Exam Details
Exam Code
:SY0-601Exam Name
:CompTIA Security+Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1334 Q&AsLast Updated
:Jul 04, 2025
CompTIA CompTIA Certifications SY0-601 Questions & Answers
-
Question 271:
A security analyst is assisting a team of developers with best practices for coding. The security analyst would like to defend against the use of SQL injection attacks. Which of the following should the security analyst recommend first?
A. Tokenization
B. Input validation
C. Code signing
D. Secure cookies
-
Question 272:
Cloud security engineers are planning to allow and deny access to specific features in order to increase data security. Which of the following cloud features is the most appropriate to ensure access is granted properly?
A. API integrations
B. Auditing
C. Resource policies
D. Virtual networks
-
Question 273:
A security analyst is investigating a report from a penetration test. During the penetration test, consultants were able to download sensitive data from a back-end server. The back-end server was exposing an API that should have only been available from the company's mobile application. After reviewing the back-end server logs, the security analyst finds the following entries:
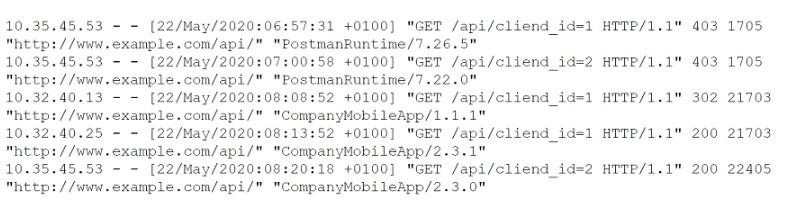
Which of the following is the most likely cause of the security control bypass?
A. IP address allow list
B. User-agent spoofing
C. WAF bypass
D. Referrer manipulation
-
Question 274:
A security analyst is investigating what appears to be unauthorized access to a corporate web application. The security analyst reviews the web server logs and finds the flowing entries:
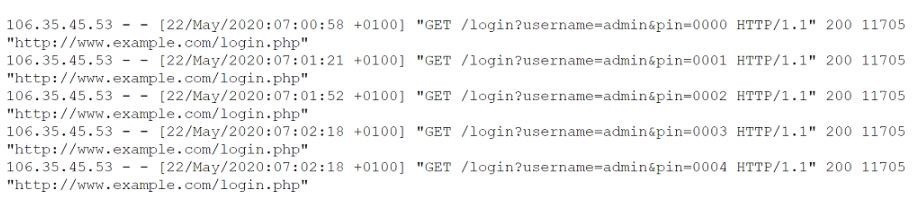
Which of the following password attacks is taking place?
A. Dictionary
B. Brute-force
C. Rainbow table
D. Spraying
-
Question 275:
A user reset the password for a laptop but has been unable to log in to it since then. In addition, several unauthorized emails were sent on the user's behalf recently. The security team investigates the issue and identifies the following findings:
Firewall logs show excessive traffic from the laptop to an external site.
Unknown processes were running on the laptop.
RDP connections that appeared to be authorized were made to other network devices from the laptop.
High bandwidth utilization alerts from that user's username.
Which of the following is most likely installed on the laptop?
A. Worm
B. Keylogger
C. Trojan
D. Logic bomb
-
Question 276:
A security analyst has been tasked with ensuring all programs that are deployed into the enterprise have been assessed in a runtime environment. Any critical issues found in the program must be sent back to the developer for verification and remediation. Which of the following BEST describes the type of assessment taking place?
A. Input validation
B. Dynamic code analysis
C. Fuzzing
D. Manual code review
-
Question 277:
Which of the following BEST describes the process of documenting who has access to evidence?
A. Order of volatility
B. Chain of custody
C. Non-repudiation
D. Admissibility
-
Question 278:
A systems engineer wants to leverage a cloud-based architecture with low latency between network-connected devices that also reduces the bandwidth that is required by performing analytics directly on the endpoints.
Which of the following would BEST meet the requirements? (Choose two.)
A. Private cloud
B. SaaS
C. Hybrid cloud
D. IaaS
E. DRaaS
F. Fog computing
-
Question 279:
Which of the following is a policy that provides a greater depth and breadth of knowledge across an organization?
A. Asset management policy
B. Separation of duties policy
C. Acceptable use policy
D. Job rotation policy
-
Question 280:
A security engineer must deploy two wireless routers in an office suite. Other tenants in the office building should not be able to connect to this wireless network. Which of the following protocols should the engineer implement to ensure the STRONGEST encryption?
A. WPS
B. WPA2
C. WAP
D. HTTPS
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-1202
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your SY0-601 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.