Exam Details
Exam Code
:PCNSEExam Name
:Palo Alto Networks Certified Network Security Engineer - PAN-OS 11.x (PCNSE)Certification
:Palo Alto Networks CertificationsVendor
:Palo Alto NetworksTotal Questions
:860 Q&AsLast Updated
:Aug 19, 2025
Palo Alto Networks Palo Alto Networks Certifications PCNSE Questions & Answers
-
Question 191:
A firewall administrator has confirm reports of a website is not displaying as expected, and wants to ensure that decryption is not causing the issue.
Which three methods can the administrator use to determine if decryption is causing the website to fail? (Choose three.)
A. Disable SSL handshake logging
B. Investigate decryption logs of the specific traffic to determine reasons for failure.
C. Temporarily disable SSL decryption for all websites to troubleshoot the issue
D. Create a policy-based "No Decrypt" rule in the decryption policy to include specific traffic from decryption.
E. Move the policy with action decrypt to the top of the decryption policy rulebase.
-
Question 192:
All firewall at a company are currently forwarding logs to Palo Alto Networks log collectors. The company also wants to deploy a sylog server and forward all firewall logs to the syslog server and to the log collectors. There is known logging peak time during the day, and the security team has asked the firewall engineer to determined how many logs per second the current Palo Alto Networking log processing at that particular time.
Which method is the most time-efficient to complete this task?
A. Navigate to Panorama > Managed Collectors, and open the Statistics windows for each Log Collector during the peak time.
B. Navigate to Monitor > Unified logs, set the filter to the peak time, and browse to the last page to find out how many logs have been received.
C. Navigate to Panorama> Managed Devices> Health, open the Logging tab for each managed firewall and check the log rates during the peak time.
D. Navigate to ACC> Network Activity, and determine the total number of sessions and threats during the peak time.
-
Question 193:
A firewall administrator is configuring an IPSec tunnel between a company's HQ and a remote location. On the HQ firewall, the interface used to terminate the IPSec tunnel has a static IP. At the remote location, the interface used to terminate the IPSec tunnel has a DHCP assigned IP address.
Which two actions are required for this scenario to work? (Choose two.)
A. On the HQ firewall select peer IP address type FQDN
B. On the remote location firewall select peer IP address type Dynamic
C. On the HQ firewall enable DDNS under the interface used for the IPSec tunnel
D. On the remote location firewall enable DONS under the interface used for the IPSec tunnel
-
Question 194:
The firewall team has been asked to deploy a new Panorama server and to forward all firewall logs to this server By default, which component of the Palo Alto Networks firewall architect is responsible for log forwarding and should be checked for early signs of overutilization?
A. Management plane CPU
B. Dataplane CPU
C. Packet buffers
D. On-chip packet descriptors
-
Question 195:
Which function does the HA4 interface provide when implementing a firewall cluster which contains firewalls configured as active-passive pairs?
A. Perform packet forwarding to the active-passive peer during session setup and asymmetric traffic flow.
B. Perform synchronization of routes, IPSec security associations, and User-ID information.
C. Perform session cache synchronization for all HA cluster members with the same cluster ID.
D. Perform synchronization of sessions, forwarding tables, and IPSec security associations between firewalls in an HA pair.
-
Question 196:
What must be configured to apply tags automatically based on User-ID logs?
A. Log Forwarding profile
B. Device ID
C. Log settings
D. Group mapping
-
Question 197:
A firewall engineer is tasked with defining signatures for a custom application.
Which two sources can the engineer use to gather information about the application patterns'? (Choose two.)
A. Traffic logs
B. Data filtering logs
C. Policy Optimizer
D. Wireshark
-
Question 198:
Which two factors should be considered when sizing a decryption firewall deployment? (Choose two.)
A. Number of blocked sessions
B. TLS protocol version
C. Encryption algorithm
D. Number of security zones in decryption policies
-
Question 199:
A firewall engineer reviews the PAN-OS GlobalProtect application and sees that it implicitly uses web-browsing and depends on SSL. When creating a new rule, what is needed to allow the application to resolve dependencies?
A. Add SSL and web-browsing applications to the same rule.
B. Add web-browsing application to the same rule.
C. Add SSL application to the same rule.
D. SSL and web-browsing must both be explicitly allowed.
-
Question 200:
Given the screenshot, how did the firewall handle the traffic?
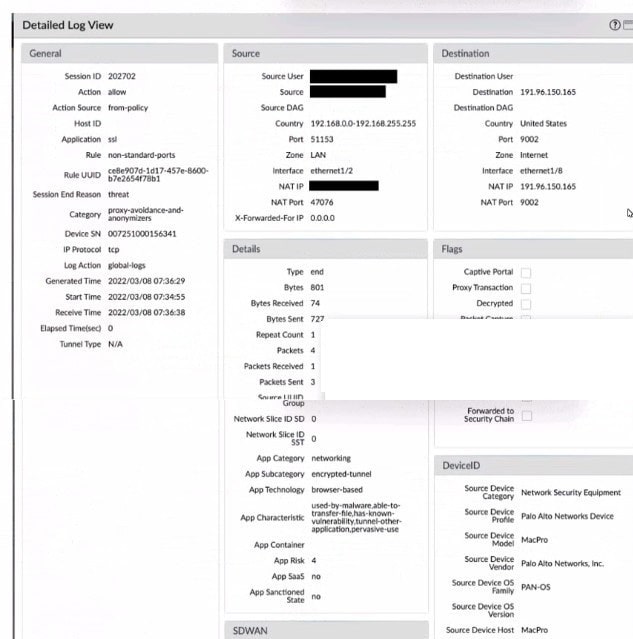
A. Traffic was allowed by policy but denied by profile as encrypted.
B. Traffic was allowed by policy but denied by profile as a threat.
C. Traffic was allowed by profile but denied by policy as a threat.
D. Traffic was allowed by policy but denied by profile as a nonstandard port.
Related Exams:
PAN-NGFE
Palo Alto Networks Network Next-Generation Firewall EngineerPAN-NSG
Palo Alto Networks Network Security GeneralistPAN-NSP
Palo Alto Networks Network Security ProfessionalPAN-SSEE
Palo Alto Networks Security Service Edge EngineerPAN-XDRE
Palo Alto Networks XDR EngineerPCCET
Palo Alto Networks Certified Cybersecurity Entry-level Technician (PCCET)PCCSA
Palo Alto Networks Certified Cybersecurity Associate (PCCSA)PCCSE
Prisma Certified Cloud Security Engineer (PCCSE)PCDRA
Palo Alto Networks Certified Detection and Remediation Analyst (PCDRA)PCNSA
Palo Alto Networks Certified Network Security Administrator (PCNSA)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Palo Alto Networks exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your PCNSE exam preparations and Palo Alto Networks certification application, do not hesitate to visit our Vcedump.com to find your solutions here.