Exam Details
Exam Code
:SY0-601Exam Name
:CompTIA Security+Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1334 Q&AsLast Updated
:Jul 04, 2025
CompTIA CompTIA Certifications SY0-601 Questions & Answers
-
Question 281:
A penetration tester is brought on site to conduct a full attack simulation at a hospital. The penetration tester notices a WAP that is hanging from the drop ceiling by its cabling and is reachable. Which of the following recommendations would the penetration tester MOST likely make given this observation?
A. Employ a general contractor to replace the drop-ceiling tiles.
B. Place the network cabling inside a secure conduit.
C. Secure the access point and cabling inside the drop ceiling.
D. Utilize only access points that have internal antennas.
-
Question 282:
A security analyst notices that specific files are being deleted each time a systems administrator is on vacation. Which of the following BEST describes the type of malware that is running?
A. Fileless virus
B. Logic bomb
C. Keylogger
D. Ransomware
-
Question 283:
A security analyst needs to centrally manage credentials and permissions to the company's network devices. The following security requirements must be met:
All actions performed by the network staff must be logged.
Per-command permissions must be possible.
The authentication server and the devices must communicate through TCP.
Which of the following authentication protocols should the analyst choose?
A. Kerberos
B. CHAP
C. TACACS+
D. RADIUS
-
Question 284:
An organization is concerned about intellectual property theft by employees who leave the organization. Which of the following should the organization MOST likely implement?
A. CBT
B. NDA
C. MOU
D. AUP
-
Question 285:
A security analyst reviews web server logs and notices the following lines:
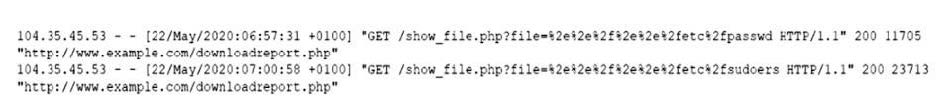
Which of the following vulnerabilities has the attacker exploited? (Choose two.)
A. Race condition
B. LFI
C. Pass the hash
D. XSS
E. RFI
F. Directory traversal
-
Question 286:
The marketing department at a retail company wants to publish an internal website to the internet so it is reachable by a limited number of specific, external service providers in a secure manner. Which of the following configurations would be BEST to fulfil this requirement?
A. NAC
B. ACL
C. WAF
D. NAT
-
Question 287:
A security administrator, who is working for a government organization, would like to utilize classification and granular planning to secure top secret data and grant access on a need-to-know basis. Which of the following access control schemas should the administrator consider?
A. Mandatory
B. Rule-based
C. Discretionary
D. Role-based
-
Question 288:
A cryptomining company recently deployed a new antivirus application to all of its mining systems. The installation of the antivirus application was tested on many personal devices, and no issues were observed. Once the antivirus application was rolled out to the servers, constant issues were reported. As a result, the company decided to remove the mining software. The antivirus application was MOST likely classifying the software as:
A. a rootkit
B. a PUP
C. a backdoor
D. ransomware
E. a RAT
-
Question 289:
A penetration tester executes the command crontab -l while working in a Linux server environment. The penetration tester observes the following string in the current user's list of cron jobs:
*/10 * * * * root /writable/update.sh
Which of the following actions should the penetration tester perform NEXT?
A. Privilege escalation
B. Memory leak
C. Directory traversal
D. Race condition
-
Question 290:
An employee used a corporate mobile device during a vacation. Multiple contacts were modified in the device during the employee's vacation. Which of the following attack methods did an attacker use to insert the contacts without having physical access to the device?
A. Jamming
B. Bluejacking
C. Disassociation
D. Evil twin
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-1202
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your SY0-601 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.