Exam Details
Exam Code
:210-250Exam Name
:Cisco Cybersecurity FundamentalsCertification
:Cisco CertificationsVendor
:CiscoTotal Questions
:1157 Q&AsLast Updated
:Nov 03, 2022
Cisco Cisco Certifications 210-250 Questions & Answers
-
Question 831:
Which situation for agentless protection is more ideal?
A. when mobile devices are used on the network but not present in the infrastructure all of the time
B. when using an agent that is not compatible with the underlying operating system
C. when desktop computers are present on the network and remain there
D. when you have wireless devices within the network and they are present some of the time
-
Question 832:
Which is considered a configuration item?
A. network switch
B. SNMP configuration on a router
C. software backup image of a server
D. policy-defining configuration management
-
Question 833:
Which feature does SIEM provide?
A. event correlation
B. asset management
C. signature detection
D. inline blocking
-
Question 834:
How can an attacker observe network traffic exchanged between two users?
A. port scanning
B. denial of service
C. command injection
D. main-in-the-middle
-
Question 835:
Refer to the exhibit. Which two statements about laptop A with respect to server B are true? (Choose two.)
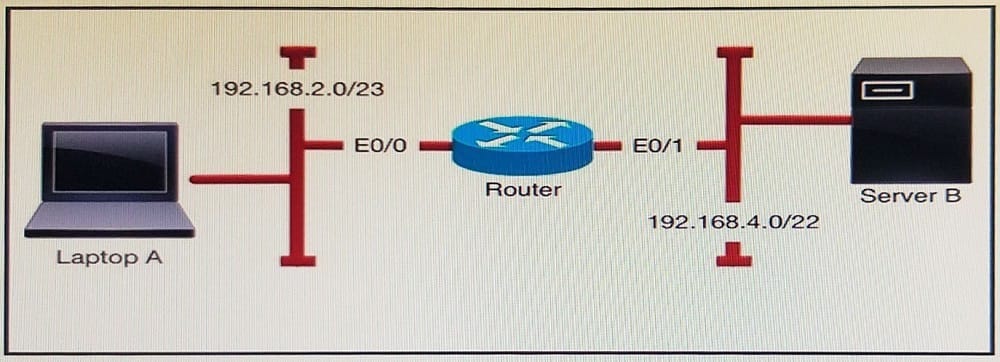
A. Laptop A and server B are in the same subnet
B. Laptop A can send a broadcast packet and reach server B
C. Laptop A and server B are in different subnets
D. Laptop A can communicate with server B at Layer 2
E. Laptop A does not know the MAC address of server B
-
Question 836:
Which technology has the limitation of network level encryption being natively incorporated?
A. IPsec
B. TLS
C. Kerberos
D. SSL
-
Question 837:
How do traffic interrogation applications function when inline?
A. They ingest the traffic as it passes through the device and inspect it in real time
B. They create a copy of the packet and send it off to be analyzed by an IDS or IPS
C. They utilize header information passed to it from mirrored ports
D. They passively "sniff" the wire to look for signatures
-
Question 838:
Refer to the exhibit. Which tool generated this output?
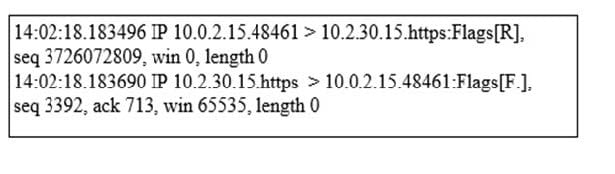
A. ps
B. syslog
C. tcpdump
D. ipfw
-
Question 839:
Which statement best describes an application proxy?
A. They are devices that operate as intermediary agents on behalf of clients
B. Application proxies can be classified as next-generation firewalls
C. Clients on the protected network send connection requests to the application proxy to encrypt packets to the internet
D. Application proxies always perform Network Address Translation on behalf of clients
-
Question 840:
In which type of an attack does an attacker send falsified and spoofed resource record information to a DNS resolver?
A. DNS reflection attack
B. DNS denial of service attack
C. DNS cache poisoning
D. DNS utilization attack
Related Exams:
300-915
Developing Solutions using Cisco IoT and Edge Platforms (DEVIOT)300-920
Developing Applications for Cisco Webex and Webex Devices (DEVWBX)352-011
Cisco Certified Design Expert Practical500-052
Cisco Unified Contact Center Express500-173
Designing the FlexPod Solution (FPDESIGN)500-174
Implementing and Administering the FlexPod Solution (FPIMPADM)500-201
Deploying Cisco Service Provider Mobile Backhaul Solutions500-210
SP Optical Technology Field Engineer Representative500-220
Cisco Meraki Solutions Specialist500-230
Cisco Service Provider Routing Field Engineer
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Cisco exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 210-250 exam preparations and Cisco certification application, do not hesitate to visit our Vcedump.com to find your solutions here.