Exam Details
Exam Code
:412-79V10Exam Name
:EC-Council Certified Security Analyst (ECSA) V10Certification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:201 Q&AsLast Updated
:Jun 27, 2025
EC-COUNCIL EC-COUNCIL Certifications 412-79V10 Questions & Answers
-
Question 21:
Which of the following appendices gives detailed lists of all the technical terms used in the report?
A. Required Work Efforts
B. References
C. Research
D. Glossary
-
Question 22:
Identify the type of firewall represented in the diagram below:
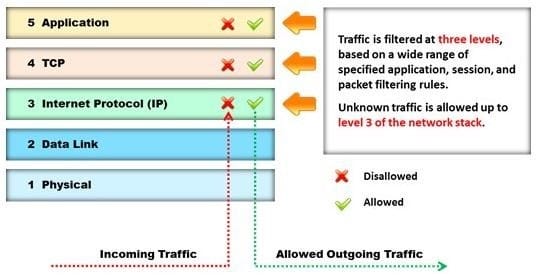
A. Stateful multilayer inspection firewall
B. Application level gateway
C. Packet filter
D. Circuit level gateway
-
Question 23:
Which of the following reports provides a summary of the complete pen testing process, its outcomes, and recommendations?
A. Vulnerability Report
B. Executive Report
C. Client-side test Report
D. Host Report
-
Question 24:
An automated electronic mail message from a mail system which indicates that the user does not exist on that server is called as?
A. SMTP Queue Bouncing
B. SMTP Message Bouncing
C. SMTP Server Bouncing
D. SMTP Mail Bouncing
-
Question 25:
Which of the following password hashing algorithms is used in the NTLMv2 authentication mechanism?
A. AES
B. DES (ECB mode)
C. MD5
D. RC5
-
Question 26:
A WHERE clause in SQL specifies that a SQL Data Manipulation Language (DML) statement should only affect rows that meet specified criteria. The criteria are expressed in the form of predicates. WHERE clauses are not mandatory clauses of SQL DML statements, but can be used to limit the number of rows affected by a SQL DML statement or returned by a query.
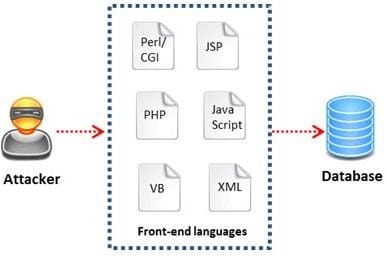
A pen tester is trying to gain access to a database by inserting exploited query statements with a WHERE clause. The pen tester wants to retrieve all the entries from the database using the WHERE clause from a particular table (e.g. StudentTable).
What query does he need to write to retrieve the information?
A. EXTRACT* FROM StudentTable WHERE roll_number = 1 order by 1000
B. DUMP * FROM StudentTable WHERE roll_number = 1 AND 1=1-
C. SELECT * FROM StudentTable WHERE roll_number = '' or '1' = '1`
D. RETRIVE * FROM StudentTable WHERE roll_number = 1'#
-
Question 27:
Which one of the following acts related to the information security in the US fix the responsibility of management for establishing and maintaining an adequate internal control structure and procedures for financial reporting?
A. California SB 1386
B. Sarbanes-Oxley 2002
C. Gramm-Leach-Bliley Act (GLBA)
D. USA Patriot Act 2001
-
Question 28:
The amount of data stored in organizational databases has increased rapidly in recent years due to the rapid advancement of information technologies. A high percentage of these data is sensitive, private and critical to the organizations, their clients and partners.
Therefore, databases are usually installed behind internal firewalls, protected with intrusion detection mechanisms and accessed only by applications. To access a database, users have to connect to one of these applications and submit queries through them to the database. The threat to databases arises when these applications do not behave properly and construct these queries without sanitizing user inputs first.
Identify the injection attack represented in the diagram below:
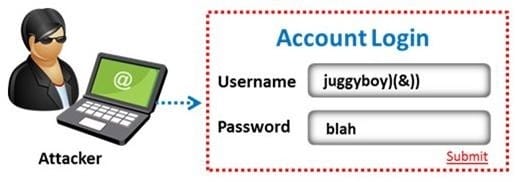
A. Frame Injection Attack
B. LDAP Injection Attack
C. XPath Injection Attack
D. SOAP Injection Attack
-
Question 29:
Which one of the following Snort logger mode commands is associated to run a binary log file through Snort in sniffer mode to dump the packets to the screen?
A. ./snort -dvr packet.log icmp
B. ./snort -dev -l ./log
C. ./snort -dv -r packet.log
D. ./snort -l ./log -b
-
Question 30:
TCP/IP model is a framework for the Internet Protocol suite of computer network protocols that defines the communication in an IP-based network. It provides end-to-end connectivity specifying how data should be formatted, addressed, transmitted, routed and received at the destination. This functionality has been organized into four abstraction layers which are used to sort all related protocols according to the scope of networking involved.
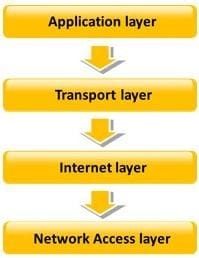
Which of the following TCP/IP layers selects the best path through the network for packets to travel?
A. Transport layer
B. Network Access layer
C. Internet layer
D. Application layer
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-055
Sun Certified Programmer for the Java 2 Platform.SE 5.0212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 412-79V10 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.