Exam Details
Exam Code
:412-79V10Exam Name
:EC-Council Certified Security Analyst (ECSA) V10Certification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:201 Q&AsLast Updated
:Jun 27, 2025
EC-COUNCIL EC-COUNCIL Certifications 412-79V10 Questions & Answers
-
Question 191:
Which of the following shields Internet users from artificial DNS data, such as a deceptive or mischievous address instead of the genuine address that was requested?
A. DNSSEC
B. Firewall
C. Packet filtering
D. IPSec
-
Question 192:
The first and foremost step for a penetration test is information gathering. The main objective of this test is to gather information about the target system which can be used in a malicious manner to gain access to the target systems.

Which of the following information gathering terminologies refers to gathering information through social engineering on-site visits, face-to-face interviews, and direct questionnaires?
A. Active Information Gathering
B. Pseudonymous Information Gathering
C. Anonymous Information Gathering
D. Open Source or Passive Information Gathering
-
Question 193:
Port numbers are used to keep track of different conversations crossing the network at the same time. Both TCP and UDP use port (socket) numbers to pass information to the upper layers. Port numbers have the assigned ranges. The port numbers above 1024 are considered as which one of the following? (Select all that apply)
A. Well-known port numbers
B. Dynamically assigned port numbers
C. Unregistered port numbers
D. Statically assigned port numbers
-
Question 194:
Which of the following contents of a pen testing project plan addresses the strengths, weaknesses, opportunities, and threats involved in the project?
A. Project Goal
B. Success Factors
C. Objectives
D. Assumptions
-
Question 195:
What is a goal of the penetration testing report?
A. The penetration testing report helps you comply with local laws and regulations related to environmental conditions in the organization.
B. The penetration testing report allows you to sleep better at night thinking your organization is protected
C. The pen testing report helps executive management to make decisions on implementing security controls in the organization and helps the security team implement security controls and patch any flaws discovered during testing.
D. The penetration testing report allows you to increase sales performance by effectively communicating with the internal security team.
-
Question 196:
The objective of social engineering pen testing is to test the strength of human factors in a security chain within the organization. It is often used to raise the level of security awareness among employees.
The tester should demonstrate extreme care and professionalism during a social engineering pen test as it might involve legal issues such as violation of privacy and may result in an embarrassing situation for the organization.
Which of the following methods of attempting social engineering is associated with bribing, handing out gifts, and becoming involved in a personal relationship to befriend someone inside the company?
A. Accomplice social engineering technique
B. Identity theft
C. Dumpster diving
D. Phishing social engineering technique
-
Question 197:
Which of the following policies helps secure data and protects the privacy of organizational information?
A. Special-Access Policy
B. Document retention Policy
C. Cryptography Policy
D. Personal Security Policy
-
Question 198:
Wireshark is a network analyzer. It reads packets from the network, decodes them, and presents them in an easy-to-understand format. Which one of the following is the command-line version of Wireshark, which can be used to capture the live packets from the wire or to read the saved capture files?
A. Tcpdump
B. Capinfos
C. Tshark
D. Idl2wrs
-
Question 199:
In a TCP packet filtering firewall, traffic is filtered based on specified session rules, such as when a session is initiated by a recognized computer.
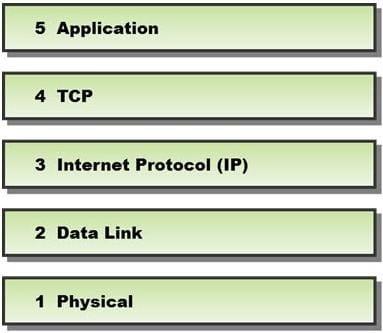
Identify the level up to which the unknown traffic is allowed into the network stack.
A. Level 5 ?Application
B. Level 2 ?Data Link
C. Level 4 ?TCP
D. Level 3 ?Internet Protocol (IP)
-
Question 200:
What is a difference between host-based intrusion detection systems (HIDS) and network- based intrusion detection systems (NIDS)?
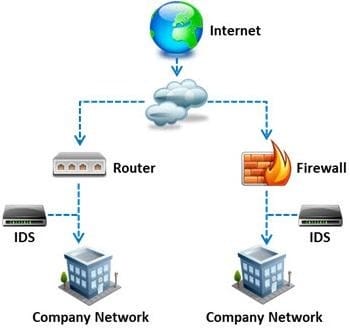
A. NIDS are usually a more expensive solution to implement compared to HIDS.
B. Attempts to install Trojans or backdoors cannot be monitored by a HIDS whereas NIDS can monitor
and stop such intrusion events.
C. NIDS are standalone hardware appliances that include network intrusion detection capabilities whereas HIDS consist of software agents installed on individual computers within the system.
D. HIDS requires less administration and training compared to NIDS.
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-055
Sun Certified Programmer for the Java 2 Platform.SE 5.0212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 412-79V10 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.