Exam Details
Exam Code
:412-79V10Exam Name
:EC-Council Certified Security Analyst (ECSA) V10Certification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:201 Q&AsLast Updated
:Jun 27, 2025
EC-COUNCIL EC-COUNCIL Certifications 412-79V10 Questions & Answers
-
Question 31:
Before performing the penetration testing, there will be a pre-contract discussion with different pen-testers (the team of penetration testers) to gather a quotation to perform pen testing.

Which of the following factors is NOT considered while preparing a price quote to perform pen testing?
A. Total number of employees in the client organization
B. Type of testers involved
C. The budget required
D. Expected time required to finish the project
-
Question 32:
Passwords protect computer resources and files from unauthorized access by malicious users. Using passwords is the most capable and effective way to protect information and to increase the security level of a company.
Password cracking is the process of recovering passwords from data that have been stored in or transmitted by a computer system to gain unauthorized access to a system.
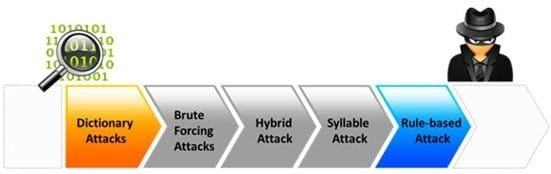
Which of the following password cracking attacks tries every combination of characters until the password is broken?
A. Brute-force attack
B. Rule-based attack
C. Hybrid attack
D. Dictionary attack
-
Question 33:
Firewall is an IP packet filter that enforces the filtering and security policies to the flowing network traffic. Using firewalls in IPv6 is still the best way of protection from low level attacks at the network and transport layers. Which one of the following cannot handle routing protocols properly?
A. "Internet-router-firewall-net architecture"
B. "Internet-firewall-router-net architecture"
C. "Internet-firewall/router(edge device)-net architecture"
D. "Internet-firewall -net architecture"
-
Question 34:
Which of the following statements is true about the LM hash?
A. Disabled in Windows Vista and 7 OSs
B. Separated into two 8-character strings
C. Letters are converted to the lowercase
D. Padded with NULL to 16 characters
-
Question 35:
In Linux, /etc/shadow file stores the real password in encrypted format for user's account with added properties associated with the user's password.
In the example of a /etc/shadow file below, what does the bold letter string indicate? Vivek: $1$fnffc$GteyHdicpGOfffXX40w#5:13064:0:99999:7
A. Number of days the user is warned before the expiration date
B. Minimum number of days required between password changes
C. Maximum number of days the password is valid
D. Last password changed
-
Question 36:
Which of the following is not a condition specified by Hamel and Prahalad (1990)?
A. Core competency should be aimed at protecting company interests
B. Core competency is hard for competitors to imitate
C. Core competency provides customer benefits
D. Core competency can be leveraged widely to many products and markets
-
Question 37:
How many possible sequence number combinations are there in TCP/IP protocol?
A. 320 billion
B. 32 million
C. 4 billion
D. 1 billion
-
Question 38:
What threat categories should you use to prioritize vulnerabilities detected in the pen testing report?
A. 1, 2, 3, 4, 5
B. Low, medium, high, serious, critical
C. Urgent, dispute, action, zero, low
D. A, b, c, d, e
-
Question 39:
Phishing is typically carried out by email spoofing or instant messaging and it often directs users to enter details at a fake website whose look and feel are almost identical to the legitimate one.
Phishing is an example of social engineering techniques used to deceive users, and exploits the poor usability of current web security technologies. Attempts to deal with the growing number of reported phishing incidents include legislation, user training, public awareness, and technical security measures.
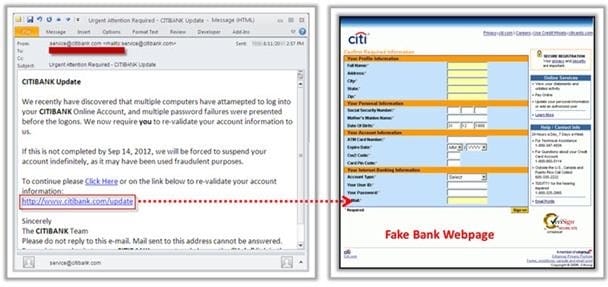
What characteristics do phishing messages often have that may make them identifiable?
A. Invalid email signatures or contact information
B. Suspiciously good grammar and capitalization
C. They trigger warning pop-ups
D. Suspicious attachments
-
Question 40:
Which one of the following 802.11 types uses either FHSS or DSSS for modulation?
A. 802.11b
B. 802.11a
C. 802.11n
D. 802.11-Legacy
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-055
Sun Certified Programmer for the Java 2 Platform.SE 5.0212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 412-79V10 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.