Exam Details
Exam Code
:SY0-601Exam Name
:CompTIA Security+Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1334 Q&AsLast Updated
:Jul 04, 2025
CompTIA CompTIA Certifications SY0-601 Questions & Answers
-
Question 261:
Which of the following documents specifies what to do in the event of catastrophic loss of a physical or virtual system?
A. Data retention plan
B. Incident response plan
C. Disaster recovery plan
D. Communication plan
-
Question 262:
Which of the following rales is responsible for defining the protection type and classification type for a given set of files?
A. General counsel
B. Data owner
C. Risk manager
D. Chief Information Officer
-
Question 263:
An employee's company email is configured with conditional access and requires that MFA is enabled and used. An example of MFA is a phone call and:
A. a push notification
B. a password
C. an SMS message
D. an authentication application
-
Question 264:
Which of the following is a security implication of newer ICS devices that are becoming more common in corporations?
A. Devices with cellular communication capabilities bypass traditional network security controls
B. Many devices do not support elliptic-curve encryption algorithms due to the overhead they require
C. These devices often lack privacy controls and do not meet newer compliance regulations
D. Unauthorized voice and audio recording can cause loss of intellectual property
-
Question 265:
A security analyst is reviewing packet capture data from a compromised host on the network. In the packet capture, the analyst locates packets that contain large amounts of text. Which of the following is most likely installed on the compromised host?
A. Keylogger
B. Spyware
C. Trojan
D. Ransomware
-
Question 266:
A user is having network connectivity issues when working from a coffee shop. The user has used the coffee shop as a workspace for several months without any issues. None of the other customers at the coffee shop are experiencing these issues. A help desk analyst at the user's company reviews the following Wi-Fi log:
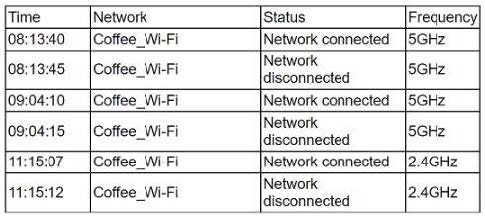
Which of the following best describes what is causing this issue?
A. Another customer has configured a rogue access point.
B. The coffee shop network is using multiple frequencies.
C. A denial-of-service attack by disassociation is occurring.
D. An evil twin access point is being utilized.
-
Question 267:
Which of the following is a physical security control that ensures only the authorized user is present when gaining access to a secured area?
A. A biometric scanner
B. A smart card reader
C. A PKI token
D. A PIN pad
-
Question 268:
A company is moving to new location. The systems administrator has provided the following server room requirements to the facilities staff:
Consistent power levels in case of brownouts or voltage spikes A minimum of 30 minutes runtime following a power outage Ability to trigger graceful shutdowns of critical systems
Which of the following would BEST meet the requirements?
A. Maintaining a standby, gas-powered generator.
B. Using large surge suppressors on computer equipment.
C. Configuring managed PDUs to monitor power levels.
D. Deploying an appropriately sized, network-connected UPS device.
-
Question 269:
Which of the following should customers who are involved with UI developer agreements be concerned with when considering the use of these products on highly sensitive projects?
A. Weak configurations
B. Integration activities
C. Unsecure user accounts
D. Outsourced code development
-
Question 270:
A security architect is designing a remote access solution for a business partner. The business partner needs to access one Linux server at the company. The business partner wants to avoid managing a password for authentication and additional software installation. Which of the following should the architect recommend?
A. Soft token
B. Smart card
C. CSR
D. SSH key
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-1202
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your SY0-601 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.