Exam Details
Exam Code
:PT0-002Exam Name
:CompTIA PenTest+Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:455 Q&AsLast Updated
:Aug 07, 2025
CompTIA CompTIA Certifications PT0-002 Questions & Answers
-
Question 1:
HOTSPOT
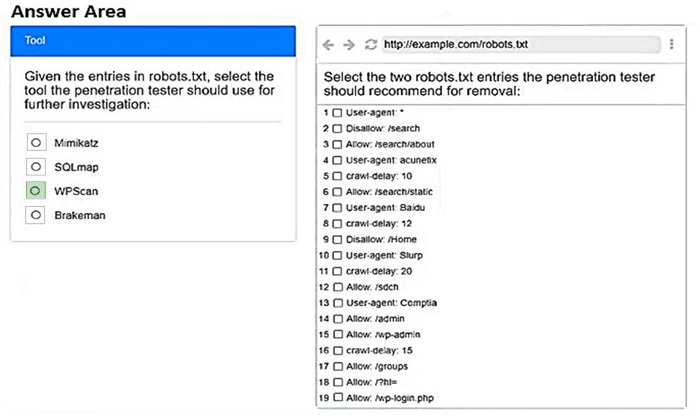
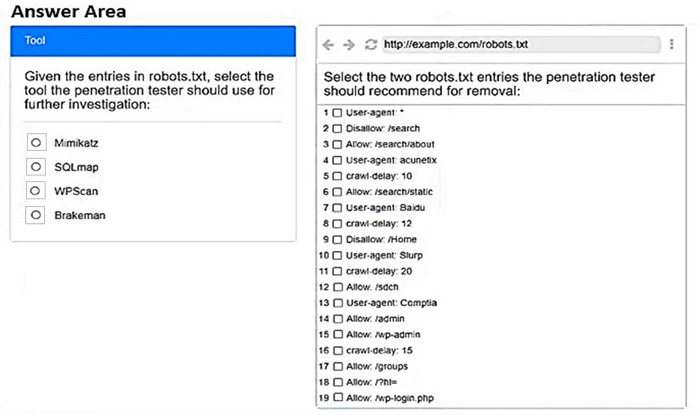
A penetration tester is performing reconnaissance for a web application assessment. Upon investigation, the tester reviews the robots.txt file for items of interest.
INSTRUCTIONS
Select the tool the penetration tester should use for further investigation.
Select the two entries in the robots.txt file that the penetration tester should recommend for removal.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
Hot Area:
-
Question 2:
A penetration tester is conducting an unknown environment test and gathering additional information that can be used for later stages of an assessment. Which of the following would most likely produce useful information for additional testing?
A. Searching for code repositories associated with a developer who previously worked for the target company code repositories associated with the
B. Searching for code repositories target company's organization
C. Searching for code repositories associated with the target company's organization
D. Searching for code repositories associated with a developer who previously worked for the target company
-
Question 3:
User credentials were captured from a database during an assessment and cracked using rainbow tables. Based on the ease of compromise, which of the following algorithms was MOST likely used to store the passwords in the database?
A. MD5
B. bcrypt
C. SHA-1
D. PBKDF2
-
Question 4:
A tester who is performing a penetration test on a website receives the following output:
Warning: mysql_fetch_array() expects parameter 1 to be resource, boolean given in /var/www/search.php on line 62
Which of the following commands can be used to further attack the website?
A.
B. ../../../../../../../../../../etc/passwd
C. /var/www/html/index.php;whoami
D. 1 UNION SELECT 1, DATABASE(),3-
-
Question 5:
A penetration tester ran an Nmap scan on an Internet-facing network device with the –F option and found a few open ports. To further enumerate, the tester ran another scan using the following command:
nmap –O –A –sS –p- 100.100.100.50
Nmap returned that all 65,535 ports were filtered. Which of the following MOST likely occurred on the second scan?
A. A firewall or IPS blocked the scan.
B. The penetration tester used unsupported flags.
C. The edge network device was disconnected.
D. The scan returned ICMP echo replies.
-
Question 6:
A penetration tester needs to access a building that is guarded by locked gates, a security team, and cameras. Which of the following is a technique the tester can use to gain access to the IT framework without being detected?
A. Pick a lock.
B. Disable the cameras remotely.
C. Impersonate a package delivery worker.
D. Send a phishing email.
-
Question 7:
A tester who is performing a penetration test discovers an older firewall that is known to have serious vulnerabilities to remote attacks but is not part of the original list of IP addresses for the engagement. Which of the following is the BEST option for the tester to take?
A. Segment the firewall from the cloud.
B. Scan the firewall for vulnerabilities.
C. Notify the client about the firewall.
D. Apply patches to the firewall.
-
Question 8:
A penetration tester wrote the following script on a compromised system:
#!/bin/bash
network='10.100.100'
ports='22 23 80 443'
for x in {1 .. 254};
do (nc -zv $network.$x $ports );
done
Which of the following would explain using this script instead of another tool?
A. The typical tools could not be used against Windows systems.
B. The configuration required the penetration tester to not utilize additional files.
C. The Bash script will provide more thorough output.
D. The penetration tester wanted to persist this script to run on reboot.
-
Question 9:
A penetration tester completed an assessment, removed all artifacts and accounts created during the test, and presented the findings to the client. Which of the following happens NEXT?
A. The penetration tester conducts a retest.
B. The penetration tester deletes all scripts from the client machines.
C. The client applies patches to the systems.
D. The client clears system logs generated during the test.
-
Question 10:
Which of the following assessment methods is the most likely to cause harm to an ICS environment?
A. Active scanning
B. Ping sweep
C. Protocol reversing
D. Packet analysis
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-1202
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your PT0-002 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.