HPE6-A79 Exam Details
-
Exam Code
:HPE6-A79 -
Exam Name
:Aruba Certified Mobility Expert Written -
Certification
:HP Certifications -
Vendor
:HP -
Total Questions
:55 Q&As -
Last Updated
:Jan 07, 2026
HP HPE6-A79 Online Questions & Answers
-
Question 1:
Refer to the exhibit.
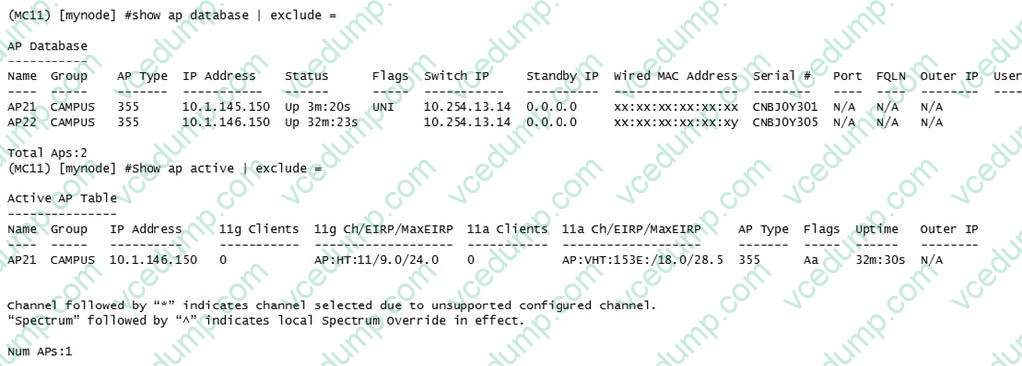
A network administrator deploys a new Mobility Master (MM) - Mobility Controller (MC) network. To test the solution, the network administrator accesses the console of a pair of APs and statically provisions them. However, one of the APs does not propagate the configured SSIDs. The network administrator looks at the logs and sees the output shown in the exhibit.
Which actions must the network administrator take to solve the problem?
A. Create another AP group in the MC's configuration, and re-provision one AP with a different group.
B. Re-provision one of the APs with a different name, and add new entries with the proper group in the whitelist.
C. Re-provision the AP with a different group, and modify the name of one AP in the whitelist.
D. Re-provision one of the APs with a different name or modify the name in the whitelist. -
Question 2:
Refer to the exhibit.

The network administrator must ensure that the configuration will force users to authenticate periodically every eight hours. Which configuration is required to effect this change?
A. Set the reauth-period to 28800 enable reauthentication in the dot1x profile.
B. Set the reauth-period to 28800 enable reauthentication in the AAA profile.
C. Set the reauth-period to 28800 enable reauthentication in both dot1x and AAA profile.
D. Set the reauth-period to 28800 in the dot1x profile and enable reauthentication in the AAA profile. -
Question 3:
Refer to the exhibit.
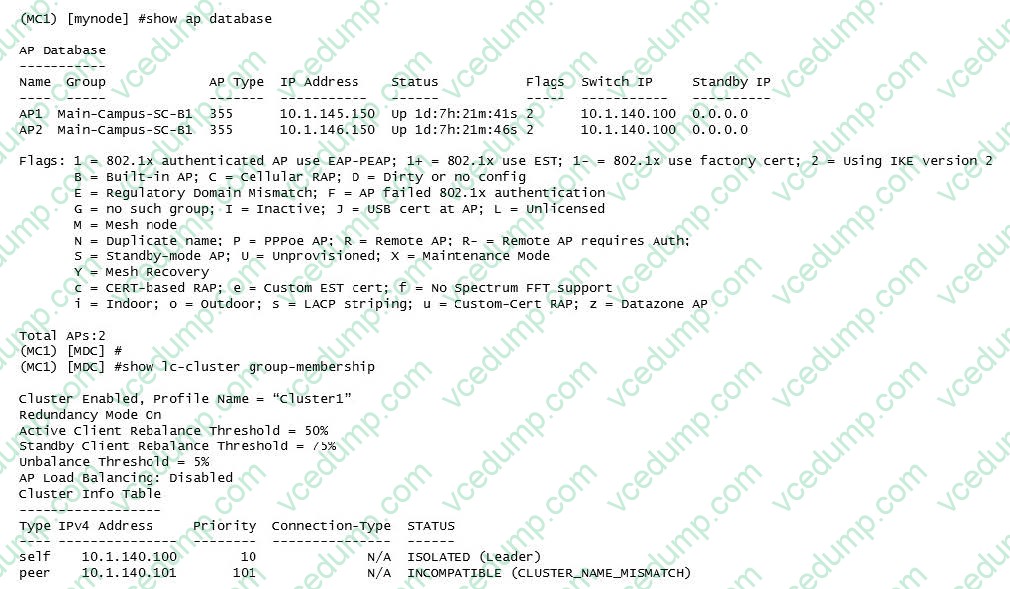
After deploying several cluster pairs, the network administrator notices that all APs assigned to Cluster1 communicate with MC1 instead of being distributed between members of the cluster. Also, no IP addresses are shown under the Standby IP column.
What should the network administrator do to fix this situation?
A. Apply the same cluster profile to both members.
B. Enable Cluster AP load balancing.
C. Rename the cluster profile as "CLUSTER1".
D. Place MCs at the same hierarchical group level. -
Question 4:
Refer to the exhibits.
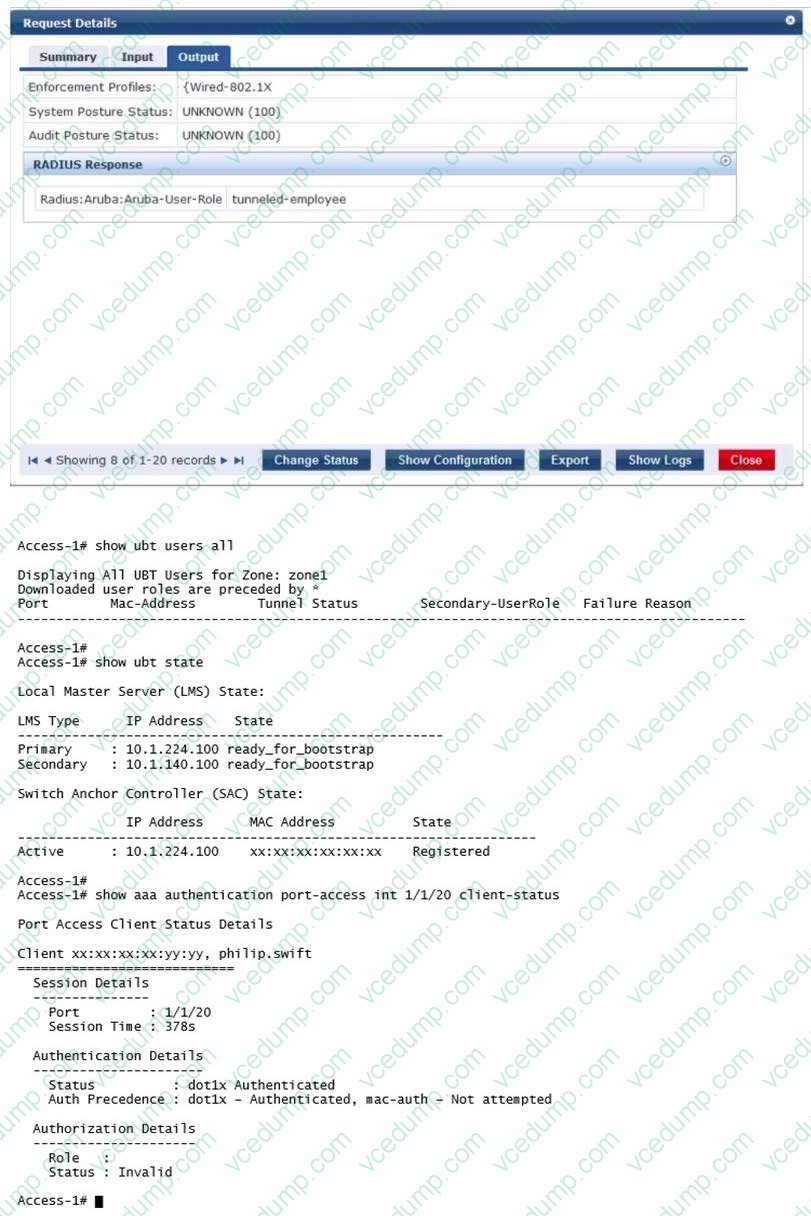
A network administrator deploys User Based Tunneling (UBT) in a corporate network to unify the security policies enforcement. When users authenticate with 802.1X, ClearPass shows Accept results, and sends the Aruba-User-Role attribute as expected. However, the AOS-CX based switch does not seem to build the tunnel to the Mobility Controller (MC) for this user.
Why does the switch fail to run UBT for the user?
A. The switch has not fully associated to the MC.
B. ClearPass is sending the wrong Vendor ID.
C. The switch is not configured with the gateway-role.
D. ClearPass is sending the wrong VSA type.
E. The switch is not configured with the port-access role. -
Question 5:
Refer to the exhibit.
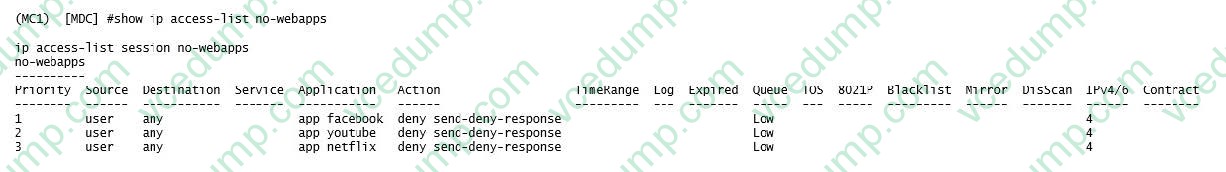
A network administrator completes the initial configuration dialog of the Mobility Controllers (MCs) and they join the Mobility Master (MM) for the first time. After the MM-MC association process, network administrator only creates AP groups, VAPs, and roles. Next, the network administrator proceeds with the configuration of the policies and creates the policy shown in the exhibit.
Which additional steps must be done to make sure this configuration takes effect over the contractor users?
A. Apply the policy in the contractors user role. Enable deep packet inspection. Reload the MCs.
B. Enable firewall visibility. Enable web-content classification. Reload the MCs.
C. Apply the policy in the contractors user role. Enable deep packet inspection.
D. Enable firewall visibility. Enable web-content classification. Reload the MMs. -
Question 6:
Refer to the exhibit.
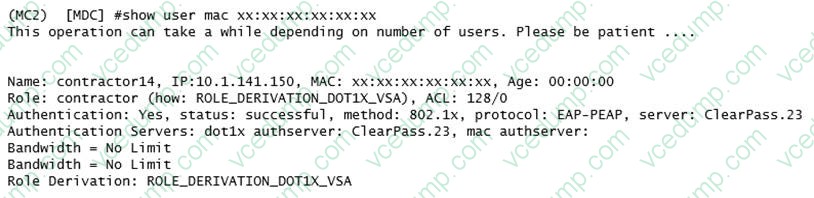
A network administrator is evaluating a deployment to validate that a user is assigned the proper role and reviews the output in the exhibit. How is the role assigned to user?
A. The MC assigned the role based on Aruba VSAs.
B. The MC assigned the machine authentication default user role.
C. The MC assigned the default role based on the authentication method.
D. The MC assigned the role based on server derivation rules. -
Question 7:
A network administrator is in charge of a Mobility Master (MM) ?Mobility Controller (MC) based network security. Recently the Air Monitors detected a Rogue AP in the network and the administrator wants to enable "Tarpit" based wireless containment.
What profile must the administrator enable "tarpit" wireless containment on?
A. IDS Unauthorized device profile
B. IDS profile
C. IDS General profile
D. IDS DOS profile -
Question 8:
Refer to the exhibit.
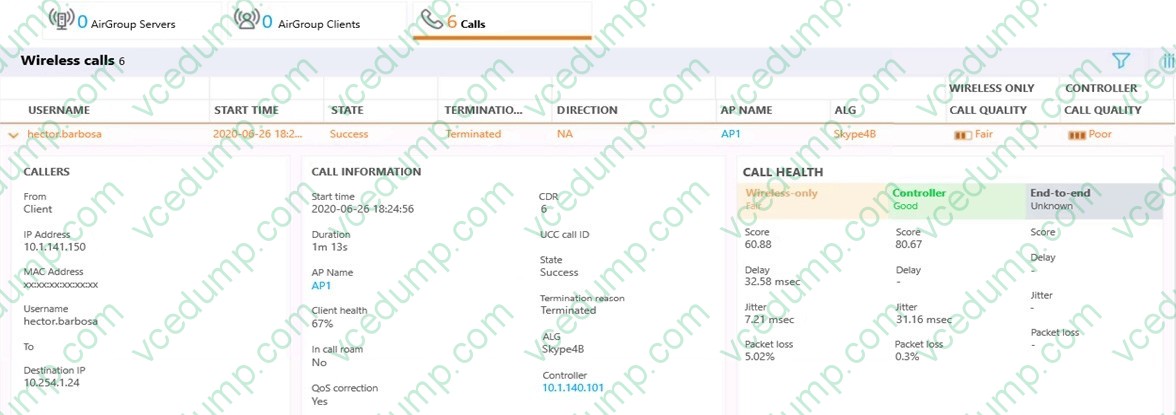
A network administrator has recently enabled WMM on the VAP's SSID profile and enabled UCC Skype4B ALG at the Mobility Master level. During testing, some voice and video conference calls were made, and it was concluded that the call quality has dramatically improved. However, end to end information isn't displayed in the call's details. Also, Skype4B app-sharing's performance is poor at times.
What must the administrator do next in order to enable end to end call visibility and QoS correction to app-sharing service?
A. Deploy the SDN API Software in the Skype4B Solution and point to the MM.
B. Increase the app-sharing DSCP value in the Skype4B ALG profile.
C. Enable UCC monitoring on the "default-controller" mgmt.-server profile.
D. Enable the App-sharing ALG profile at both MM and MD hierarchy levels. -
Question 9:
Refer to the exhibit.
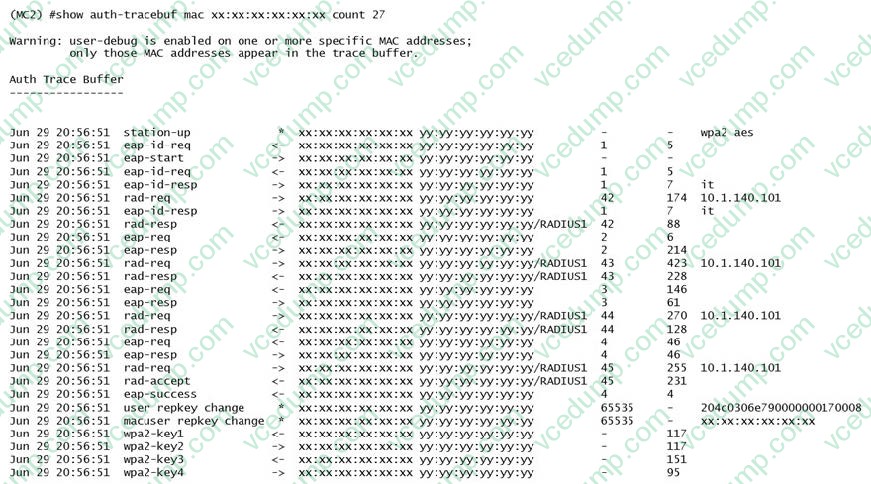
A network administrator is validating client connectivity and executes the show command shown in the exhibit. Which authentication method was used by a wireless station?
A. EAP authentication
B. 802.1X machine authentication
C. MAC authentication
D. 802.1X user authentication -
Question 10:
Refer to the exhibit.
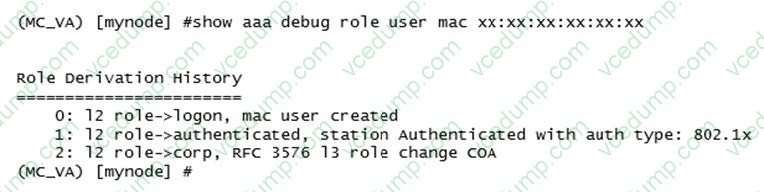
A network administrator has Mobility Master (MM) - Mobility Controller (MC) based network and has fully integrated the MCs with ClearPass for RADIUS-based AAA services. The administrator is testing different ways to run user role derivation.
Based on the show command output, what method has the administrator use for assigning the "corp" role to client with MAC xx:xx:xx:xx:xx:xx?
A. Dynamic Authorization using VSA attributes.
B. Dynamic Authorization using IETF attributes.
C. Server Derivation Rules using IETF attributes.
D. User Derivation Rules using the client's MAC.
Related Exams:
-
HP0-003
HP OpenView Service Desk 5.x -
HP0-045
Supporting the ESL E-Series Lobraries -
HP0-052
Planning and Design of HP 9000/HP Integrity Server Solutions -
HP0-053
Enterprise Integration and Management of HP ProLiant Servers -
HP0-054
Compaq/Oracle 8i I and P with Windows NT -
HP0-055
Implementing HP ProLiant Servers -
HP0-058
Configuration and Management of HP Integrity Mid-Range Servers -
HP0-063
LF PROFESSIONAL COLOR WORKFLOW MANAGEMENT -
HP0-064
HP BladeSystems C-Class Solutions 1 -
HP0-065
Planning and Designing ProLiant Solutions for the Enterprise
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only HP exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your HPE6-A79 exam preparations and HP certification application, do not hesitate to visit our Vcedump.com to find your solutions here.