412-79V10 Exam Details
-
Exam Code
:412-79V10 -
Exam Name
:EC-Council Certified Security Analyst (ECSA) V10 -
Certification
:EC-COUNCIL Certifications -
Vendor
:EC-COUNCIL -
Total Questions
:201 Q&As -
Last Updated
:
EC-COUNCIL 412-79V10 Online Questions & Answers
-
Question 1:
The term social engineering is used to describe the various tricks used to fool people (employees, business partners, or customers) into voluntarily giving away information that would not normally be known to the general public.
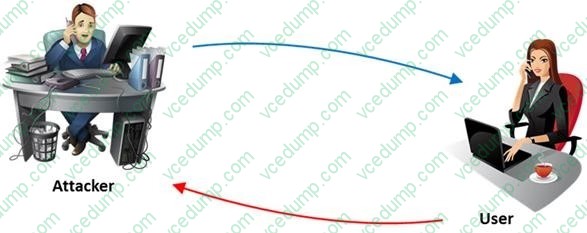
What is the criminal practice of social engineering where an attacker uses the telephone system in an attempt to scam the user into surrendering private information?
A. Phishing
B. Spoofing
C. Tapping
D. Vishing -
Question 2:
Which of the following is the objective of Gramm-Leach-Bliley Act?
A. To ease the transfer of financial information between institutions and banks
B. To protect the confidentiality, integrity, and availability of data
C. To set a new or enhanced standards for all U.S. public company boards, management and public accounting firms
D. To certify the accuracy of the reported financial statement -
Question 3:
Internet Control Message Protocol (ICMP) messages occur in many situations, such as whenever a datagram cannot reach the destination or the gateway does not have the buffering capacity to forward a datagram. Each ICMP message contains three fields: type, code, and checksum. Different types of Internet Control Message Protocols (ICMPs) are identified by a TYPE field. If the destination is not reachable, which one of the following are generated?
A. Type 8 ICMP codes
B. Type 12 ICMP codes
C. Type 3 ICMP codes
D. Type 7 ICMP codes -
Question 4:
This is a group of people hired to give details of the vulnerabilities present in the system found after a penetration test. They are elite and extremely competent penetration testers and intrusion analysts. This team prepares a report on the vulnerabilities in the system, attack methods, and how to defend against them.

What is this team called?
A. Blue team
B. Tiger team
C. Gorilla team
D. Lion team -
Question 5:
Which of the following policies states that the relevant application owner must authorize requests for additional access to specific business applications in writing to the IT Department/resource?
A. Special-Access Policy
B. User Identification and Password Policy
C. Personal Computer Acceptable Use Policy
D. User-Account Policy -
Question 6:
SQL injection attacks are becoming significantly more popular amongst hackers and there has been an estimated 69 percent increase of this attack type.
This exploit is used to great effect by the hacking community since it is the primary way to steal sensitive data from web applications. It takes advantage of non-validated input vulnerabilities to pass SQL commands through a web application
for execution by a back- end database.
The below diagram shows how attackers launched SQL injection attacks on web applications.
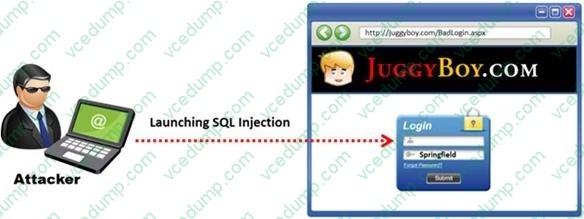
Which of the following can the attacker use to launch an SQL injection attack?
A. Blah' "2=2 ?
B. Blah' and 2=2 -
C. Blah' and 1=1 -
D. Blah' or 1=1 - -
Question 7:
A Blind SQL injection is a type of SQL Injection attack that asks the database true or false questions and determines the answer based on the application response. This attack is often used when the web application is configured to show generic error messages, but has not mitigated the code that is vulnerable to SQL injection.
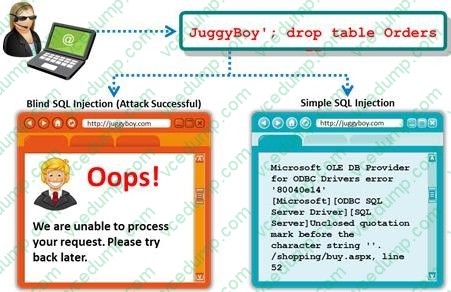
It is performed when an error message is not received from application while trying to exploit SQL vulnerabilities. The developer's specific message is displayed instead of an error message. So it is quite difficult to find SQL vulnerability in such cases. A pen tester is trying to extract the database name by using a blind SQL injection. He tests the database using the below query and finally finds the database name. http://juggyboy.com/page.aspx?id=1; IF (LEN(DB_NAME())=4) WAITFOR DELAY '00:00:10'-http://juggyboy.com/page.aspx?id=1; IF (ASCII(lower(substring((DB_NAME()),1,1)))=97) WAITFOR DELAY '00:00:10'-http://juggyboy.com/page.aspx?id=1; IF (ASCII(lower(substring((DB_NAME()),2,1)))=98) WAITFOR DELAY '00:00:10'-http://juggyboy.com/page.aspx?id=1; IF (ASCII(lower(substring((DB_NAME()),3,1)))=99) WAITFOR DELAY '00:00:10'-http://juggyboy.com/page.aspx?id=1; IF (ASCII(lower(substring((DB_NAME()),4,1)))=100) WAITFOR DELAY '00:00:10'-What is the database name?
A. WXYZ
B. PQRS
C. EFGH
D. ABCD -
Question 8:
What information can be collected by dumpster diving?
A. Sensitive documents
B. Email messages
C. Customer contact information
D. All the above -
Question 9:
Rules of Engagement (ROE) document provides certain rights and restriction to the test team for performing the test and helps testers to overcome legal, federal, and policy-related restrictions to use different penetration testing tools and techniques.

What is the last step in preparing a Rules of Engagement (ROE) document?
A. Conduct a brainstorming session with top management and technical teams
B. Decide the desired depth for penetration testing
C. Conduct a brainstorming session with top management and technical teams
D. Have pre-contract discussions with different pen-testers -
Question 10:
Identify the injection attack represented in the diagram below:
A. XPath Injection Attack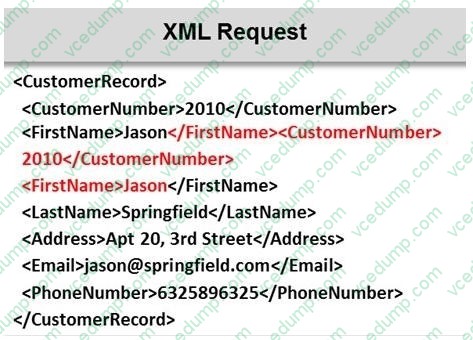
B. XML Request Attack
C. XML Injection Attack
D. Frame Injection Attack
Related Exams:
-
112-51
EC-Council Certified Network Defense Essentials (NDE) -
212-055
Sun Certified Programmer for the Java 2 Platform.SE 5.0 -
212-77
EC-Council Certified Linux Security -
212-81
EC-Council Certified Encryption Specialist (ECES) -
212-82
EC-Council Certified Cybersecurity Technician (C|CT) -
212-89
EC Council Certified Incident Handler (ECIH v3) -
312-38
EC-Council Certified Network Defender (CND) -
312-39
EC-Council Certified SOC Analyst (CSA) -
312-40
EC-Council Certified Cloud Security Engineer (CCSE) -
312-49
ECCouncil Computer Hacking Forensic Investigator (V9)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 412-79V10 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.