > FortiGate serial number
D. Connected monitored ports > HA uptime > Priority > FortiGate serial number -
Question 4:
Which three pieces of information does FortiGate use to identify the hostname of the SSL server when SSL certificate inspection is enabled? (Choose three.)
A. The host field in the HTTP header
B. The subject alternative name (SAN) field in the server certificate
C. The subject field in the server certificate
D. The server name indication (SNI) extension in the client hello message
E. The serial number in the server certificate -
Question 5:
Refer to the exhibit to view the firewall policy.
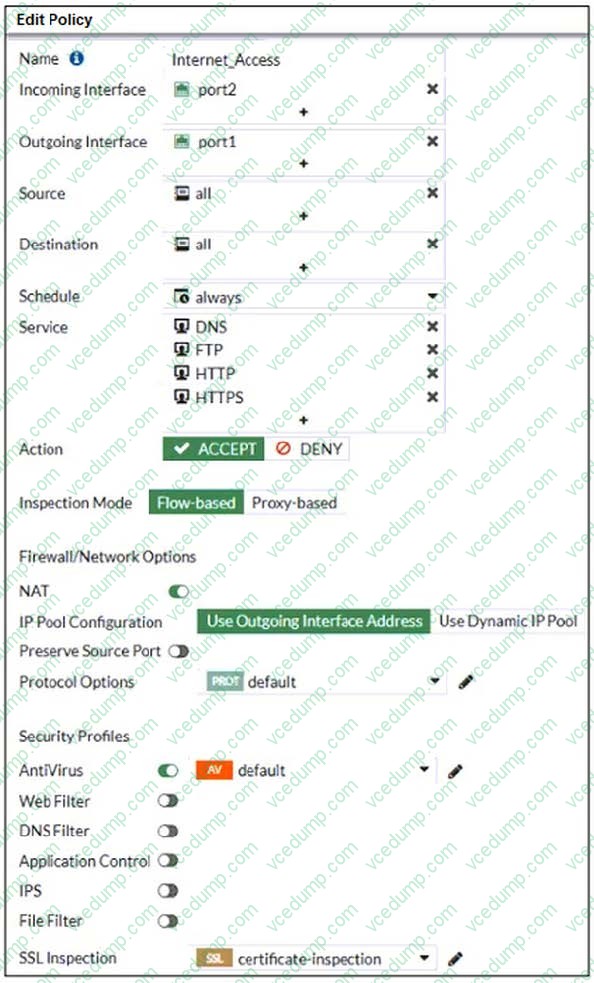
Why would the firewall policy not block a well-known virus, for example eicar?
A. Web filter is not enabled on the firewall policy to complement the antivirus profile.
B. The firewall policy is not configured in proxy-based inspection mode.
C. The firewall policy does not apply deep content inspection.
D. The action on the firewall policy is not set to deny. -
Question 6:
Refer to the exhibit.
The exhibit shows a diagram of a FortiGate device connected to the network and the firewall policy and IP pool configuration on the FortiGate device.
Two PCs, PC1 and PC2, are connected behind FortiGate and can access the internet successfully. However, when the administrator adds a third PC to the network (PC3), the PC cannot connect to the internet.
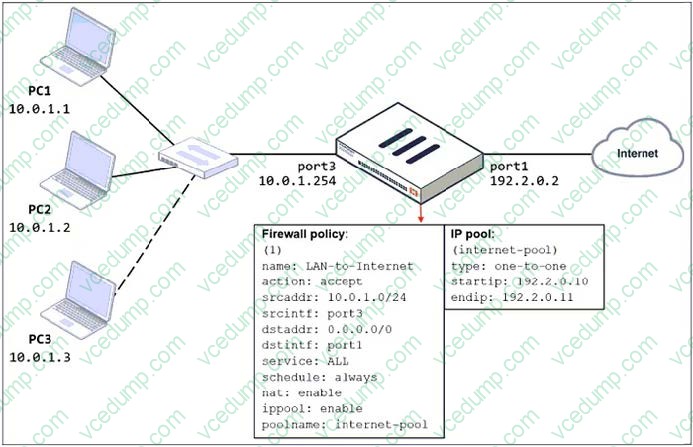
Based on the information shown in the exhibit, which three configuration changes should the administrator make to fix the connectivity issue for PC3? (Choose three.)
A. In the IP pool configuration, set type to overload. Most Voted
B. Configure 192.2.0.12/24 as the secondary IP address on port1.
C. In the firewall policy configuration, disable ippool. Most Voted
D. In the IP pool configuration, set endip to 192.2.0.12. Most Voted
E. Configure another firewall policy that matches only the address of PC3 as source, and then place the policy on top of the list. -
Question 7:
How can you disable RPF checking?
A. Disable fail-detect on the interface level settings.
B. Disable strict-src-check under system settings.
C. Unset fail-alert-interfaces on the interface level settings.
D. Disable src-check on the interface level settings. -
Question 8:
Refer to the exhibit.
In the network shown in the exhibit, the web client cannot connect to the HTTP web server. The administrator runs the FortiGate built-in sniffer and gets the output shown in the exhibit.
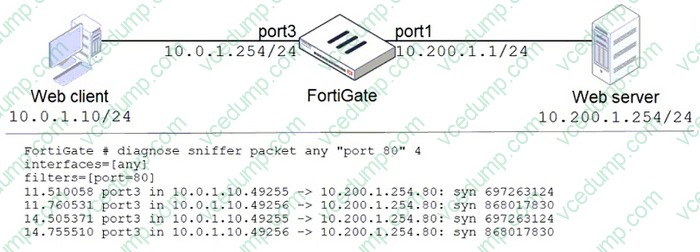
What should the administrator do next, to troubleshoot the problem?
A. Execute a debug flow.
B. Capture the traffic using an external sniffer connected to port1.
C. Execute another sniffer on FortiGate, this time with the filter "host 10.0.1.10".
D. Run a sniffer on the web server. -
Question 9:
Refer to the exhibits.
The exhibits contain a network interface configuration, firewall policies, and a CLI console configuration.
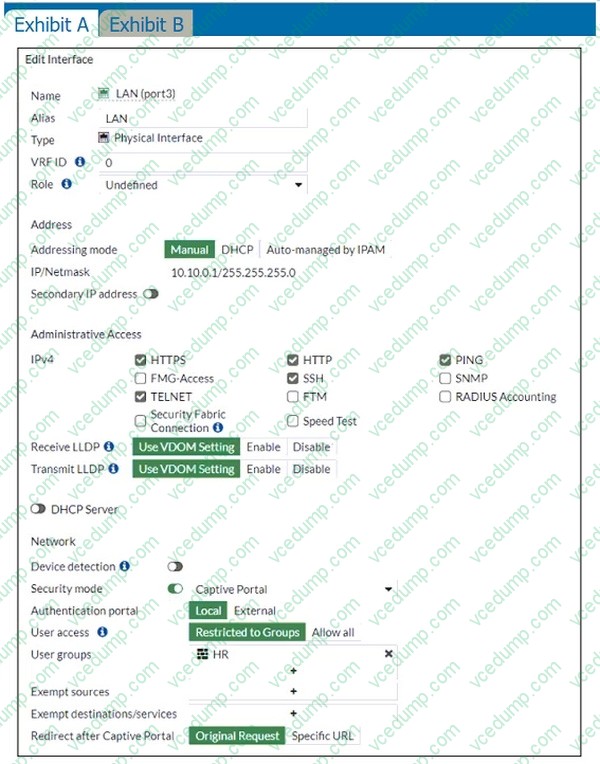
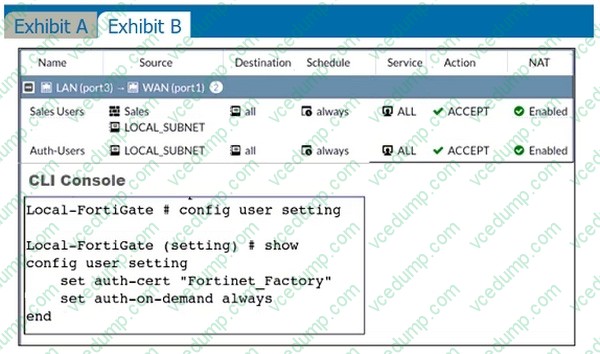
How will the FortiGate device handle user authentication for traffic that arrives on the LAN interface?
A. All users will be prompted for authentication; users from the HR group can authenticate successfully with the correct credentials.
B. If there is a fall-through policy in place, users will not be prompted for authentication.
C. All users will be prompted for authentication; users from the sales group can authenticate successfully with the correct credentials.
D. Authentication is enforced only at a policy level; all users will be prompted for authentication. -
Question 10:
Refer to the exhibits.
Exhibit A shows a network diagram. Exhibit B shows the central SNAT policy and IP pool configuration.
The WAN (port1) interface has the IP address 10.200.1.1/24.
The LAN (port3) interface has the IP address 10.0.1.254/24.
A firewall policy is configured to allow all destinations from LAN (port3) to WAN (port1).
Central NAT is enabled, so NAT settings from matching central SNAT policies will be applied.
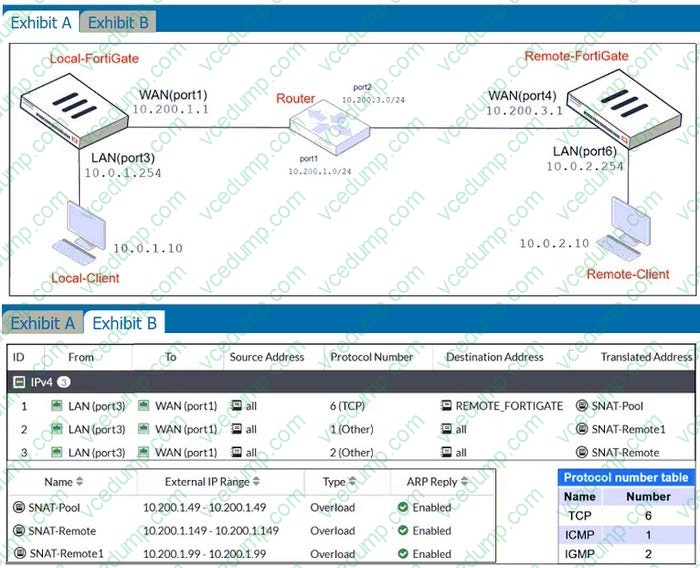
Which IP address will be used to source NAT (SNAT) the traffic, if the user on Local-Client (10.0.1.10) pings the IP address of Remote-FortiGate (10.200.3.1)?
A. 10.200.1.99
B. 10.200.1.1
C. 10.200.1.49
D. 10.200.1.149
Related Exams:
-
EMEA-ADVANCED-SUPPORT
Fortinet EMEA Advanced Support -
FCP_FAC_AD-6.5
FCP - FortiAuthenticator 6.5 Administrator -
FCP_FAZ_AD-7.4
FCP - FortiAnalyzer 7.4 Administrator -
FCP_FAZ_AN-7.4
FCP - FortiAnalyzer 7.4 Analyst -
FCP_FCT_AD-7.2
FCP - Forti Client EMS 7.2 Administrator -
FCP_FGT_AD-7.4
FCP - FortiGate 7.4 Administrator -
FCP_FGT_AD-7.6
FortiGate 7.6 Administrator FCP_FGT_AD-7.6 -
FCP_FMG_AD-7.4
FCP - FortiManager 7.4 Administrator -
FCP_FMG_AD-7.6
FortiManager 7.6 Administrator -
FCP_FML_AD-7.4
FCP - FortiMail 7.4 Administrator
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Fortinet exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your NSE4_FGT-7.2 exam preparations and Fortinet certification application, do not hesitate to visit our Vcedump.com to find your solutions here.