Exam Details
Exam Code
:412-79V10Exam Name
:EC-Council Certified Security Analyst (ECSA) V10Certification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:201 Q&AsLast Updated
:Jun 27, 2025
EC-COUNCIL EC-COUNCIL Certifications 412-79V10 Questions & Answers
-
Question 11:
Identify the injection attack represented in the diagram below: A. XPath Injection Attack
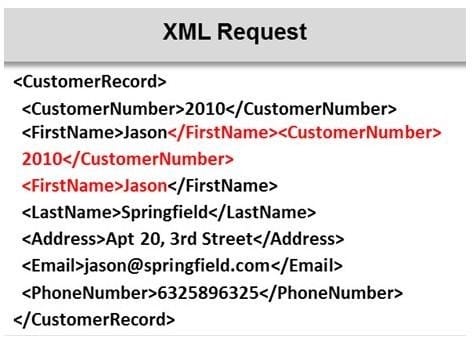
B. XML Request Attack
C. XML Injection Attack
D. Frame Injection Attack
-
Question 12:
Which of the following is not a characteristic of a firewall?
A. Manages public access to private networked resources
B. Routes packets between the networks
C. Examines all traffic routed between the two networks to see if it meets certain criteria
D. Filters only inbound traffic but not outbound traffic
-
Question 13:
What is the difference between penetration testing and vulnerability testing?
A. Penetration testing goes one step further than vulnerability testing; while vulnerability tests check for known vulnerabilities, penetration testing adopts the concept of `in-depth ethical hacking'
B. Penetration testing is based on purely online vulnerability analysis while vulnerability testing engages ethical hackers to find vulnerabilities
C. Vulnerability testing is more expensive than penetration testing
D. Penetration testing is conducted purely for meeting compliance standards while vulnerability testing is focused on online scans
-
Question 14:
DNS information records provide important data about:
A. Phone and Fax Numbers
B. Location and Type of Servers
C. Agents Providing Service to Company Staff
D. New Customer
-
Question 15:
Identify the person who will lead the penetration-testing project and be the client point of contact.
A. Database Penetration Tester
B. Policy Penetration Tester
C. Chief Penetration Tester
D. Application Penetration Tester
-
Question 16:
Variables are used to define parameters for detection, specifically those of your local network and/or specific servers or ports for inclusion or exclusion in rules. These are simple substitution variables set with the var keyword. Which one of the following operator is used to define meta-variables?
A. "$"
B. "#"
C. "*"
D. "?"
-
Question 17:
Attackers create secret accounts and gain illegal access to resources using backdoor while bypassing the authentication procedures. Creating a backdoor is a where an attacker obtains remote access to a computer on a network.
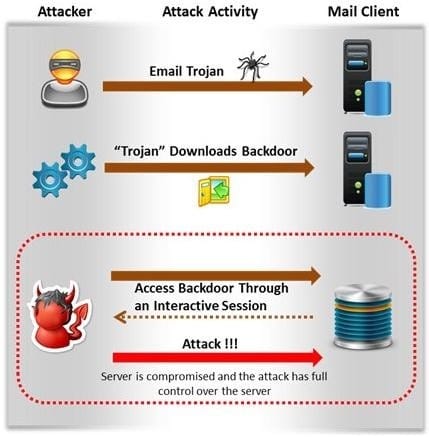
Which of the following techniques do attackers use to create backdoors to covertly gather critical information about a target machine?
A. Internal network mapping to map the internal network of the target machine
B. Port scanning to determine what ports are open or in use on the target machine
C. Sniffing to monitor all the incoming and outgoing network traffic
D. Social engineering and spear phishing attacks to install malicious programs on the target machine
-
Question 18:
Which of the following protocol's traffic is captured by using the filter tcp.port==3389 in the Wireshark tool?
A. Reverse Gossip Transport Protocol (RGTP)
B. Real-time Transport Protocol (RTP)
C. Remote Desktop Protocol (RDP)
D. Session Initiation Protocol (SIP)
-
Question 19:
Which of the following information gathering techniques collects information from an organization's web-based calendar and email services?
A. Anonymous Information Gathering
B. Private Information Gathering
C. Passive Information Gathering
D. Active Information Gathering
-
Question 20:
John, a penetration tester, was asked for a document that defines the project, specifies goals, objectives, deadlines, the resources required, and the approach of the project. Which of the following includes all of these requirements?
A. Penetration testing project plan
B. Penetration testing software project management plan
C. Penetration testing project scope report
D. Penetration testing schedule plan
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-055
Sun Certified Programmer for the Java 2 Platform.SE 5.0212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 412-79V10 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.