Exam Details
Exam Code
:PCNSEExam Name
:Palo Alto Networks Certified Network Security Engineer - PAN-OS 11.x (PCNSE)Certification
:Palo Alto Networks CertificationsVendor
:Palo Alto NetworksTotal Questions
:860 Q&AsLast Updated
:Aug 19, 2025
Palo Alto Networks Palo Alto Networks Certifications PCNSE Questions & Answers
-
Question 201:
Review the information below. A firewall engineer creates a U-NAT rule to allow users in the trust zone access to a server in the same zone by using an external, public NAT IP for that server.
Given the rule below, what change should be made to make sure the NAT works as expected?
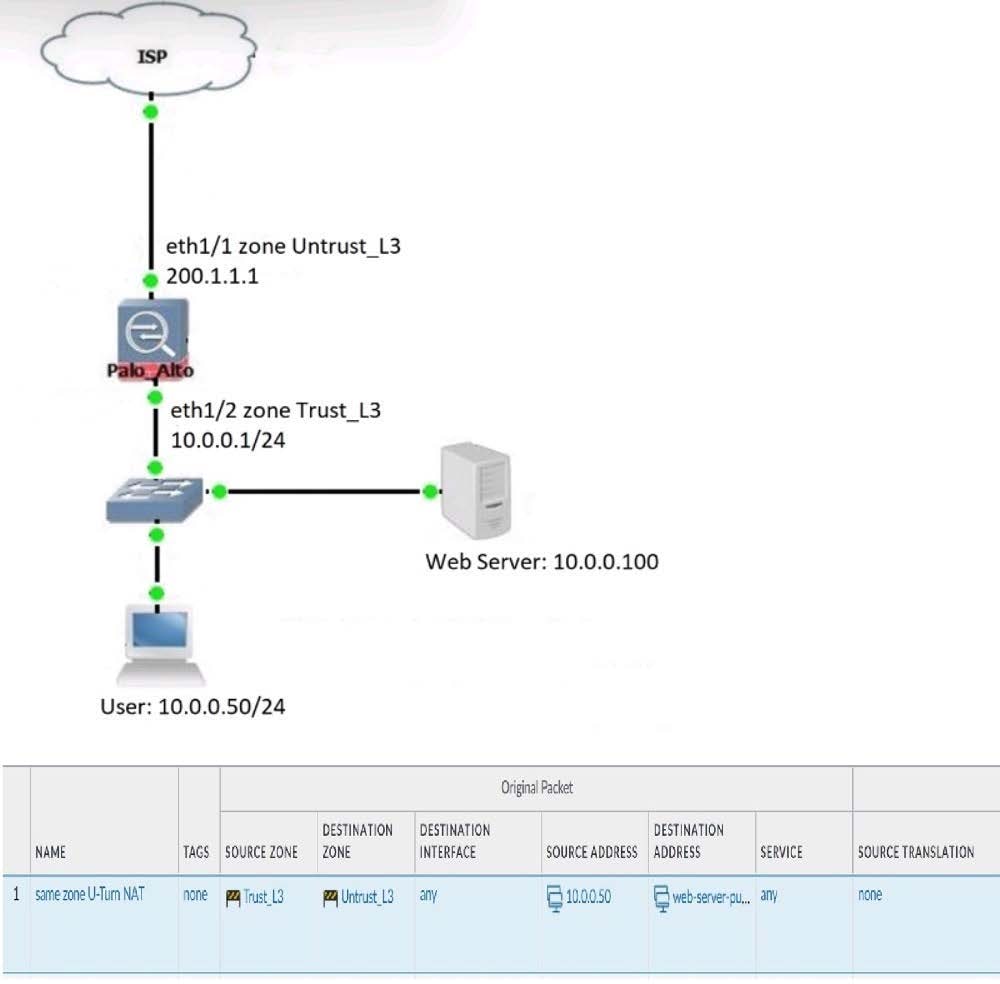
A. Change destination NAT zone to Trust_L3.
B. Change destination translation to Dynamic IP (with session distribution) using firewall ethI/2 address.
C. Change Source NAT zone to Untrust_L3.
D. Add source Translation to translate original source IP to the firewall eth1/2 interface translation.
-
Question 202:
An engineer manages a high availability network and requires fast failover of the routing protocols. The engineer decides to implement BFD. Which three dynamic routing protocols support BFD? (Choose three.)
A. OSPF
B. RIP
C. BGP
D. IGRP
E. OSPFv3 virtual link
-
Question 203:
An administrator is troubleshooting why video traffic is not being properly classified. If this traffic does not match any QoS classes, what default class is assigned?
A. 1
B. 2
C. 3
D. 4
-
Question 204:
An ISP manages a Palo Alto Networks firewall with multiple virtual systems for its tenants.
Where on this firewall can the ISP configure unique service routes for different tenants?
A. Setup > Services > Virtual Systems > Set Location > Service Route Configuration > Inherit Global Service Route Configuration
B. Setup > Services > Global > Service Route Configuration > Customize
C. Setup > Services > Virtual Systems > Set Location > Service Route Configuration > Customize
D. Setup > Services > Global > Service Route Configuration > Use Management Interface for all
-
Question 205:
When using SSH keys for CLI authentication for firewall administration, which method is used for authorization?
A. Local
B. LDAP
C. Kerberos
D. Radius
-
Question 206:
An engineer reviews high availability (HA) settings to understand a recent HA failover event. Review the screenshot below.
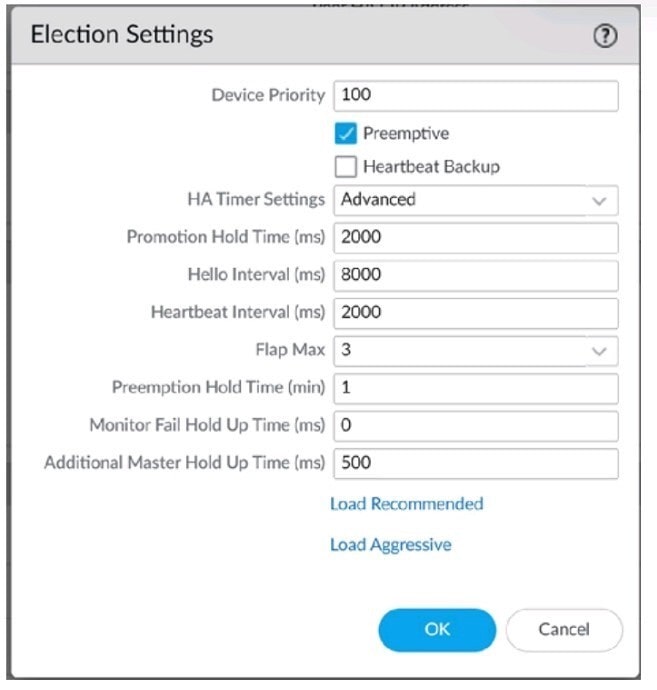
Which timer determines the frequency at which the HA peers exchange messages in the form of an ICMP (ping)
A. Hello Interval
B. Promotion Hold Time
C. Heartbeat Interval
D. Monitor Fail Hold Up Time
-
Question 207:
An administrator connected a new fiber cable and transceiver to interface Ethernetl/l on a Palo Alto Networks firewall. However, the link does not seem to be coming up.
If an administrator were to troubleshoot, how would they confirm the transceiver type, tx-power, rx-power, vendor name, and part number via the CLI?
A. show system state filter sw.dev.interface.config
B. show chassis status slot s1
C. show system state filter-pretty sys.s1.*
D. show system state filter ethernet1/1
-
Question 208:
Which DoS Protection Profile detects and prevents session exhaustion attacks against specific destinations?
A. Resource Protection
B. TCP Port Scan Protection
C. Packet Based Attack Protection
D. Packet Buffer Protection
-
Question 209:
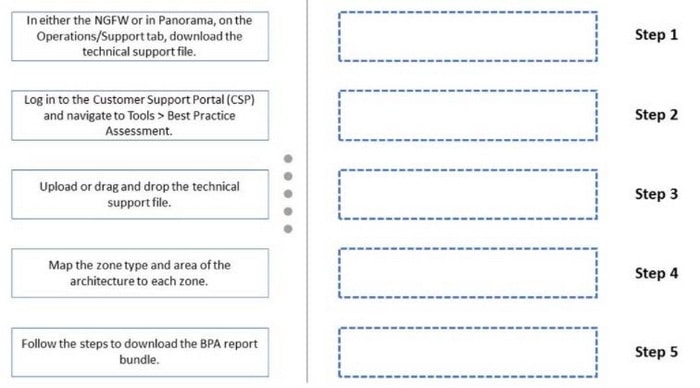
DRAG DROP
Below are the steps in the workflow for creating a Best Practice Assessment in a firewall and Panorama configuration Place the steps in order.
Select and Place:
-
Question 210:
DRAG DROP
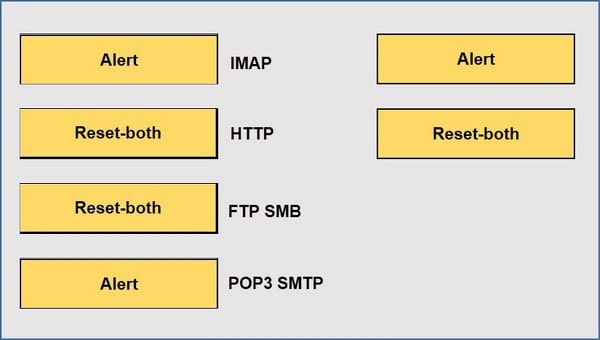
When using the predefined default profile, the policy will inspect for viruses on the decoders. Match each decoder with its default action. Answer options may be used more than once or not at all.
Select and Place:
Related Exams:
PAN-NGFE
Palo Alto Networks Network Next-Generation Firewall EngineerPAN-NSG
Palo Alto Networks Network Security GeneralistPAN-NSP
Palo Alto Networks Network Security ProfessionalPAN-SSEE
Palo Alto Networks Security Service Edge EngineerPAN-XDRE
Palo Alto Networks XDR EngineerPCCET
Palo Alto Networks Certified Cybersecurity Entry-level Technician (PCCET)PCCSA
Palo Alto Networks Certified Cybersecurity Associate (PCCSA)PCCSE
Prisma Certified Cloud Security Engineer (PCCSE)PCDRA
Palo Alto Networks Certified Detection and Remediation Analyst (PCDRA)PCNSA
Palo Alto Networks Certified Network Security Administrator (PCNSA)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Palo Alto Networks exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your PCNSE exam preparations and Palo Alto Networks certification application, do not hesitate to visit our Vcedump.com to find your solutions here.