Exam Details
Exam Code
:CKSExam Name
:Linux Foundation Certified Kubernetes Security Specialist (CKS)Certification
:Linux Foundation CertificationsVendor
:Linux FoundationTotal Questions
:46 Q&AsLast Updated
:Jul 17, 2025
Linux Foundation Linux Foundation Certifications CKS Questions & Answers
-
Question 31:

You can switch the cluster/configuration context using the following command:
[desk@cli] $ kubectl config use-context stage
Context:
A PodSecurityPolicy shall prevent the creation of privileged Pods in a specific namespace.
Task:
1.
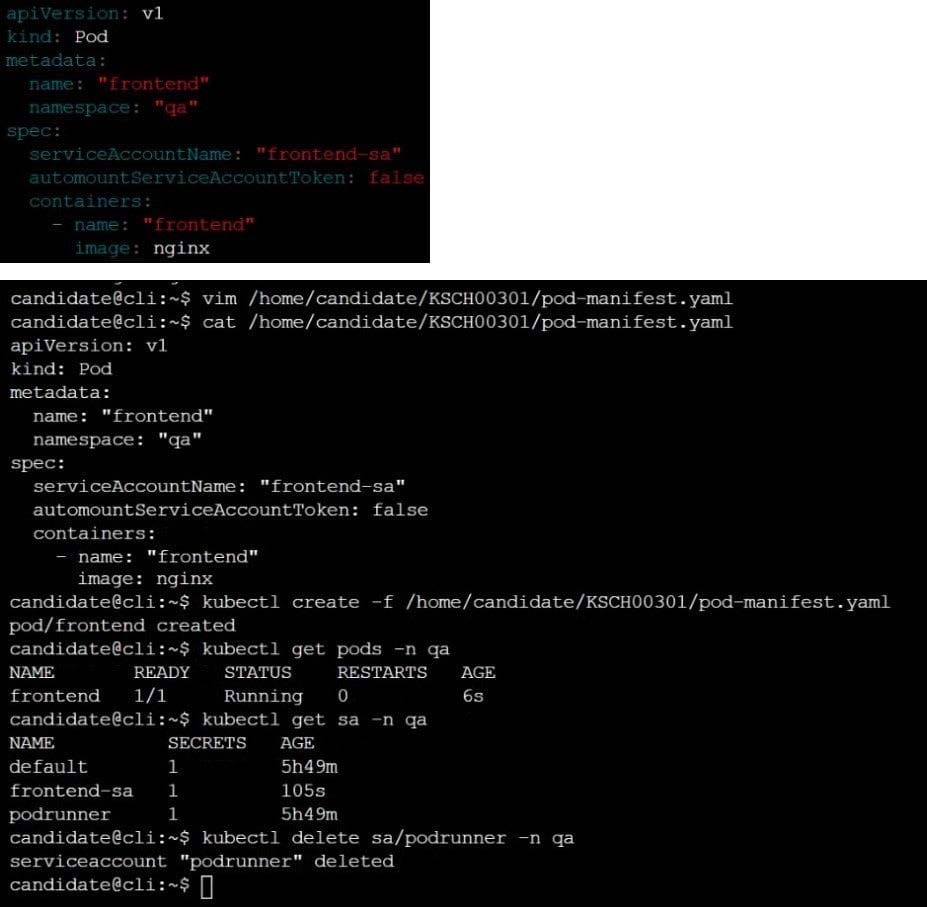
Create a new PodSecurityPolcy named deny-policy, which prevents the creation of privileged Pods.
2.
Create a new ClusterRole name deny-access-role, which uses the newly created PodSecurityPolicy deny-policy.
3.
Create a new ServiceAccount named psd-denial-sa in the existing namespace development.
Finally, create a new ClusterRoleBindind named restrict-access-bind, which binds the newly created ClusterRole deny-access-role to the newly created ServiceAccount psp-denial-sa
A. See the explanation below
B. PlaceHolder
-
Question 32:
Enable audit logs in the cluster, To Do so, enable the log backend, and ensure that
1.
logs are stored at /var/log/kubernetes/kubernetes-logs.txt.
2.
Log files are retained for 5 days.
3.
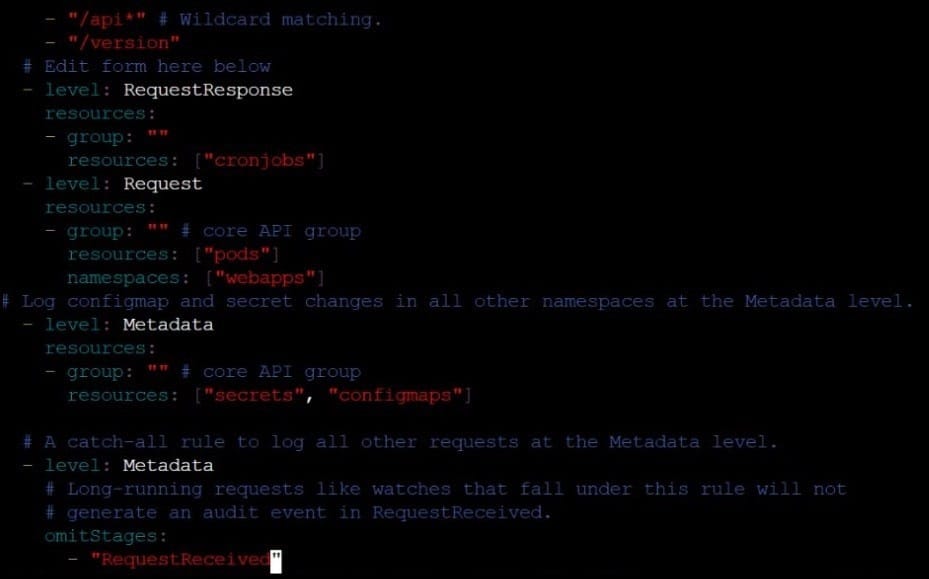
at maximum, a number of 10 old audit logs files are retained. Edit and extend the basic policy to log:
1.
Cronjobs changes at RequestResponse
2.
Log the request body of deployments changes in the namespace kube-system.
3.
Log all other resources in core and extensions at the Request level.
4.
Don't log watch requests by the "system:kube-proxy" on endpoints or
A. See explanation below.
B. PlaceHolder
-
Question 33:


You can switch the cluster/configuration context using the following command:
[desk@cli] $ kubectl config use-context dev
Context:
A CIS Benchmark tool was run against the kubeadm created cluster and found multiple issues that must be addressed.
Task:
Fix all issues via configuration and restart the affected components to ensure the new settings take effect.
Fix all of the following violations that were found against the API server:
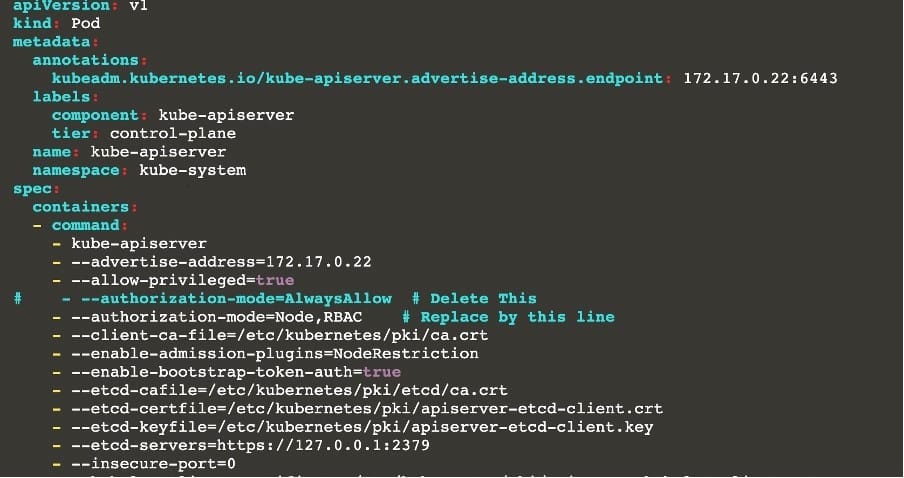
1.2.7 authorization-mode argument is not set to AlwaysAllow FAIL
1.2.8 authorization-mode argument includes Node FAIL
1.2.7 authorization-mode argument includes RBAC FAIL
Fix all of the following violations that were found against the Kubelet:
4.2.1 Ensure that the anonymous-auth argument is set to false FAIL
4.2.2 authorization-mode argument is not set to AlwaysAllow FAIL (Use Webhook autumn/authz where possible)
Fix all of the following violations that were found against etcd:
2.2 Ensure that the client-cert-auth argument is set to true
A. See the explanation below
B. PlaceHolder
-
Question 34:
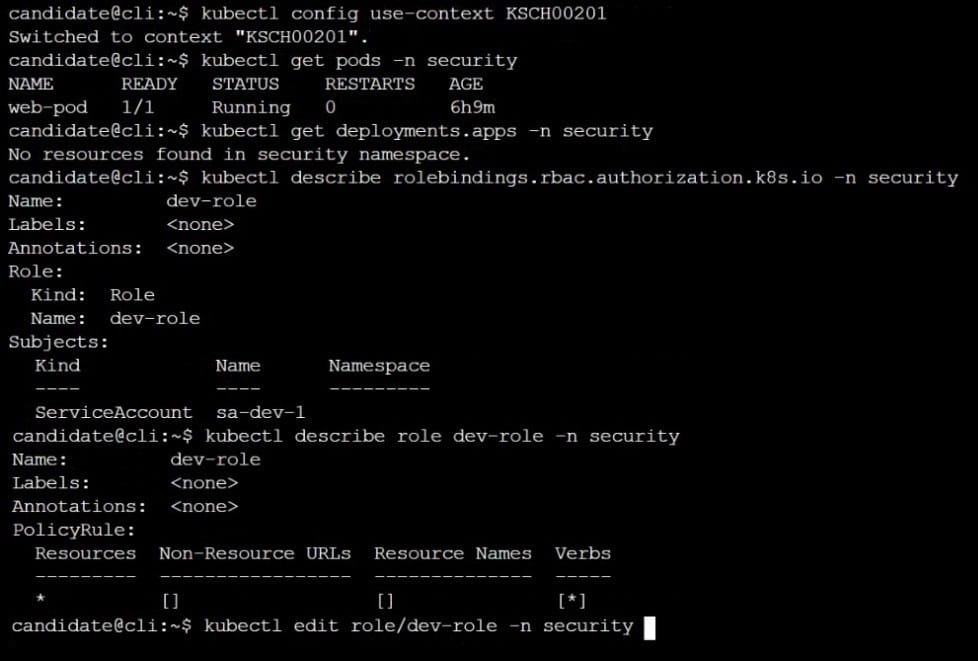
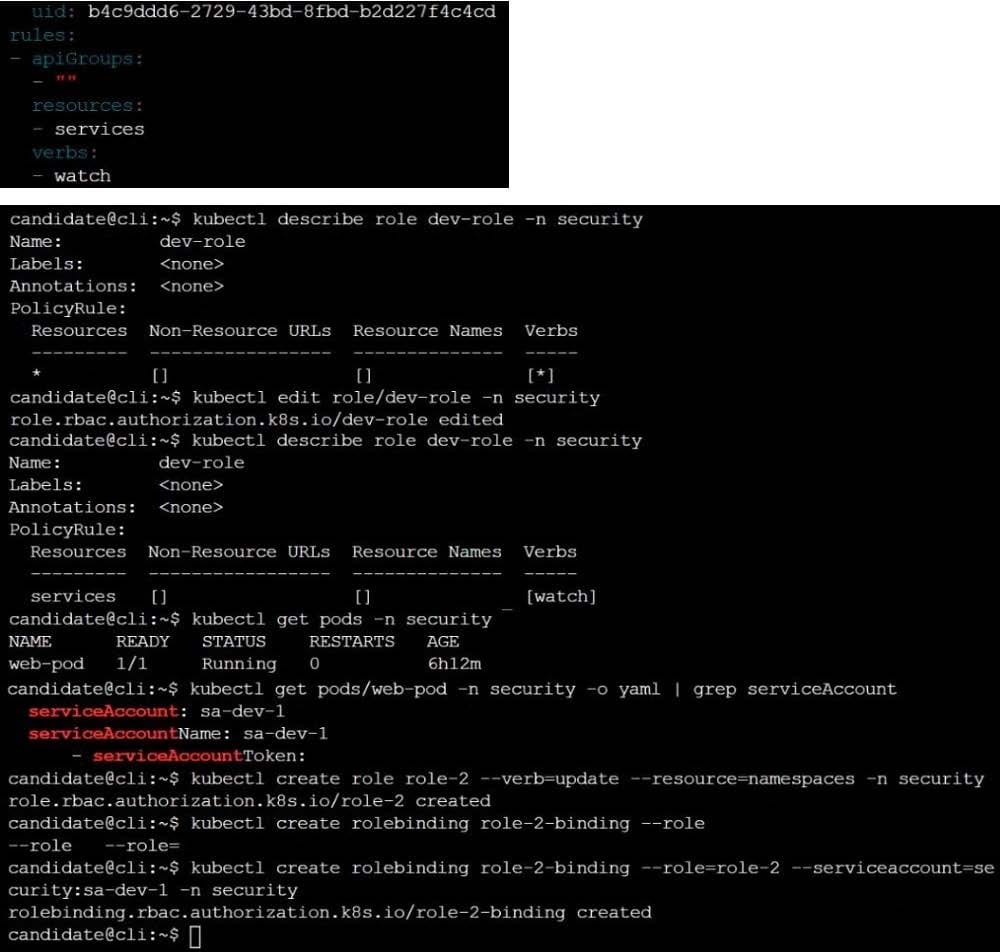
A Role bound to a Pod's ServiceAccount grants overly permissive permissions. Complete the following tasks to reduce the set of permissions.
Task
Given an existing Pod named web-pod running in the namespace security.
Edit the existing Role bound to the Pod's ServiceAccount sa-dev-1 to only allow performing watch operations, only on resources of type services.
Create a new Role named role-2 in the namespace security, which only allows performing update
operations, only on resources of type namespaces.
Create a new RoleBinding named role-2-binding binding the newly created Role to the Pod's ServiceAccount.

A. See the explanation below
B. PlaceHolder
-
Question 35:
Analyze and edit the given Dockerfile
1.
FROM ubuntu:latest
2.
RUN apt-get update -y
3.
RUN apt-install nginx -y
4.
COPY entrypoint.sh /
5.
ENTRYPOINT ["/entrypoint.sh"]
6.
USER ROOT
Fixing two instructions present in the file being prominent security best practice issues
Analyze and edit the deployment manifest file
1.
apiVersion: v1
2.
kind: Pod
3.
metadata:
4.
name: security-context-demo-2
5.
spec:
6.
securityContext:
7.
runAsUser: 1000
8.
containers:
9.
- name: sec-ctx-demo-2 10.image: gcr.io/google-samples/node-hello:1.0 11.securityContext: 12.runAsUser: 0 13.privileged: True 14.allowPrivilegeEscalation: false
Fixing two fields present in the file being prominent security best practice issues
Don't add or remove configuration settings; only modify the existing configuration settings
Whenever you need an unprivileged user for any of the tasks, use user test-user with the user id 5487
A. See the explanation below:
B. PlaceHolder
-
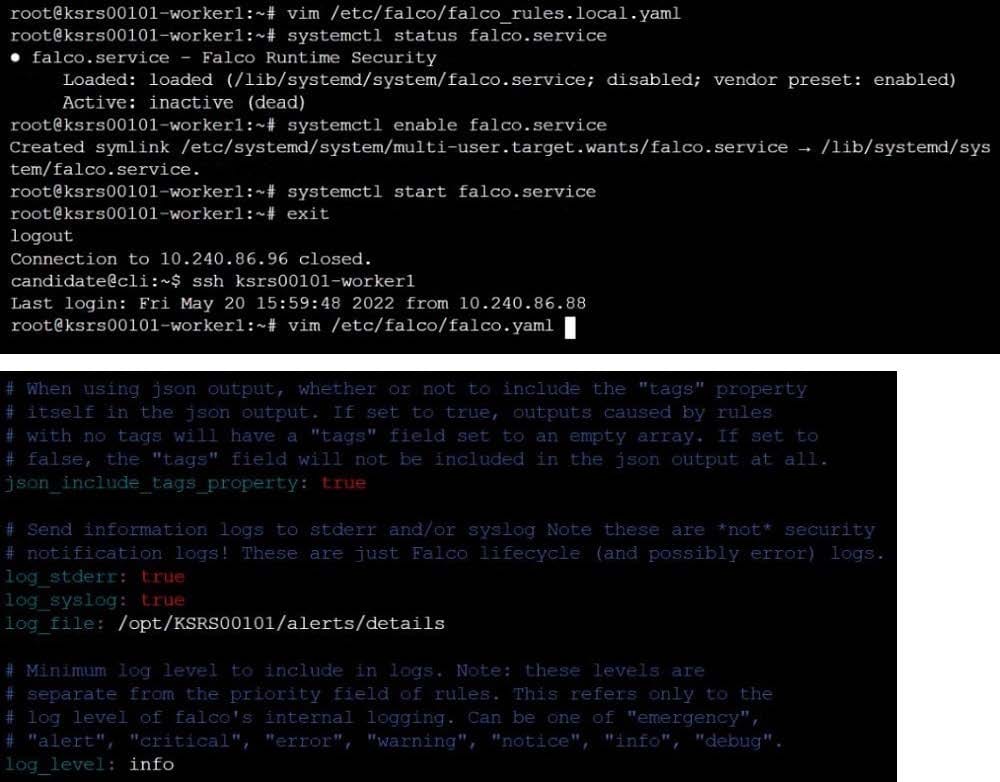
Question 36:
CORRECT TEXT
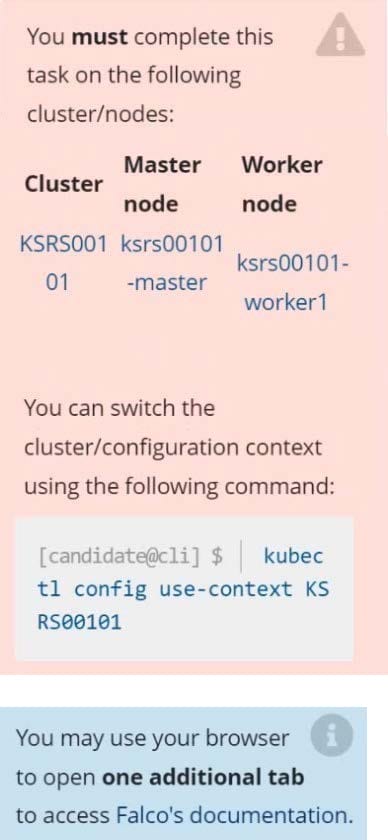
Two tools are pre-installed on the cluster's worker node:
1.
sysdig
2.
falco
Using the tool of your choice (including any non pre-installed tool), analyze the container's behavior for at least 30 seconds, using filters that detect newly spawning and executing processes. Store an incident file at /opt/KSRS00101/alerts/
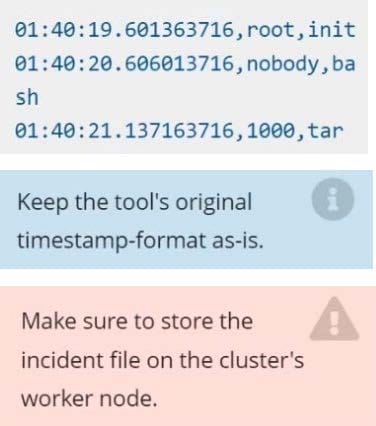
details, containing the detected incidents, one per line, in the following format:

The following example shows a properly formatted incident file:
A. See the explanation below:
B. PlaceHolder
-
Question 37:
Use the kubesec docker images to scan the given YAML manifest, edit and apply the advised changes, and passed with a score of 4 points.
kubesec-test.yaml
1.
apiVersion: v1
2.
kind: Pod
3.
metadata:
4.
name: kubesec-demo
5.
spec:
6.
containers:
7.
- name: kubesec-demo
8.
image: gcr.io/google-samples/node-hello:1.0
9.
securityContext: 10.readOnlyRootFilesystem: true
Hint: docker run -i kubesec/kubesec:512c5e0 scan /dev/stdin < kubesec-test.yaml
A. See explanation below.
B. PlaceHolder
-
Question 38:
Create a User named john, create the CSR Request, fetch the certificate of the user after approving it.
Create a Role name john-role to list secrets, pods in namespace john
Finally, Create a RoleBinding named john-role-binding to attach the newly created role john-role to the user john in the namespace john.
To Verify: Use the kubectl auth CLI command to verify the permissions.
A. See the below.
B. PlaceHolder
-
Question 39:
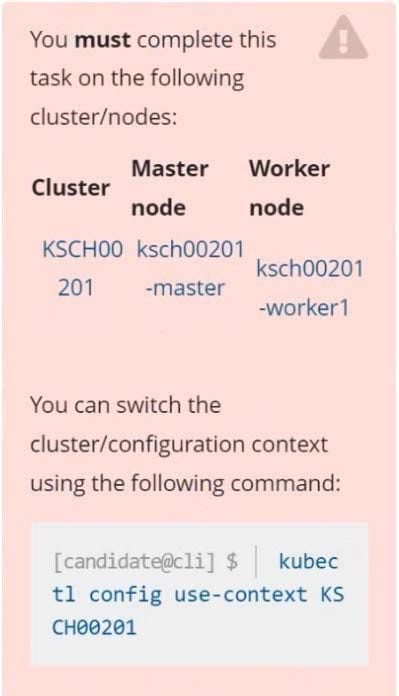
You must complete this task on the following cluster/nodes:
Cluster: trace Master node: master Worker node: worker1
You can switch the cluster/configuration context using the following command:
[desk@cli] $ kubectl config use-context trace
Given: You may use Sysdig or Falco documentation.
Task:
Use detection tools to detect anomalies like processes spawning and executing something weird frequently in the single container belonging to Pod tomcat.
Two tools are available to use:
1.
falco
2.
sysdig
Tools are pre-installed on the worker1 node only.
Analyse the container's behaviour for at least 40 seconds, using filters that detect newly spawning and executing processes.
Store an incident file at /home/cert_masters/report, in the following format:
[timestamp],[uid],[processName]
Note: Make sure to store incident file on the cluster's worker node, don't move it to master node.
A. See the explanation below
B. PlaceHolder
-
Question 40:
Create a RuntimeClass named untrusted using the prepared runtime handler named runsc.
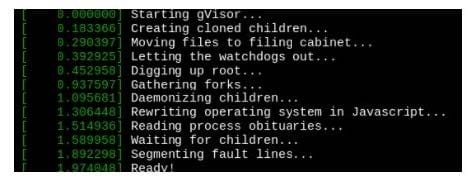
Create a Pods of image alpine:3.13.2 in the Namespace default to run on the gVisor runtime class.
A. See the explanation below:
B. PlaceHolder
Related Exams:
CKA
Linux Foundation Certified Kubernetes Administrator (CKA)CKAD
Linux Foundation Certified Kubernetes Application Developer (CKAD)CKS
Linux Foundation Certified Kubernetes Security Specialist (CKS)HFCP
Linux Foundation Certified Hyperledger Fabric Certified Practitioner (HFCP)KCNA
Linux Foundation Certified Kubernetes and Cloud Native Associate (KCNA)LFCA
Linux Foundation Certified IT Associate (LFCA)LFCS
Linux Foundation Certified System Administrator (LFCS)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Linux Foundation exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CKS exam preparations and Linux Foundation certification application, do not hesitate to visit our Vcedump.com to find your solutions here.