Exam Details
Exam Code
:210-250Exam Name
:Cisco Cybersecurity FundamentalsCertification
:Cisco CertificationsVendor
:CiscoTotal Questions
:1157 Q&AsLast Updated
:Nov 03, 2022
Cisco Cisco Certifications 210-250 Questions & Answers
-
Question 861:
Which tool provides universal query access to text-based data such as event logs and file system?
A. log parser
B. Windows Management Instrumentation
C. handles
D. service viewer
-
Question 862:
Which option is true when using the traffic mirror feature in a switch?
A. Packets are automatically decrypted.
B. Ethernet headers are modified before capture.
C. Packet payloads are lost.
D. Full packet captures are possible.
-
Question 863:
Endpoint logs indicate that a machine has obtained an unusual gateway address and unusual DNS servers via DHCP. Which option is this situation most likely an example of?
A. command injection
B. man in the middle attack
C. evasion methods
D. phishing
-
Question 864:
After a large influx of network traffic to externally facing devices, you begin investigating what appears to be a denial of service attack. When you review packet capture data, you notice that the traffic is a single SYN packet to each port. Which kind of attack is this?
A. SYN flood
B. port scanning
C. traffic fragmentation
D. host profiling
-
Question 865:
Which data type is the most beneficial to recreate a binary file for malware analysis?
A. session data
B. statistical data
C. extracted content data
D. alert data
-
Question 866:
Which NTP service is a best practice to ensure that all network devices are synchronized with a reliable and trusted time source?
A. redundant authenticated NTP
B. local NTP within each network device
C. redundant unauthenticated NTP
D. authenticated NTP services from one of the local AD domain controllers
-
Question 867:
Which benefit does the Antivirus Engine within AMP for Endpoints provide?
A. It displays all files that have been executed across your organization, ordered by prevalence from lowest to highest.
B. It continuously tracks file propagation over time throughout your environment.
C. It performs offline and system-based detections, including rootkit scanning.
D. It provides visibility into which command-line arguments are used to launch executables.
-
Question 868:
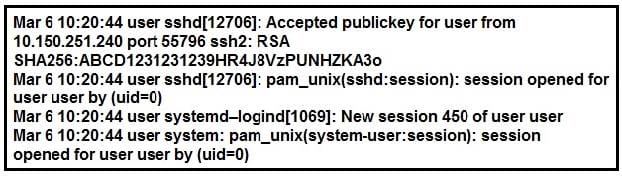
Refer to the exhibit. Which description of what happened on the system is true?
A. A user connected to the system using SSH using source port 55796.
B. A user created a new HTTP session using the SHA256 hashing algorithm.
C. A user connected to the system after 450 attempts.
D. A user connected to the system using remote access VPN.
-
Question 869:
What does the sum of the risks presented by an application represent for that application?
A. application attack surface
B. HIPPA violation
C. vulnerability
D. security violation
-
Question 870:
Which two characteristics of a secure hashing algorithm are true? (Choose two.)
A. produces a variable-length output
B. not reversible
C. produces a fixed-length output
D. susceptible to collisions
E. reversible
Related Exams:
300-915
Developing Solutions using Cisco IoT and Edge Platforms (DEVIOT)300-920
Developing Applications for Cisco Webex and Webex Devices (DEVWBX)352-011
Cisco Certified Design Expert Practical500-052
Cisco Unified Contact Center Express500-173
Designing the FlexPod Solution (FPDESIGN)500-174
Implementing and Administering the FlexPod Solution (FPIMPADM)500-201
Deploying Cisco Service Provider Mobile Backhaul Solutions500-210
SP Optical Technology Field Engineer Representative500-220
Cisco Meraki Solutions Specialist500-230
Cisco Service Provider Routing Field Engineer
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Cisco exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 210-250 exam preparations and Cisco certification application, do not hesitate to visit our Vcedump.com to find your solutions here.