Exam Details
Exam Code
:PT0-002Exam Name
:CompTIA PenTest+Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:455 Q&AsLast Updated
:Aug 07, 2025
CompTIA CompTIA Certifications PT0-002 Questions & Answers
-
Question 31:
Which of the following should be included in scope documentation?
A. Service accounts
B. Tester experience
C. Disclaimer
D. Number of tests
-
Question 32:
A Chief Information Security Officer wants to evaluate the security of the company's e- commerce application. Which of the following tools should a penetration tester use FIRST to obtain relevant information from the application without triggering alarms?
A. SQLmap
B. DirBuster
C. w3af
D. OWASP ZAP
-
Question 33:
A red team gained access to the internal network of a client during an engagement and used the Responder tool to capture important data. Which of the following was captured by the testing team?
A. Multiple handshakes
B. IP addresses
C. Encrypted file transfers
D. User hashes sent over SMB
-
Question 34:
A red team completed an engagement and provided the following example in the report to describe how the team gained access to a web server:
x' OR role LIKE '%admin%
Which of the following should be recommended to remediate this vulnerability?
A. Multifactor authentication
B. Encrypted communications
C. Secure software development life cycle
D. Parameterized queries
-
Question 35:
A penetration tester is contracted to attack an oil rig network to look for vulnerabilities. While conducting the assessment, the support organization of the rig reported issues connecting to corporate applications and upstream services for data acquisitions. Which of the following is the MOST likely culprit?
A. Patch installations
B. Successful exploits
C. Application failures
D. Bandwidth limitations
-
Question 36:
A penetration tester runs a scan against a server and obtains the following output: 21/tcp open ftp Microsoft ftpd | ftp-anon: Anonymous FTP login allowed (FTP code 230) | 03-12-20 09:23AM 331 index.aspx | ftp-syst: 135/tcp open msrpc Microsoft Windows RPC 139/tcp open netbios-ssn Microsoft Windows netbios-ssn 445/tcp open microsoft-ds Microsoft Windows Server 2012 Std 3389/tcp open ssl/ms-wbt-server | rdp-ntlm-info: | Target Name: WEB3 | NetBIOS_Computer_Name: WEB3 | Product_Version: 6.3.9600 |_ System_Time: 2021-01-15T11:32:06+00:00 8443/tcp open http Microsoft IIS httpd 8.5 | http-methods: |_ Potentially risky methods: TRACE |_http-server-header: Microsoft-IIS/8.5 |_http-title: IIS Windows Server Which of the following command sequences should the penetration tester try NEXT?
A. ftp 192.168.53.23
B. smbclient \\\\WEB3\\IPC$ -I 192.168.53.23 –U guest
C. ncrack –u Administrator –P 15worst_passwords.txt –p rdp 192.168.53.23
D. curl –X TRACE https://192.168.53.23:8443/index.aspx
E. nmap –-script vuln –sV 192.168.53.23
-
Question 37:
A penetration tester is able to use a command injection vulnerability in a web application to get a reverse shell on a system After running a few commands, the tester runs the following:
python -c 'import pty; pty.spawn("/bin/bash")'
Which of the following actions Is the penetration tester performing?
A. Privilege escalation
B. Upgrading the shell
C. Writing a script for persistence
D. Building a bind shell
-
Question 38:
A penetration tester downloaded a Java application file from a compromised web server and identifies how to invoke it by looking at the following log:
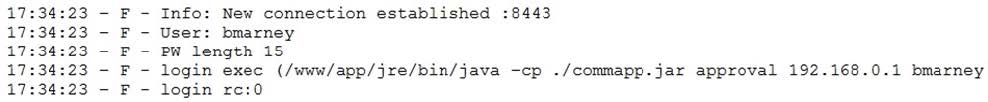
Which of the following is the order of steps the penetration tester needs to follow to validate whether the Java application uses encryption over sockets?
A. Run an application vulnerability scan and then identify the TCP ports used by the application.
B. Run the application attached to a debugger and then review the application's log.
C. Disassemble the binary code and then identify the break points.
D. Start a packet capture with Wireshark and then run the application.
-
Question 39:
A penetration tester logs in as a user in the cloud environment of a company. Which of the following Pacu modules will enable the tester to determine the level of access of the existing user?
A. iam_enum_permissions
B. iam_privesc_scan
C. iam_backdoor_assume_role
D. iam_bruteforce_permissions
-
Question 40:
A penetration tester learned that when users request password resets, help desk analysts change users' passwords to 123change. The penetration tester decides to brute force an internet-facing webmail to check which users are still using the temporary password. The tester configures the brute-force tool to test usernames found on a text file and the... Which of the following techniques is the penetration tester using?
A. Password brute force attack
B. SQL injection
C. Password spraying
D. Kerberoasting
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-1202
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your PT0-002 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.