Exam Details
Exam Code
:CKSExam Name
:Linux Foundation Certified Kubernetes Security Specialist (CKS)Certification
:Linux Foundation CertificationsVendor
:Linux FoundationTotal Questions
:46 Q&AsLast Updated
:Jul 09, 2025
Linux Foundation Linux Foundation Certifications CKS Questions & Answers
-
Question 11:
Create a new NetworkPolicy named deny-all in the namespace testing which denies all traffic of type ingress and egress traffic
A. See the explanation below:
B. PlaceHolder
-
Question 12:
CORRECT TEXT
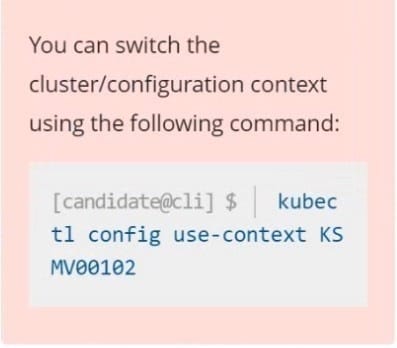
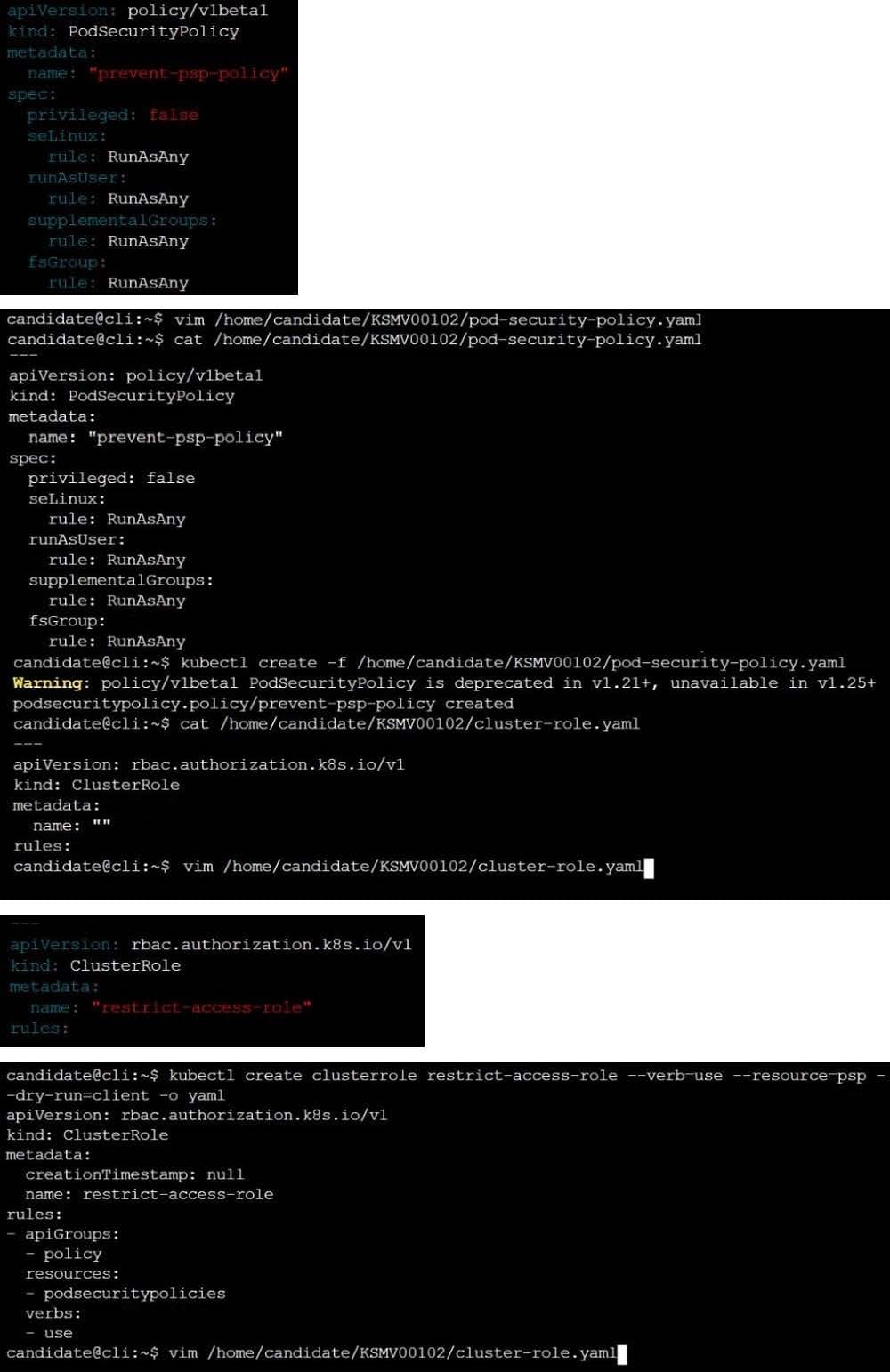
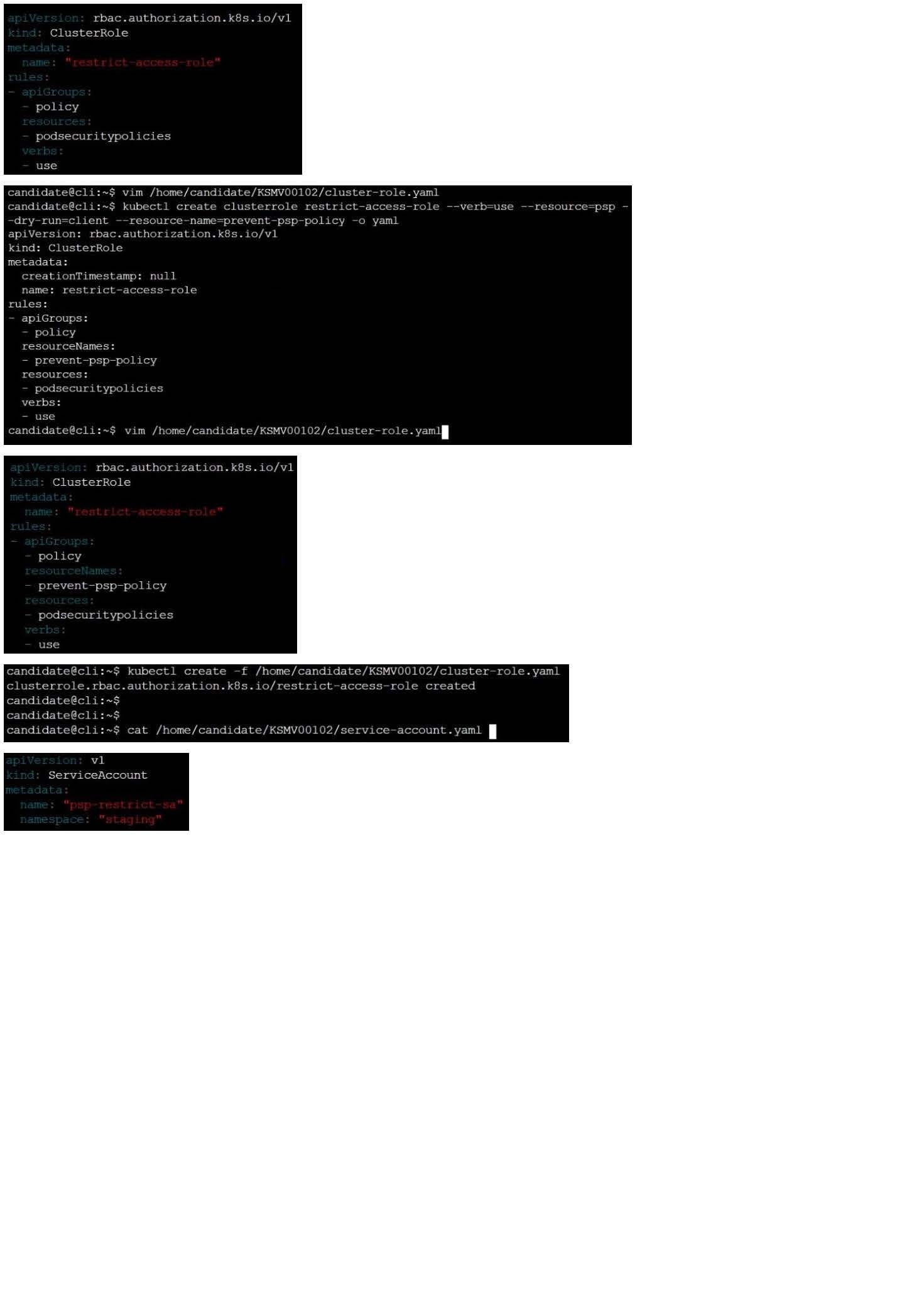
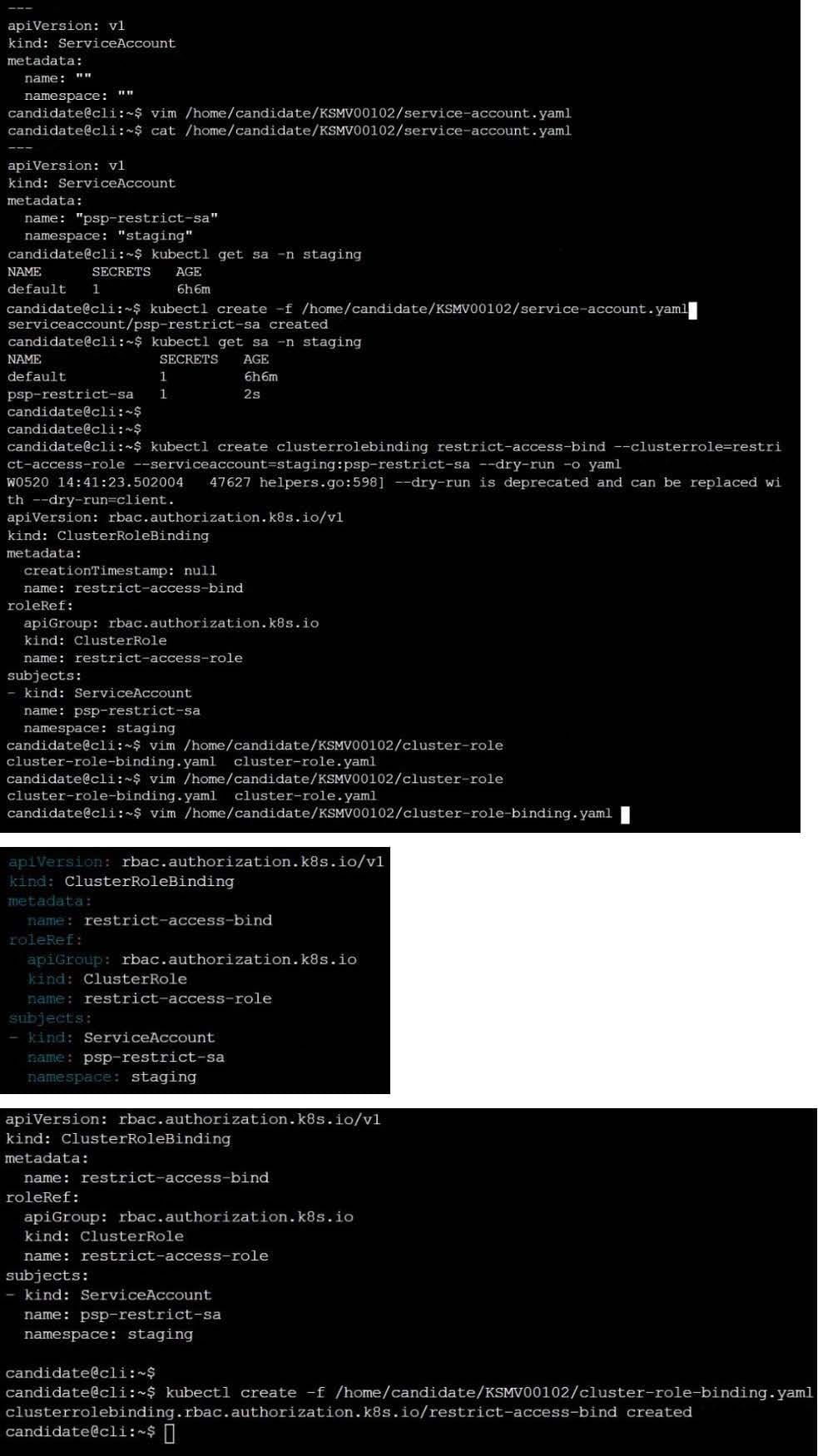
A PodSecurityPolicy shall prevent the creation of privileged Pods in a specific namespace.
Task
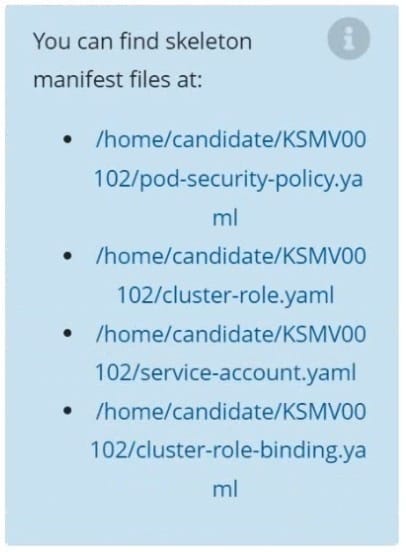
Create a new PodSecurityPolicy named prevent-psp-policy,which prevents the creation of privileged Pods.
Create a new ClusterRole named restrict-access-role, which uses the newly created PodSecurityPolicy prevent-psp-policy.
Create a new ServiceAccount named psp-restrict-sa in the existing namespace staging.
Finally, create a new ClusterRoleBinding named restrict-access-bind, which binds the newly created ClusterRole restrict-access-role to the newly created ServiceAccount psp- restrict-sa.
A. See explanation below.
B. PlaceHolder
-
Question 13:
Context:
Cluster: prod
Master node: master1
Worker node: worker1
You can switch the cluster/configuration context using the following command:
[desk@cli] $ kubectl config use-context prod
Task:
Analyse and edit the given Dockerfile (based on the ubuntu:18:04 image)
/home/cert_masters/Dockerfile fixing two instructions present in the file being prominent security/best-practice issues.
Analyse and edit the given manifest file
/home/cert_masters/mydeployment.yaml fixing two fields present in the file being prominent security/best-practice issues.
Note: Don't add or remove configuration settings; only modify the existing configuration settings, so that two configuration settings each are no longer security/best-practice concerns.
Should you need an unprivileged user for any of the tasks, use user nobody with user id 65535
A. See the explanation below
B. PlaceHolder
-
Question 14:
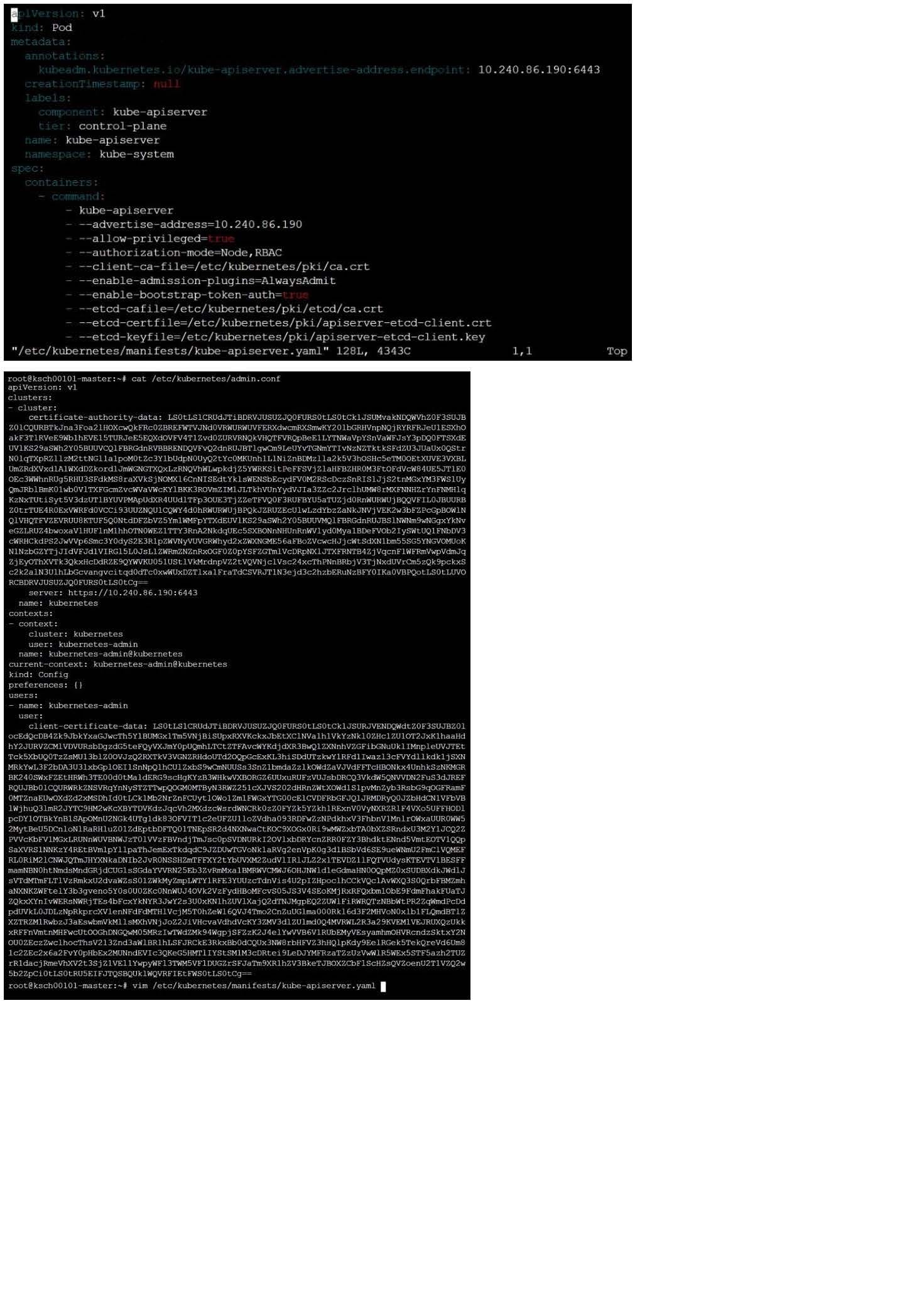
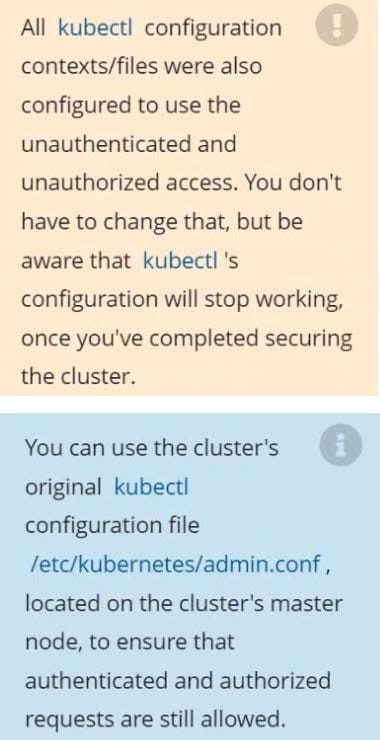
The kubeadm-created cluster's Kubernetes API server was, for testing purposes, temporarily configured to allow unauthenticated and unauthorized access granting the anonymous user duster-admin access.

Task
Reconfigure the cluster's Kubernetes API server to ensure that only authenticated and authorized REST requests are allowed.
Use authorization mode Node,RBAC and admission controller NodeRestriction.
Cleaning up, remove the ClusterRoleBinding for user system:anonymous.
A. See explanation below.
B. PlaceHolder
-
Question 15:
Cluster: qa-cluster
Master node: master Worker node: worker1 You can switch the cluster/configuration context using the following command: [desk@cli] $ kubectl config use-context qa-cluster
Task:
Create a NetworkPolicy named restricted-policy to restrict access to Pod product running in namespace dev.
Only allow the following Pods to connect to Pod products-service:
1.
Pods in the namespace qa
2.
Pods with label environment: stage, in any namespace
A. See the below.
B. PlaceHolder
-
Question 16:

1.
Retrieve the content of the existing secret named default-token-xxxxx in the testing namespace.
Store the value of the token in the token.txt
2.
Create a new secret named test-db-secret in the DB namespace with the following content:
username: mysql password: password@123
Create the Pod name test-db-pod of image nginx in the namespace db that can access test-db-secret via a volume at path /etc/mysql-credentials
A. See the explanation below:
B. PlaceHolder
-
Question 17:
You can switch the cluster/configuration context using the following command:
[desk@cli] $ kubectl config use-context prod-account
Context:
A Role bound to a Pod's ServiceAccount grants overly permissive permissions. Complete the following tasks to reduce the set of permissions.
Task:
Given an existing Pod named web-pod running in the namespace database.
1.
Edit the existing Role bound to the Pod's ServiceAccount test-sa to only allow performing get operations, only on resources of type Pods.
2.
Create a new Role named test-role-2 in the namespace database, which only allows performing update operations, only on resources of type statuefulsets.
3.
Create a new RoleBinding named test-role-2-bind binding the newly created Role to the Pod's ServiceAccount. Note: Don't delete the existing RoleBinding.
A. See the explanation below
B. PlaceHolder
-
Question 18:
Given an existing Pod named nginx-pod running in the namespace test-system, fetch the service-account-name used and put the content in /candidate/KSC00124.txt
Create a new Role named dev-test-role in the namespace test-system, which can perform update operations, on resources of type namespaces.
Create a new RoleBinding named dev-test-role-binding, which binds the newly created Role to the Pod's ServiceAccount ( found in the Nginx pod running in namespace test- system).
A. See explanation below.
B. PlaceHolder
-
Question 19:
Create a PSP that will prevent the creation of privileged pods in the namespace.
Create a new PodSecurityPolicy named prevent-privileged-policy which prevents the creation of privileged pods.
Create a new ServiceAccount named psp-sa in the namespace default.
Create a new ClusterRole named prevent-role, which uses the newly created Pod Security Policy prevent-privileged-policy.
Create a new ClusterRoleBinding named prevent-role-binding, which binds the created ClusterRole prevent-role to the created SA psp-sa.
Also, Check the Configuration is working or not by trying to Create a Privileged pod, it should get failed.
A. See the below.
B. PlaceHolder
-
Question 20:
Cluster: scanner
Master node: controlplane
Worker node: worker1
You can switch the cluster/configuration context using the following command:
[desk@cli] $ kubectl config use-context scanner
Given:
You may use Trivy's documentation.
Task:
Use the Trivy open-source container scanner to detect images with severe vulnerabilities used by Pods in the namespace nato.
Look for images with High or Critical severity vulnerabilities and delete the Pods that use those images.
Trivy is pre-installed on the cluster's master node. Use cluster's master node to use Trivy.
A. See the explanation below
B. PlaceHolder
Related Exams:
CKA
Linux Foundation Certified Kubernetes Administrator (CKA)CKAD
Linux Foundation Certified Kubernetes Application Developer (CKAD)CKS
Linux Foundation Certified Kubernetes Security Specialist (CKS)HFCP
Linux Foundation Certified Hyperledger Fabric Certified Practitioner (HFCP)KCNA
Linux Foundation Certified Kubernetes and Cloud Native Associate (KCNA)LFCA
Linux Foundation Certified IT Associate (LFCA)LFCS
Linux Foundation Certified System Administrator (LFCS)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Linux Foundation exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CKS exam preparations and Linux Foundation certification application, do not hesitate to visit our Vcedump.com to find your solutions here.