FCP_FGT_AD-7.6 Exam Details
-
Exam Code
:FCP_FGT_AD-7.6 -
Exam Name
:FortiGate 7.6 Administrator FCP_FGT_AD-7.6 -
Certification
:Fortinet Certifications -
Vendor
:Fortinet -
Total Questions
:99 Q&As -
Last Updated
:Jan 19, 2026
Fortinet FCP_FGT_AD-7.6 Online Questions & Answers
-
Question 1:
Refer to the exhibits.
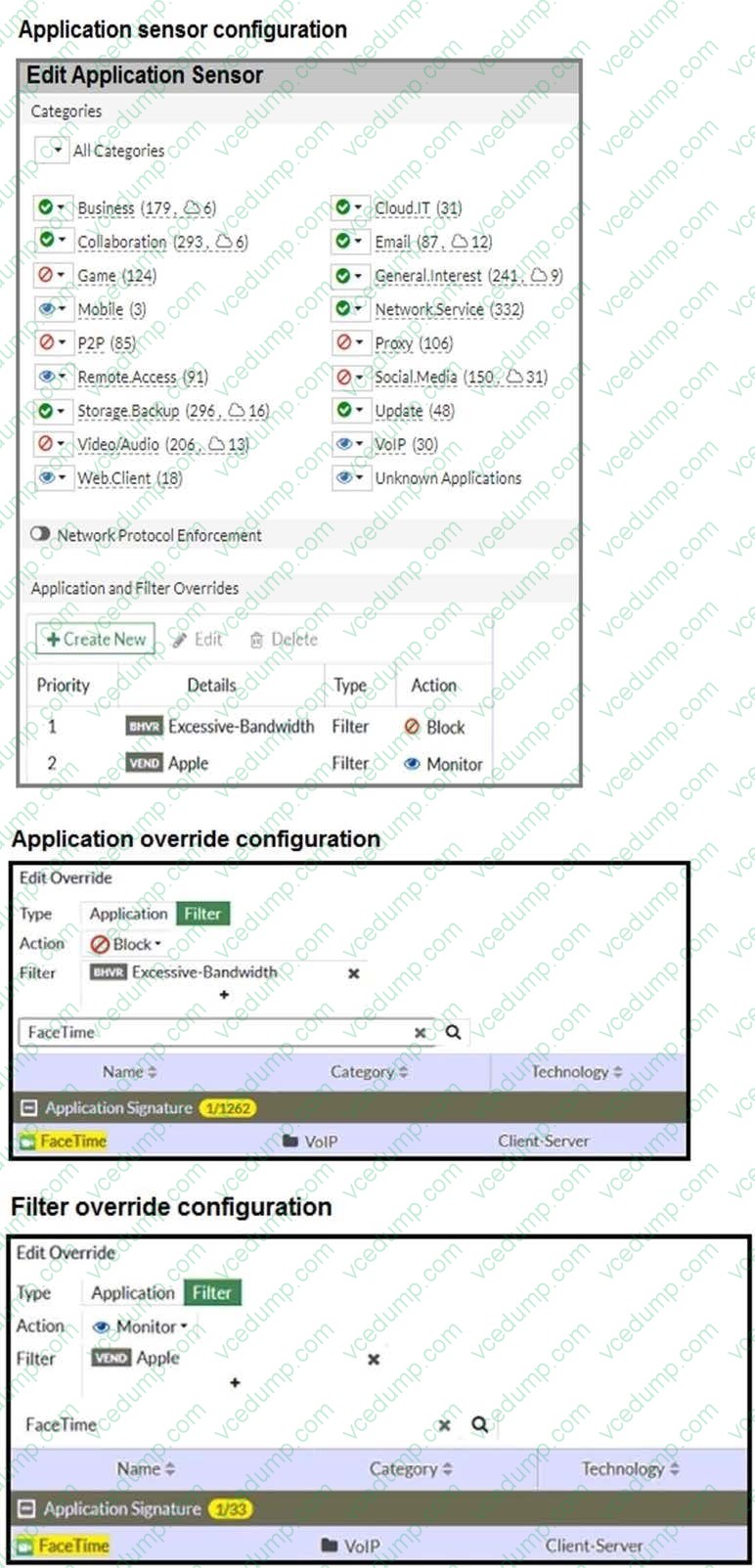
The exhibits show the application sensor configuration and the Excessive-Bandwidth and Apple filter details.
Based on the configuration, what will happen to Apple FaceTime if there are only a few calls originating or incoming?
A. Apple Face Time will be allowed, based on the Video/Audio category configuration.
B. Apple Face Time will be blocked, based on the Excessive-Bandwidth filter configuration.
C. Apple Face Time will be allowed, based on the Apple filter configuration.
D. Apple Face Time will be allowed only if the Apple filter in Application and Filter Overrides is set to Allow. -
Question 2:
You are encountering connectivity problems caused by intermediate devices blocking IPsec traffic. In which two ways can you effectively resolve the problem? (Choose two.)
A. You can use SSL VPN tunnel mode to prevent problems with blocked ESP and UDP ports (500 or 4500).
B. You can configure a hub-and-spoke topology with SSL VPN tunnels to bypass blocked UDP ports.
C. You can turn on fragmentation to fix large certificate negotiation problems.
D. You should use the protocol IKEv2. -
Question 3:
Refer to the exhibits.
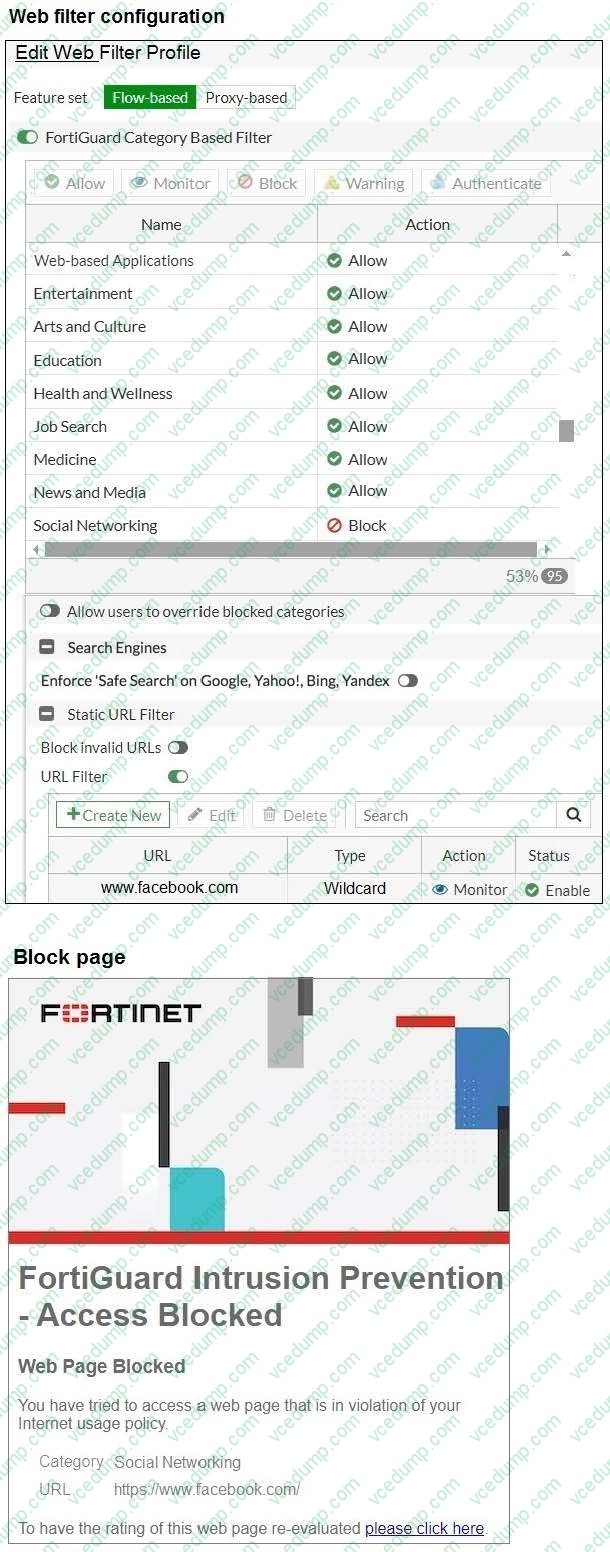
An administrator configured the Web Filter Profile to block access to all social networking sites except Facebook. However, when users try to access Facebook.com, they are redirected to a FortiGuard web filtering block page.
Based on the exhibits, which configuration change must the administrator make to allow Facebook while blocking all other social networking sites?
A. Change the type as Simple in the Static URL Filter section.
B. Set the Social Networking action as warning in the FortiGuard Category Based Filter.
C. Change the Feature set of Web Filter Profile as Proxy-based.
D. Set the Action as Exempt for www.facebook.com in the Static URL Filter. -
Question 4:
Refer to the exhibit.

Which two statements about the FortiGuard connection are true? (Choose two.)
A. FortiGate is using the default port for FortiGuard communication.
B. FortiGate identified the FortiGuard Server using DNS lookup.
C. The weight increases as the number of failed packets rises.
D. You can configure unreliable protocols to communicate with FortiGuard Server. -
Question 5:
Refer to the exhibits.
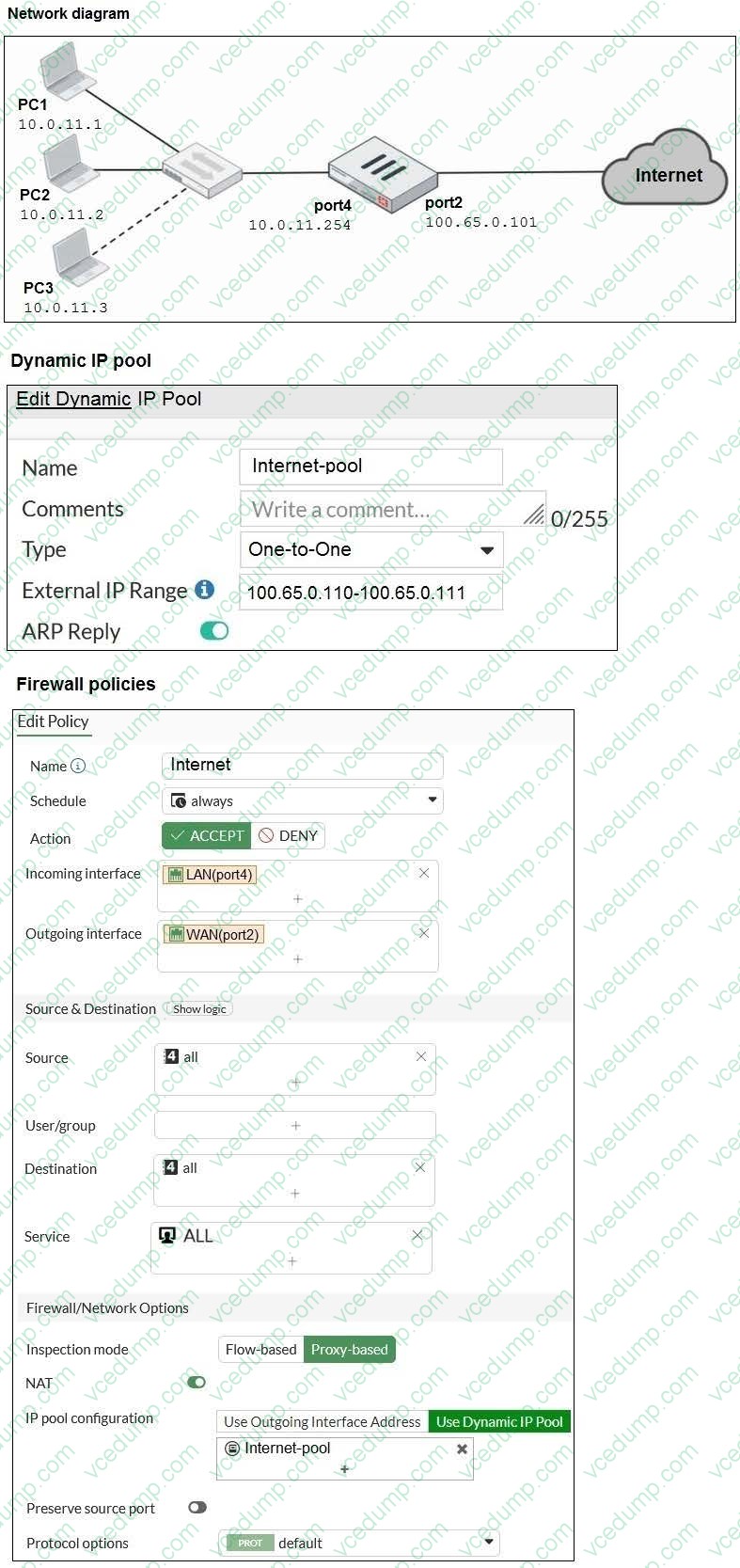
The exhibits show a diagram of a FortiGate device connected to the network, as well as the firewall policy and IP pool configuration on the FortiGate device.
Two PCs, PC1 and PC2, are connected behind FortiGate and can access the internet successfully. However, when the administrator adds a third PC to the network (PC3), the PC cannot connect to the internet.
Based on the information shown in the exhibit, which two configuration options can the administrator use to fix the connectivity issue for PC3? (Choose two.)
A. In the IP pool configuration, set type to overload.
B. In the system settings, set Multiple Interface Policies to enable.
C. In the firewall policy, set match-vip to enable using CLI.
D. In the IP pool configuration, set endip to 100.65.0.112. -
Question 6:
A FortiGate administrator is required to reduce the attack surface on the SSL VPN portal. Which SSL timer can you use to mitigate a denial of service (DoS) attack?
A. SSL VPN http-request-header-timeout
B. SSL VPN dtls-hello-timeout
C. SSL VPN login-timeout
D. SSL VPN idle-timeout -
Question 7:
An administrator has configured the following settings:
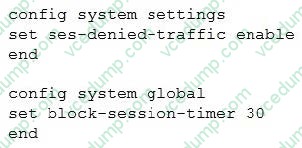
What are the two results of this configuration? (Choose two.)
A. Denied users are blocked for 30 minutes.
B. A session for denied traffic is created.
C. Session helpers are disabled for denied traffic.
D. The number of logs generated by denied traffic is reduced. -
Question 8:
Which two statements about the Security Fabric rating are true? (Choose two.)
A. A license is required to obtain an executive summary in the Security Rating section.
B. The root FortiGate provides executive summaries of all the FortiGate devices in the Security Fabric.
C. The Security Posture category provides PCI compliance results.
D. Security Rating Insights are available only in the Security Rating page. -
Question 9:
Refer to the exhibits.
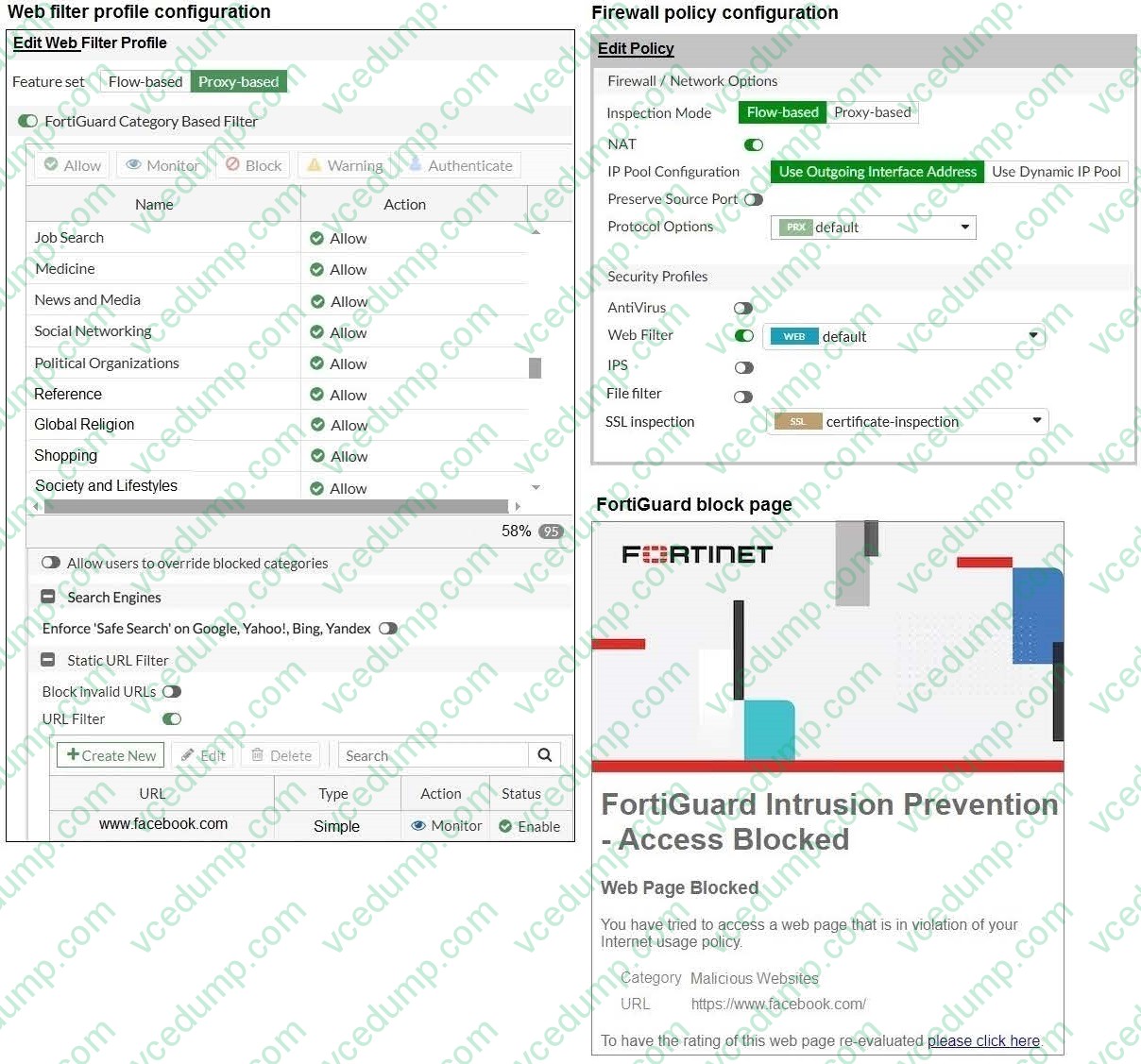
A web filter profile configuration and firewall policy configuration are shown. You are trying to access www.facebook.com, but you are redirected to a FortiGuard web filtering block page. Based on the exhibits, what is the possible cause of the issue?
A. The web filter profile feature set is configured incorrectly.
B. The web rating override configuration is incorrect.
C. The firewall policy inspection mode is incorrect.
D. For www.facebook.com, the URL filter action is incorrect. -
Question 10:
Refer to the exhibits.
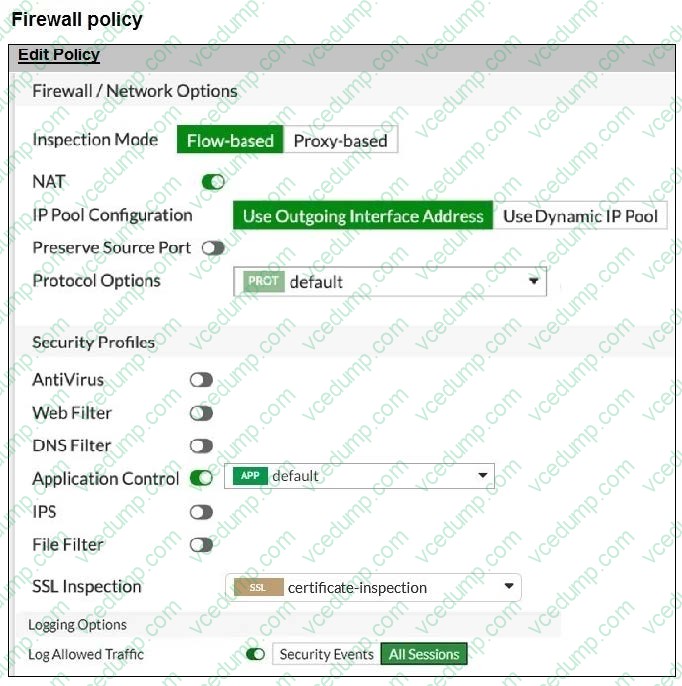
You have implemented the application sensor and the corresponding firewall policy as shown in the exhibits.
You cannot access any of the Google applications, but you are able to access www.fortinet.com.
What would you do to resolve this issue?
A. Change the Inspection mode to Proxy-based.
B. Set SSL inspection to deep-content-inspection.
C. Move up Google in the Application and Filter Overrides section to set its priority to 1.
D. Add *Google*.com to the URL category in the security profile.
Related Exams:
-
EMEA-ADVANCED-SUPPORT
Fortinet EMEA Advanced Support -
FCP_FAC_AD-6.5
FCP - FortiAuthenticator 6.5 Administrator -
FCP_FAZ_AD-7.4
FCP - FortiAnalyzer 7.4 Administrator -
FCP_FAZ_AN-7.4
FCP - FortiAnalyzer 7.4 Analyst -
FCP_FCT_AD-7.2
FCP - Forti Client EMS 7.2 Administrator -
FCP_FGT_AD-7.4
FCP - FortiGate 7.4 Administrator -
FCP_FGT_AD-7.6
FortiGate 7.6 Administrator FCP_FGT_AD-7.6 -
FCP_FMG_AD-7.4
FCP - FortiManager 7.4 Administrator -
FCP_FMG_AD-7.6
FortiManager 7.6 Administrator -
FCP_FML_AD-7.4
FCP - FortiMail 7.4 Administrator
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Fortinet exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your FCP_FGT_AD-7.6 exam preparations and Fortinet certification application, do not hesitate to visit our Vcedump.com to find your solutions here.