Exam Details
Exam Code
:PT0-002Exam Name
:CompTIA PenTest+Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:455 Q&AsLast Updated
:Aug 07, 2025
CompTIA CompTIA Certifications PT0-002 Questions & Answers
-
Question 21:
A penetration tester is examining a Class C network to identify active systems quickly. Which of the following commands should the penetration tester use?
A. nmap sn 192.168.0.1/16
B. nmap sn 192.168.0.1-254
C. nmap sn 192.168.0.1 192.168.0.1.254
D. nmap sN 192.168.0.0/24
-
Question 22:
A penetration tester conducted a discovery scan that generated the following:
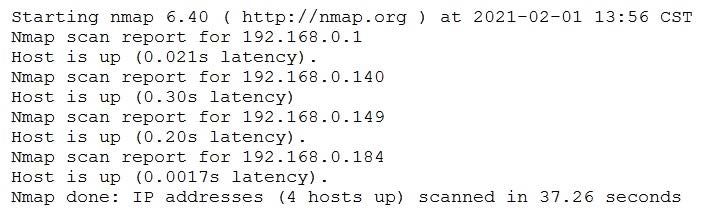
Which of the following commands generated the results above and will transform them into a list of active hosts for further analysis?
A. nmap –oG list.txt 192.168.0.1-254 , sort
B. nmap –sn 192.168.0.1-254 , grep “Nmap scan” | awk ‘{print S5}’
C. nmap –-open 192.168.0.1-254, uniq
D. nmap –o 192.168.0.1-254, cut –f 2
-
Question 23:
A penetration tester discovered a vulnerability that provides the ability to upload to a path via directory traversal. Some of the files that were discovered through this vulnerability are:
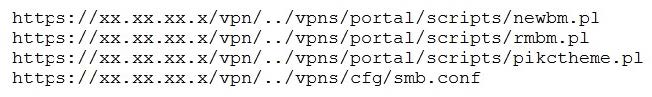
Which of the following is the BEST method to help an attacker gain internal access to the affected machine?
A. Edit the discovered file with one line of code for remote callback
B. Download .pl files and look for usernames and passwords
C. Edit the smb.conf file and upload it to the server
D. Download the smb.conf file and look at configurations
-
Question 24:
A penetration tester uncovers access keys within an organization's source code management solution. Which of the following would BEST address the issue? (Choose two.)
A. Setting up a secret management solution for all items in the source code management system
B. Implementing role-based access control on the source code management system
C. Configuring multifactor authentication on the source code management system
D. Leveraging a solution to scan for other similar instances in the source code management system
E. Developing a secure software development life cycle process for committing code to the source code management system
F. Creating a trigger that will prevent developers from including passwords in the source code management system
-
Question 25:
A penetration tester created the following script to use in an engagement:
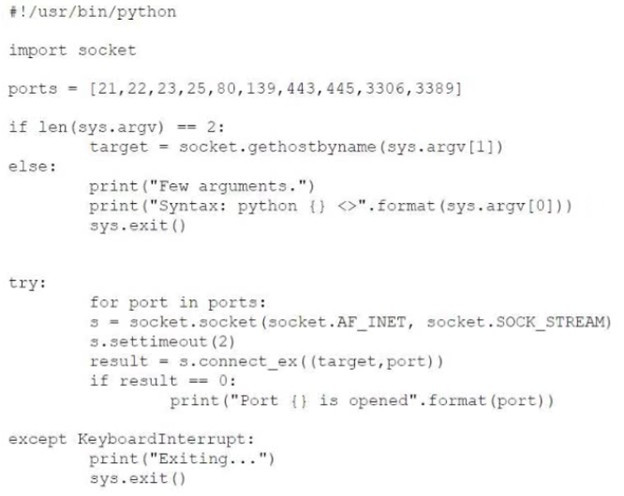
However, the tester is receiving the following error when trying to run the script:
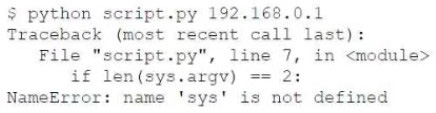
Which of the following is the reason for the error?
A. The sys variable was not defined.
B. The argv variable was not defined.
C. The sys module was not imported.
D. The argv module was not imported.
-
Question 26:
A company's Chief Executive Officer has created a secondary home office and is concerned that the WiFi service being used is vulnerable to an attack. A penetration tester is hired to test the security of the WiFi's router. Which of the following is MOST vulnerable to a brute-force attack?
A. WPS
B. WPA2-EAP
C. WPA-TKIP
D. WPA2-PSK
-
Question 27:
A penetration tester wants to validate the effectiveness of a DLP product by attempting exfiltration of data using email attachments. Which of the following techniques should the tester select to accomplish this task?
A. Steganography
B. Metadata removal
C. Encryption
D. Encode64
-
Question 28:
Which of the following OSSTM testing methodologies should be used to test under the worst conditions?
A. Tandem
B. Reversal
C. Semi-authorized
D. Known environment
-
Question 29:
A company provided the following network scope for a penetration test: 169.137.1.0/24 221.10.1.0/24 149.14.1.0/24 A penetration tester discovered a remote command injection on IP address 149.14.1.24 and exploited the system. Later, the tester learned that this particular IP address belongs to a third party. Which of the following stakeholders is
responsible for this mistake?
A. The company that requested the penetration test
B. The penetration testing company
C. The target host's owner
D. The penetration tester
E. The subcontractor supporting the test
-
Question 30:
Which of the following factors would a penetration tester most likely consider when testing at a location?
A. Determine if visas are required.
B. Ensure all testers can access all sites.
C. Verify the tools being used are legal for use at all sites.
D. Establish the time of the day when a test can occur.
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-1202
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your PT0-002 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.