Exam Details
Exam Code
:PT0-002Exam Name
:CompTIA PenTest+Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:455 Q&AsLast Updated
:Aug 07, 2025
CompTIA CompTIA Certifications PT0-002 Questions & Answers
-
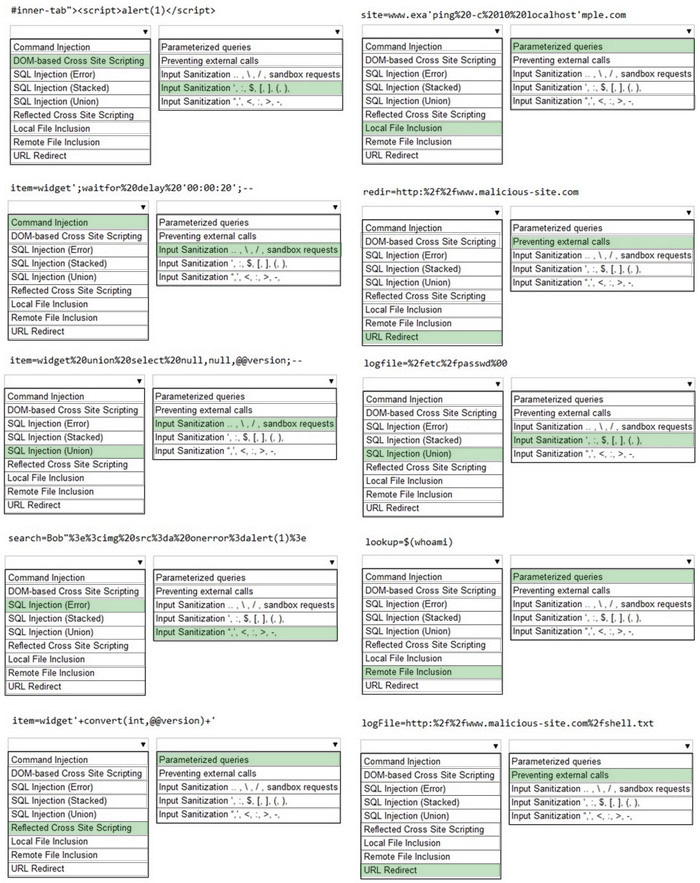
Question 41:
CORRECT TEXT SIMULATION Using the output, identify potential attack vectors that should be further investigated.
-
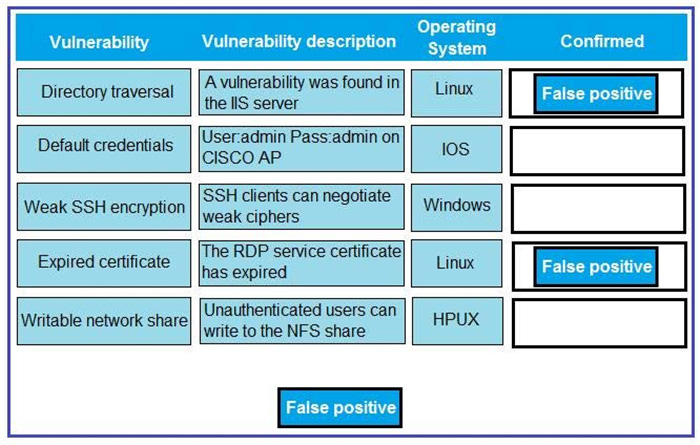
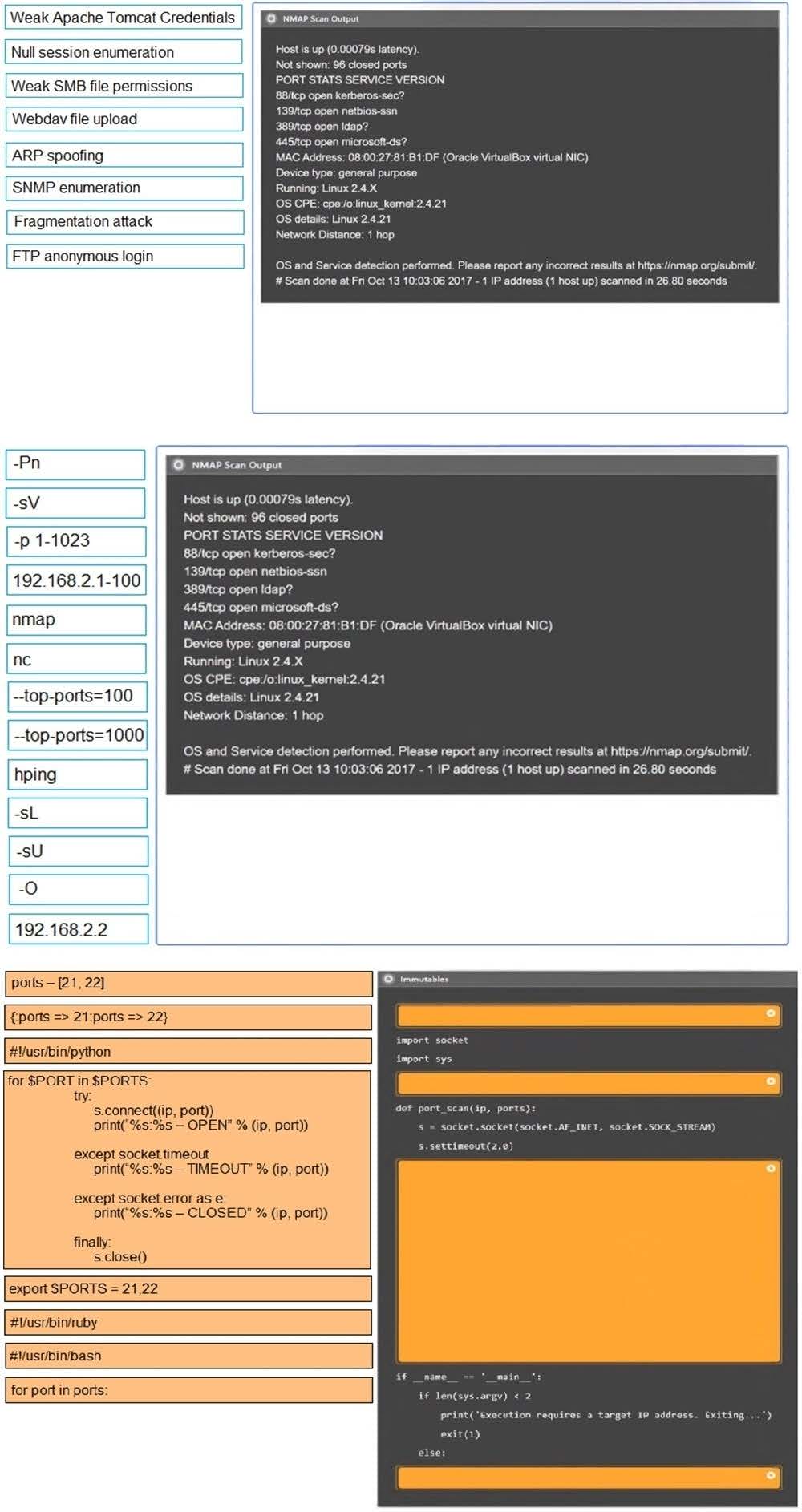
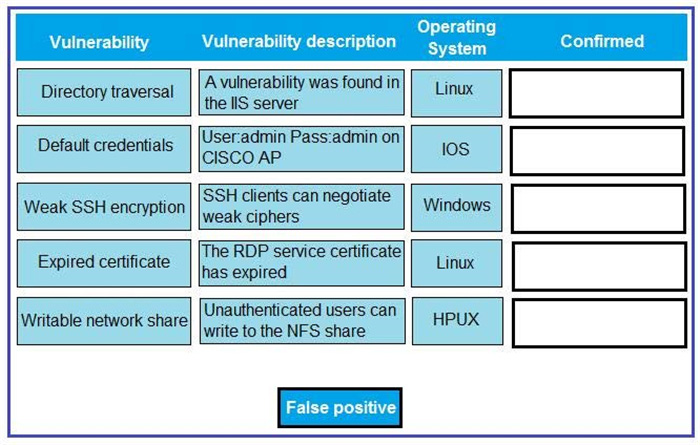
Question 42:
DRAG DROP
A technician is reviewing the following report. Given this information, identify which vulnerability can be definitively confirmed to be a false positive by dragging the “false positive” token to the “Confirmed” column for each vulnerability that is a false positive.
Select and Place:
-
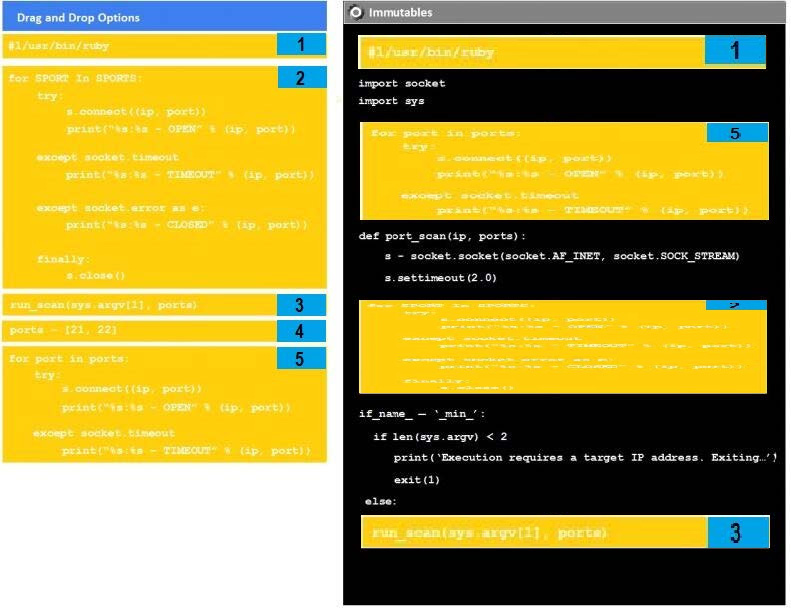
Question 43:
DRAG DROP
Instructions:
Analyze the code segments to determine which sections are needed to complete a port scanning script. Drag the appropriate elements into the correct locations to complete the script.
If at any time you would like to bring back the initial state of the simulation, please click the reset all button.
During a penetration test, you gain access to a system with a limited user interface. This machine appears to have access to an isolated network that you would like to port scan.
Select and Place:
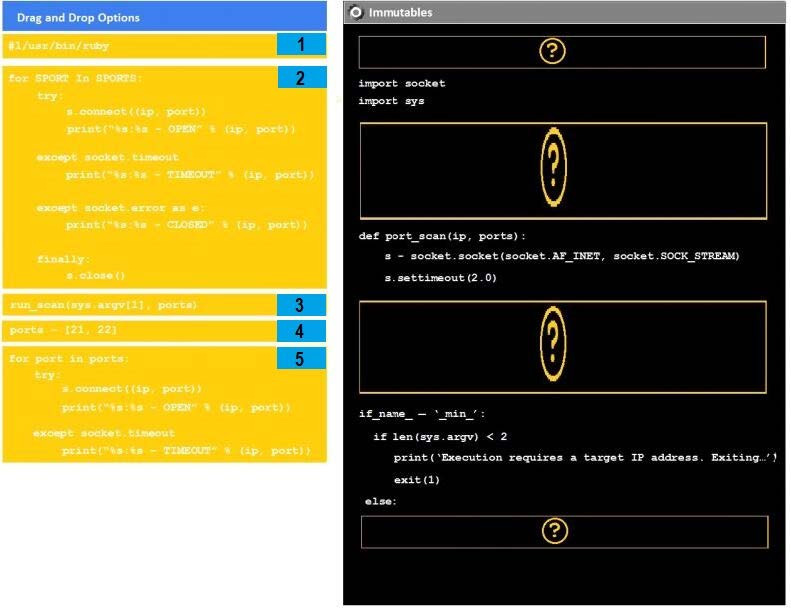
-
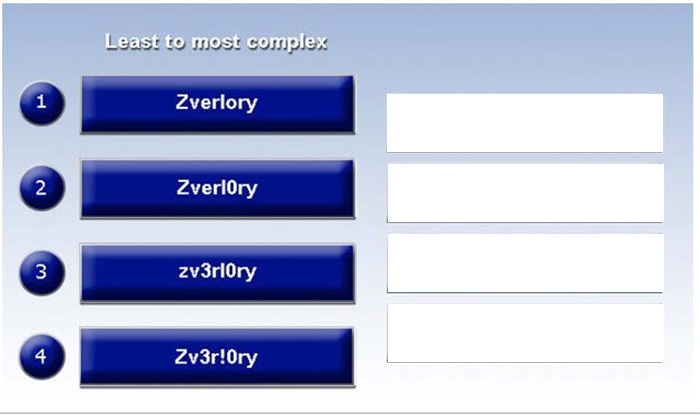
Question 44:
Place each of the following passwords in order of complexity from least complex (1) to most complex (4), based on the character sets represented Each password may be used only once.
Select and Place:
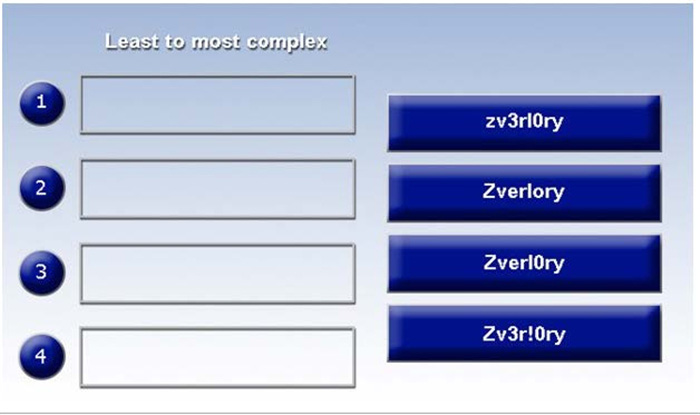
-
Question 45:
A manager calls upon a tester to assist with diagnosing an issue within the following:
Python script: #!/usr/bin/python s = “Administrator”
The tester suspects it is an issue with string slicing and manipulation Analyze the following code segment and drag and drop the correct output for each string manipulation to its corresponding code segment Options may be used once or not at all.
Select and Place:

-
Question 46:
SIMULATION
You are a penetration tester running port scans on a server.
INSTRUCTIONS
Part 1: Given the output, construct the command that was used to generate this output from the available options.
Part 2: Once the command is appropriately constructed, use the given output to identify the potential attack vectors that should be investigated further.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
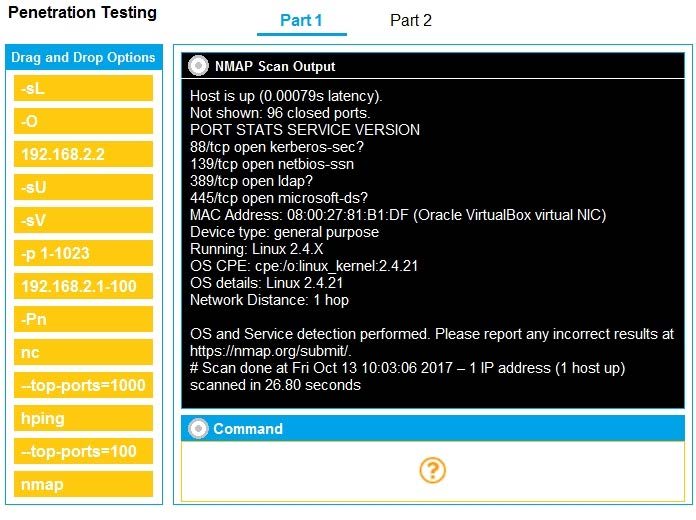
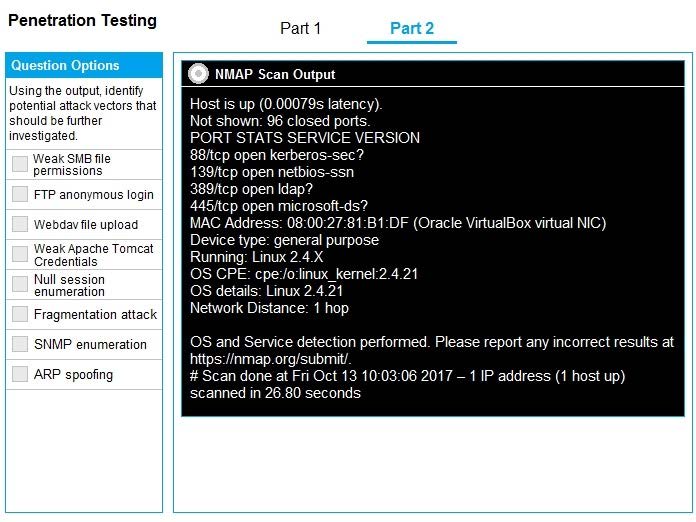
A.
-
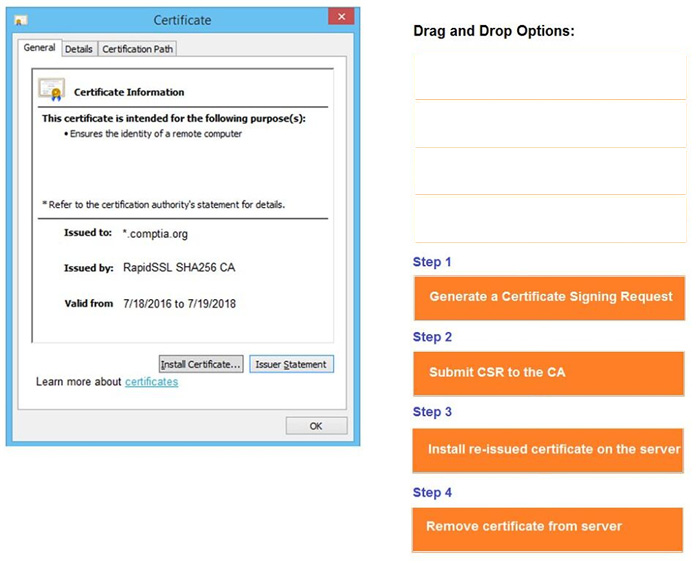
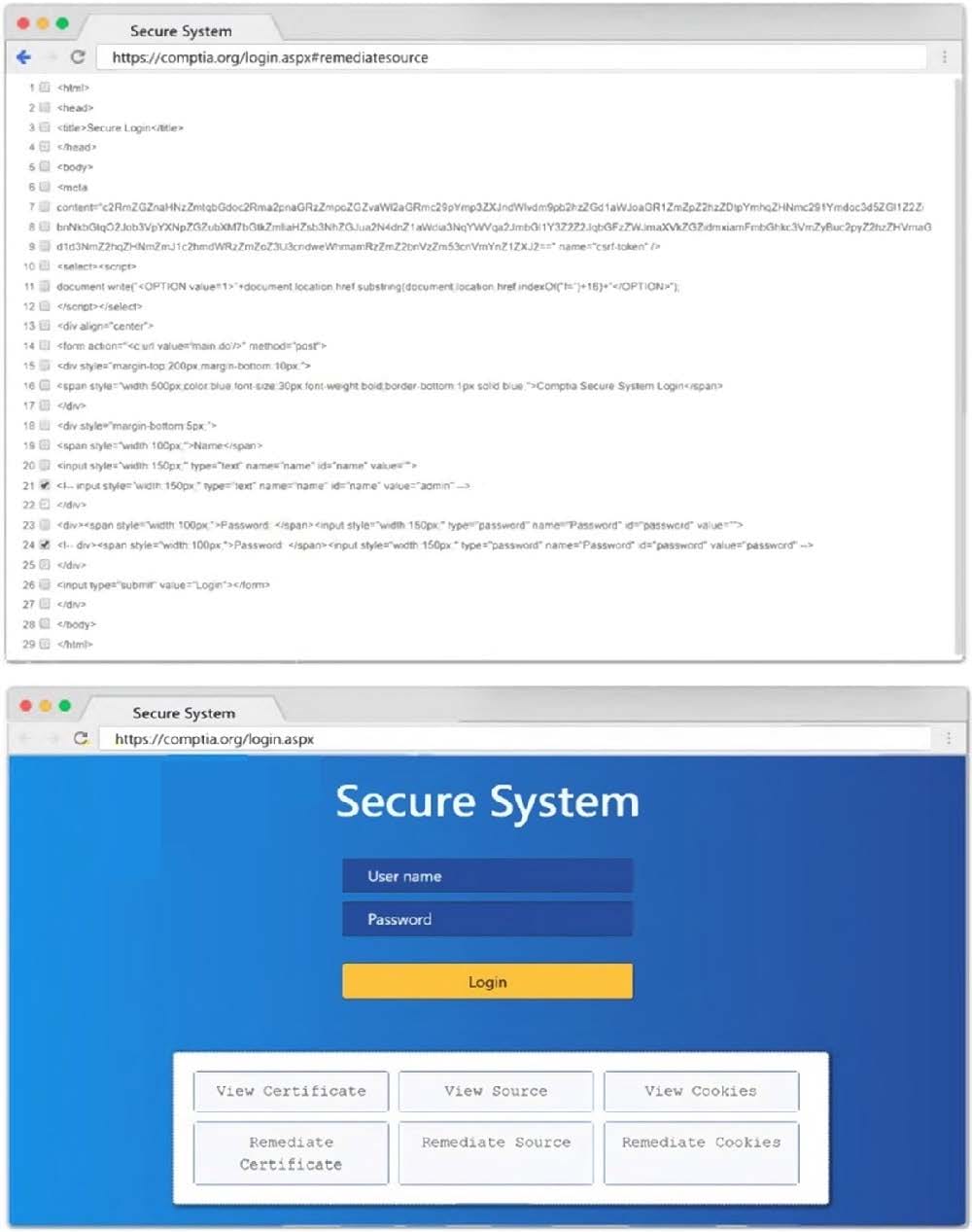
Question 47:
DRAG DROP
You are a penetration tester reviewing a client's website through a web browser.
INSTRUCTIONS
Review all components of the website through the browser to determine if vulnerabilities are present.
Remediate ONLY the highest vulnerability from either the certificate, source, or cookies.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
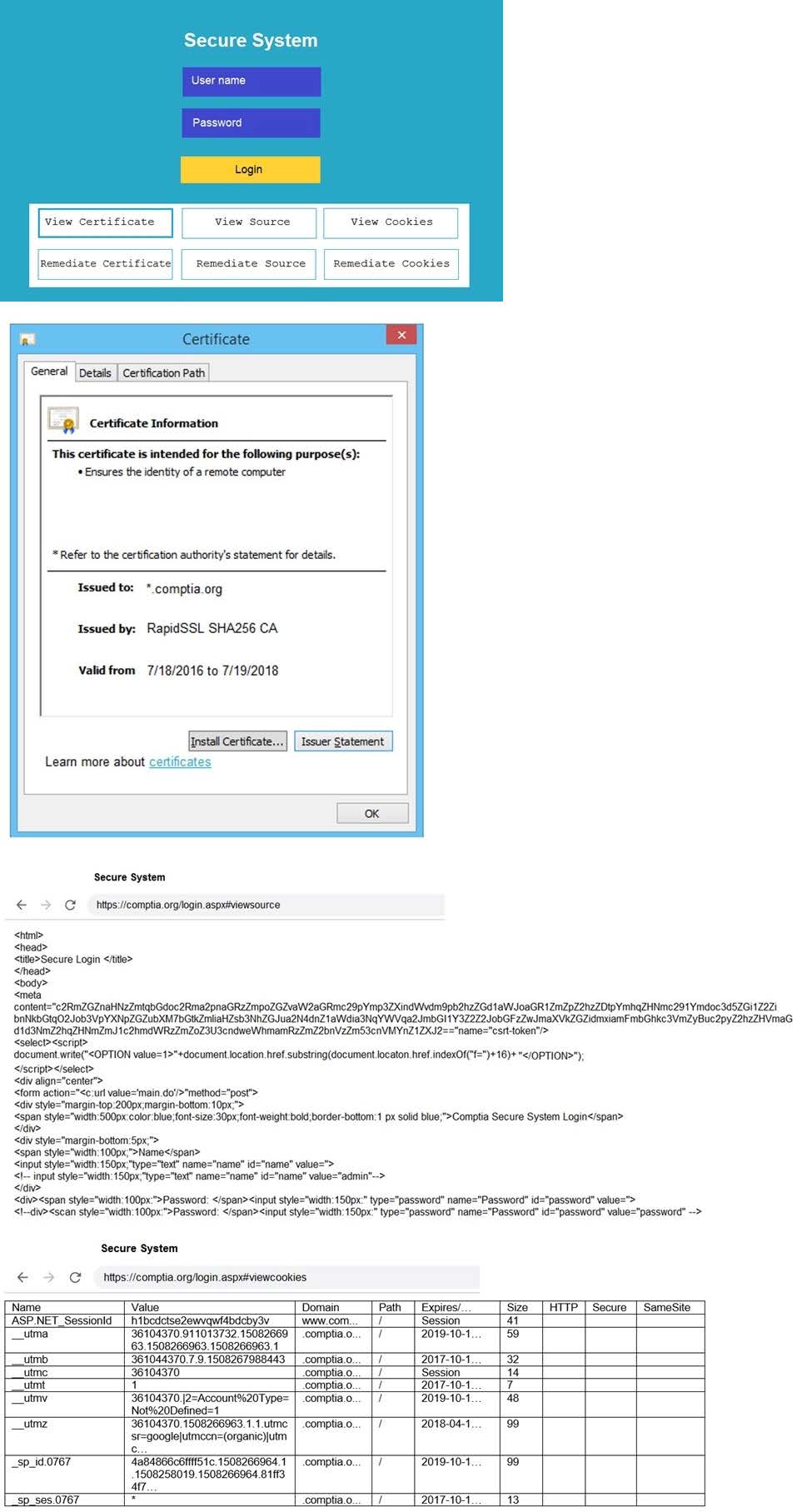
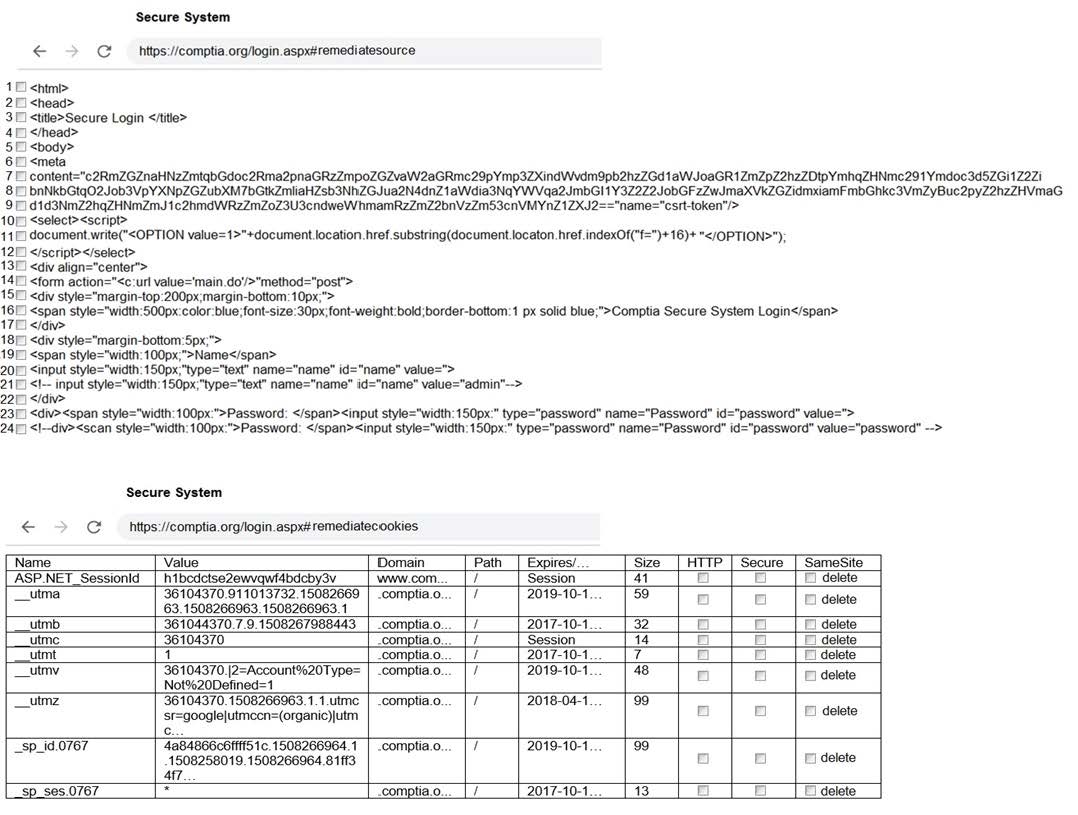
Select and Place:
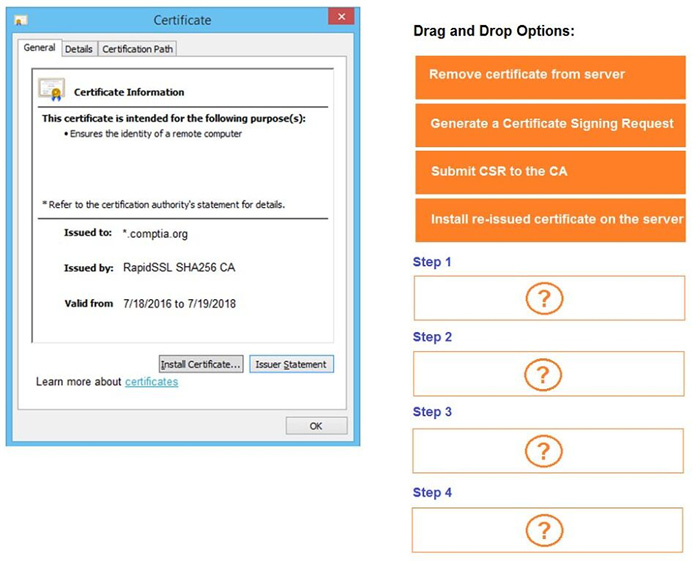
-
Question 48:
HOTSPOT
You are a security analyst tasked with hardening a web server.
You have been given a list of HTTP payloads that were flagged as malicious.
INSTRUCTIONS
Given the following attack signatures, determine the attack type, and then identify the associated remediation to prevent the attack in the future.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
Hot Area:
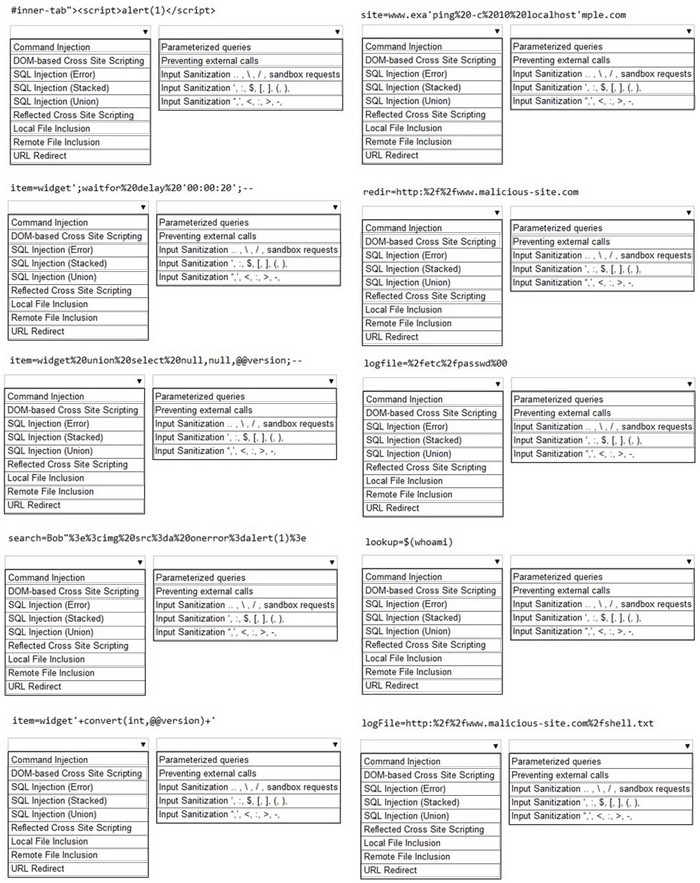
-
Question 49:
A penetration tester fuzzes an internal server looking for hidden services and applications and obtains the following output:
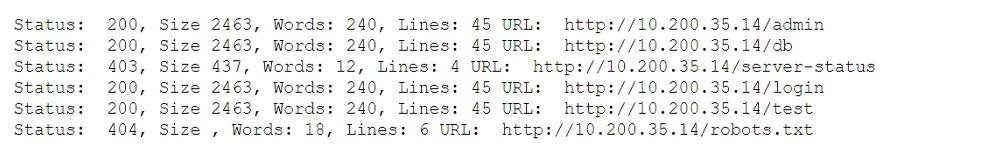
Which of the following is the most likely explanation for the output?
A. The tester does not have credentials to access the server-status page.
B. The admin directory cannot be fuzzed because it is forbidden.
C. The admin, test, and db directories redirect to the log-in page.
D. The robots.txt file has six entries in it.
-
Question 50:
Which of the following web-application security risks are part of the OWASP Top 10 v2017? (Choose two.)
A. Buffer overflows
B. Cross-site scripting
C. Race-condition attacks
D. Zero-day attacks
E. Injection flaws
F. Ransomware attacks
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-1202
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your PT0-002 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.