Exam Details
Exam Code
:210-250Exam Name
:Cisco Cybersecurity FundamentalsCertification
:Cisco CertificationsVendor
:CiscoTotal Questions
:1157 Q&AsLast Updated
:Nov 03, 2022
Cisco Cisco Certifications 210-250 Questions & Answers
-
Question 841:
Which feature allows a firewall to look at Layer 7 information to block threats?
A. packet filtering
B. access control lists
C. deep packet inspection
D. diagnostic signature
-
Question 842:
Refer to the exhibit. Which of these is depicted?
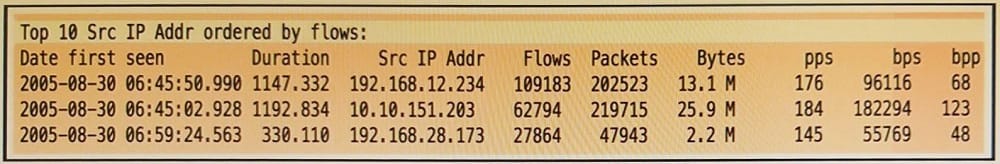
A. IPS event data
B. network discovery event
C. NetFlow data
D. IIS data
-
Question 843:
Which type of data collection requires the largest amount of storage space?
A. alert data
B. session data
C. full packet capture
D. transaction data
-
Question 844:
What are two examples of personally identifiable information? (Choose two.)
A. email address
B. business street address
C. job title
D. personal web site
E. passport number
-
Question 845:
Which two items are useful for investigating security incidents that affect employee laptops? (Choose two.)
A. SSL remote access VPN configuration
B. Python script to automate firewall access control lists
C. antivirus logs
D. application logs
E. remote wipe mobile device logs
-
Question 846:
Which security technology allows only a set of pre-approved applications to run on a system?
A. application-level blacklisting
B. host-based IPS
C. antivirus
D. application-level whitelisting
-
Question 847:
The target web application server is running as the root user and is vulnerable to command injection. Which result of a successful attack is true?
A. cross-site scripting
B. cross-site request forgery
C. privilege escalation
D. buffer overflow
-
Question 848:
Which description is an example of whaling?
A. when attackers go after the CEO
B. when attackers target specific individuals
C. when attackers use fraudulent websites that look like legitimate ones
D. when attackers target a group of individuals
-
Question 849:
A system administrator installs an IDS to protect users on 10.2.3.0/24. After the installation, users can see only other machines on their /24 consistently and cannot reach external sites. Which possible explanation is true?
A. The IDS is working properly and providing the users on 10.2.3.0/24 with the security they need
B. The IDS was configured to fail open and has not yet been fully configured
C. The IDS was installed inline and is dropping traffic that must be allowed
D. The system administrator mirrored the traffic for that network segment and did not tune the IDS properly
-
Question 850:
Which protocol is used on IPv6 to resolve a Layer 3 address to a Layer 2 address?
A. ICMPv6
B. DHCPv6
C. ARPv6
D. PNPv6
Related Exams:
300-915
Developing Solutions using Cisco IoT and Edge Platforms (DEVIOT)300-920
Developing Applications for Cisco Webex and Webex Devices (DEVWBX)352-011
Cisco Certified Design Expert Practical500-052
Cisco Unified Contact Center Express500-173
Designing the FlexPod Solution (FPDESIGN)500-174
Implementing and Administering the FlexPod Solution (FPIMPADM)500-201
Deploying Cisco Service Provider Mobile Backhaul Solutions500-210
SP Optical Technology Field Engineer Representative500-220
Cisco Meraki Solutions Specialist500-230
Cisco Service Provider Routing Field Engineer
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Cisco exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 210-250 exam preparations and Cisco certification application, do not hesitate to visit our Vcedump.com to find your solutions here.