Exam Details
Exam Code
:350-401Exam Name
:Implementing and Operating Cisco Enterprise Network Core Technologies (ENCOR)Certification
:CCIE Enterprise WirelessVendor
:CiscoTotal Questions
:1457 Q&AsLast Updated
:Jul 10, 2025
Cisco CCIE Enterprise Wireless 350-401 Questions & Answers
-
Question 931:
Refer to the exhibit. After configuring HSRP an engineer enters the show standby command. Which two facts are derived from the output? (Choose two.)
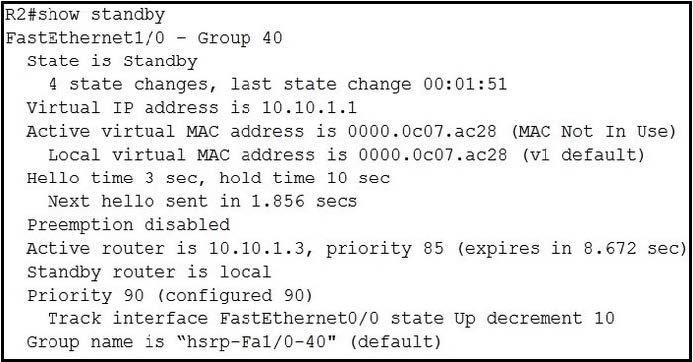
A. The router with IP 10.10 1.3 is active because it has a higher IP address
B. If Fa0/0 is shut down, the HSRP pnonty on R2 becomes 80
C. R2 Fa1/0 regains the primary role when the link comes back up
D. R2 becomes the active router after the hold time expires.
E. R2 is using the default HSRP hello and hold timers.
-
Question 932:
What does the LAP send when multiple WLCs respond to the CISCO_CAPWAPCONTROLLER.localdomain hostname during the CAPWAP discovery and join process?
A. broadcast discover request
B. join request to all the WLCs
C. unicast discovery request to each WLC
D. Unicast discovery request to the first WLS that resolves the domain name
-
Question 933:
What are two benefits of implementing a Cisco SD-WAN architecture? (Choose two)
A. It provides resilient and effective traffic flow using MPLS.
B. It improves endpoint protection by integrating embedded and cloud security features.
C. It allows configuration of application-aware policies with real time enforcement.
D. It simplifies endpoint provisioning through standalone router management
E. It enforces a single. scalable. hub-and-spoke topology.
-
Question 934:
Refer to the exhibit.
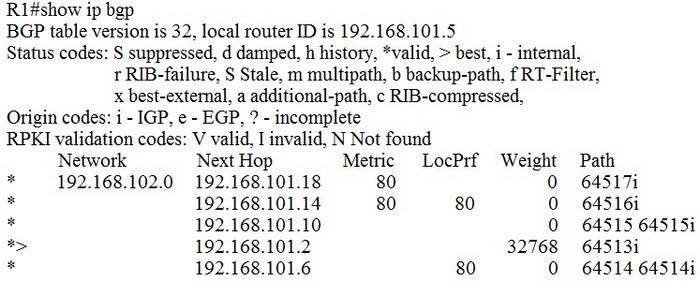
Which IP address becomes the active next hop for 192.168.102 0/24 when 192.168.101.2 fails?
A. 192.168.101.18
B. 192.168.101.6
C. 192.168.101.10
D. 192.168.101.14
-
Question 935:
Refer to the exhibit. VPN-A sends point-to-point traffic to VPN-B and receives traffic only from VPN-C VPN-B sends point-to-point traffic to VPN-C and receives traffic only from VPN-A. Which configuration is applied?
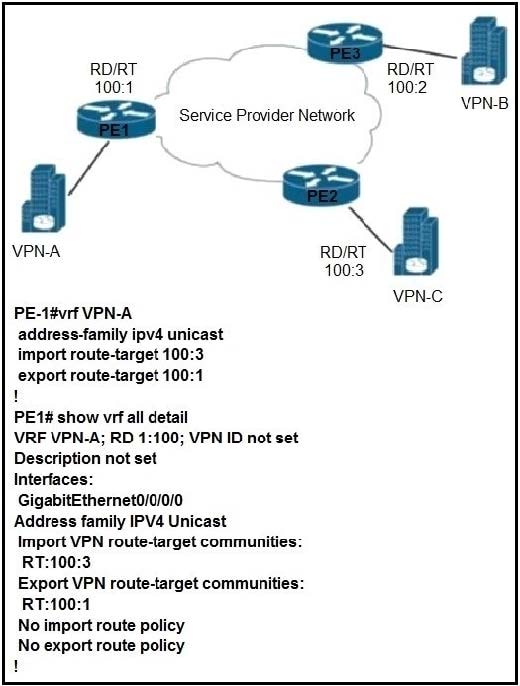
A. PE-2 vrf VPN-B address-family ipv4 unicast import route-target 100:1 export route-target 100:2
B. PE-3 vrf VPN-B address-family ipv4 unicast import route-target 100:1 export route-target 100:2
C. PE-2 vrf VPN-B address-family ipv4 unicast import route-target 100:1 export route-target 100:2
D. PE-3 vrf VPN-B address-family ipv4 unicast import route-target 100:2 export route-target 100:2
-
Question 936:
What is a VPN in a Cisco SD-WAN deployment?
A. common exchange point between two different services
B. attribute to identify a set of services offered in specific places in the SD-WAN fabric
C. virtualized environment that provides traffic isolation and segmentation in the SD-WAN fabric
D. virtual channel used to carry control plane information
-
Question 937:
Refer to the exhibit.
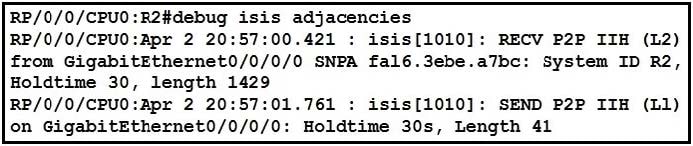
A network operator is attempting to configure an IS-IS adjacency between two routers, but the adjacency cannot be established. To troubleshoot the problem, the operator collects this debugging output. Which interfaces are misconfigured on these routers?
A. The peer router interface is configured as Level 1 only, and the R2 interface is configured as Level 2 only.
B. The R2 interface is configured as Level 1 only, and the Peer router interface is configured as Level 2 only.
C. The R2 interface is configured as point-to-point, and the peer router interface is configured as multipoint.
D. The peer router interface is configured as point-as-point, and the R2 interface is configured as multipoint.
-
Question 938:
A network engineer configures a WLAN controller with increased security for web access. There is IP connectivity with the WLAN controller, but the engineer cannot start a management session from a web browser. Which action resolves the issued?
A. Disable JavaScript on the web browser
B. Disable Adobe Flash Player
C. Use a browser that supports 128-bit or larger ciphers.
D. Use a private or incognito session.
-
Question 939:
Refer to the exhibit.
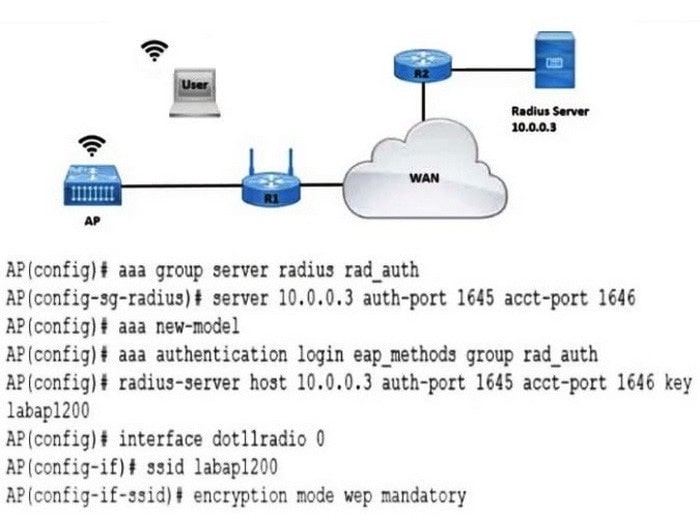
A company requires that all wireless users authenticate using dynamic key generation. Which configuration must be applied?
A. AP(config-if-ssid)# authentication open wep wep_methods
B. AP(config-if-ssid)# authentication dynamic wep wep_methods
C. AP(config-if-ssid)# authentication dynamic open wep_dynamic
D. AP(config-if-ssid)# authentication open eap eap_methods
-
Question 940:
A network administrator is Implementing a routing configuration change and enables routing debugs to track routing behavior during the change. The logging output on the terminal is interrupting the command typing process.
Which two actions can the network administrator take to minimize the possibility of typing commands incorrectly? (Choose two.)
A. Configure the logging synchronous global configuration command
B. Configure the logging delimiter feature
C. Configure the logging synchronous command under the vty
D. Press the TAB key to reprint the command in a new line
E. increase the number of lines on the screen using the terminal length command
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Cisco exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 350-401 exam preparations and Cisco certification application, do not hesitate to visit our Vcedump.com to find your solutions here.