Exam Details
Exam Code
:SY0-601Exam Name
:CompTIA Security+Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1334 Q&AsLast Updated
:Jul 04, 2025
CompTIA CompTIA Certifications SY0-601 Questions & Answers
-
Question 251:
Which of the following types of disaster recovery plan exercises requires the least interruption to IT operations?
A. Parallel
B. Full-scale
C. Tabletop
D. Simulation
-
Question 252:
Which of the follow ng disaster recovery sites is the most cost effective to operate?
A. Warm site
B. Cold site
C. Hot site
D. Hybrid site
-
Question 253:
A security operations center wants to implement a solution that can execute files to test for malicious activity. The solution should provide a report of the files' activity against known threats. Which of the following should the security operations center implement?
A. Harvester
B. Nessus
C. Cuckoo
D. Sniper
-
Question 254:
A security administrator would like to ensure all cloud servers will have software preinstalled for facilitating vulnerability scanning and continuous monitoring. Which of the following concepts should the administrator utilize?
A. Provisioning
B. Staging
C. Quality assurance
-
Question 255:
A network architect wants a server to have the ability to retain network availability even if one of the network switches it is connected to goes down. Which of the following should the architect implement on the server to achieve this goal?
A. RAID
B. UPS
C. NIC teaming
D. Load balancing
-
Question 256:
Security analysts have noticed the network becomes flooded with malicious packets at specific times of the day. Which of the following should the analysts use to investigate this issue?
A. Web metadata
B. Bandwidth monitors
C. System files D. Correlation dashboards
-
Question 257:
A systems administrator is required to enforce MFA for corporate email account access, relying on the possession factor. Which of the following authentication methods should the systems administrator choose? (Choose two.)
A. Passphrase
B. Time-based one-time password
C. Facial recognition
D. Retina scan
E. Hardware token
F. Fingerprints
-
Question 258:
An employee who is using a mobile device for work, is required to use a fingerprint to unlock the device. Which of the following is this an example of?
A. Something you know
B. Something you are
C. Something you have
D. Somewhere you are
-
Question 259:
A security administrator needs to add fault tolerance and load balancing to the connection from the file server to the backup storage. Which of the following is the best choice to achieve this objective?
A. Multipath
B. RAID
C. Segmentation
D. 802.11
-
Question 260:
A security administrator examines the ARP table of an access switch and sees the following output:
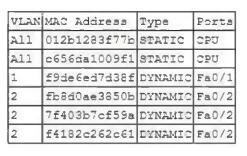
A. DDoS on Fa0/2 port
B. MAC flooding on Fa0/2 port
C. ARP poisoning on Fa0/1 port
D. DNS poisoning on port Fa0/1
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-1202
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your SY0-601 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.