PCNSE Exam Details
-
Exam Code
:PCNSE -
Exam Name
:Palo Alto Networks Certified Network Security Engineer - PAN-OS 11.x (PCNSE) -
Certification
:Palo Alto Networks Certifications -
Vendor
:Palo Alto Networks -
Total Questions
:860 Q&As -
Last Updated
:Jan 16, 2026
Palo Alto Networks PCNSE Online Questions & Answers
-
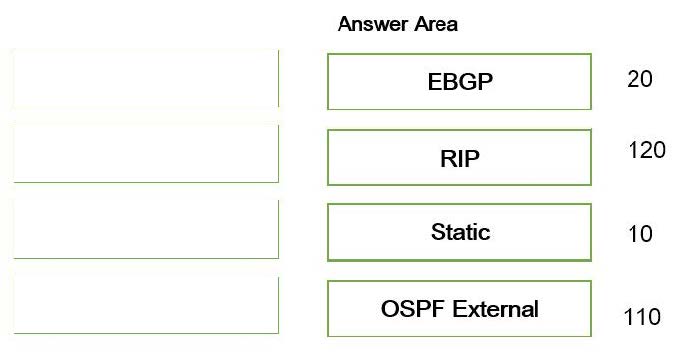
Question 1:
DRAG DROP
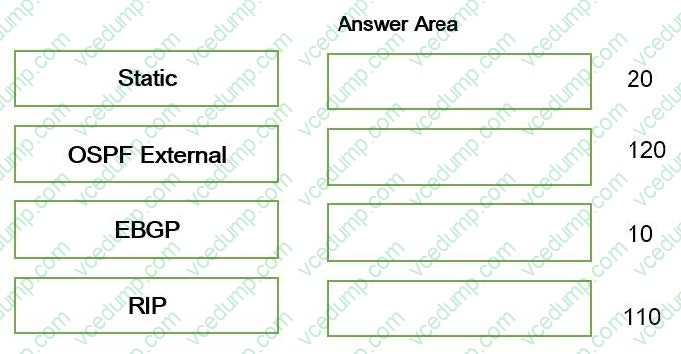
An engineer is troubleshooting traffic routing through the virtual router. The firewall uses multiple routing protocols, and the engineer is trying to determine routing priority.
Match the default Administrative Distances for each routing protocol.
Select and Place:
-
Question 2:
DRAG DROP
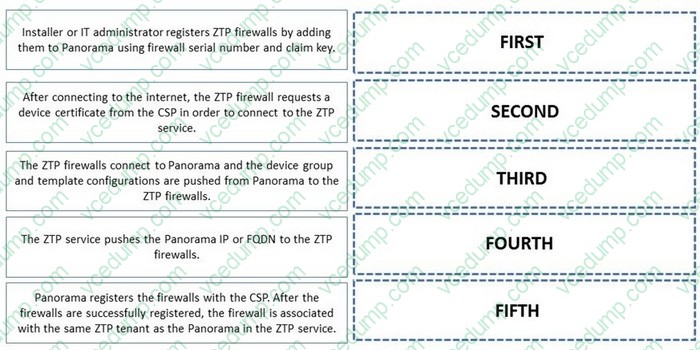
Place the steps to onboard a ZTP firewall into Panorama/CSP/ZTP-Service in the correct order.
Select and Place:
-
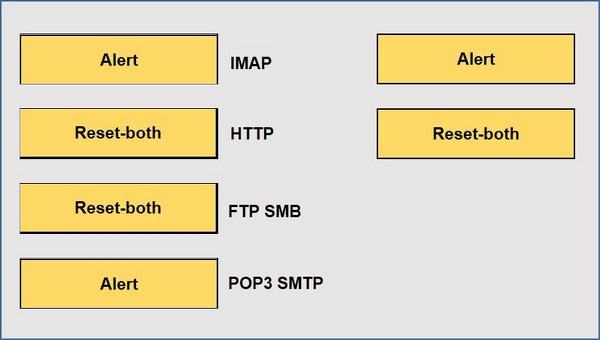
Question 3:
DRAG DROP
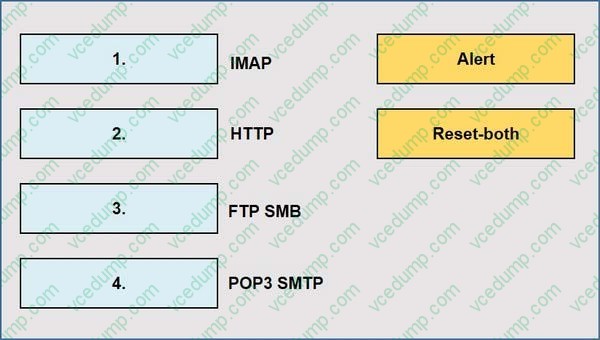
When using the predefined default profile, the policy will inspect for viruses on the decoders. Match each decoder with its default action. Answer options may be used more than once or not at all.
Select and Place:
-
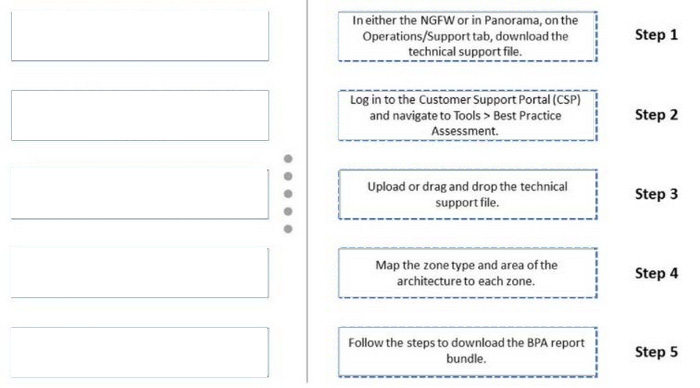
Question 4:
DRAG DROP
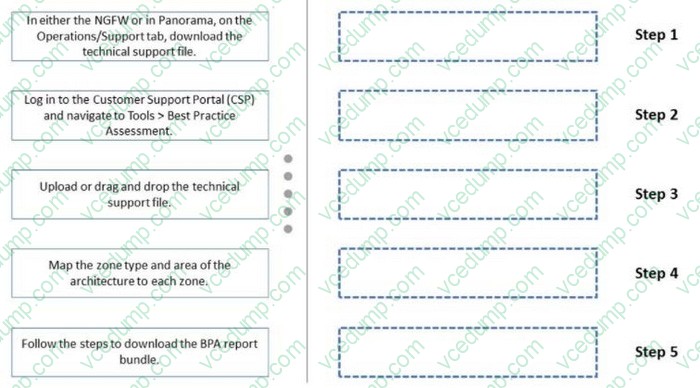
Below are the steps in the workflow for creating a Best Practice Assessment in a firewall and Panorama configuration Place the steps in order.
Select and Place:
-
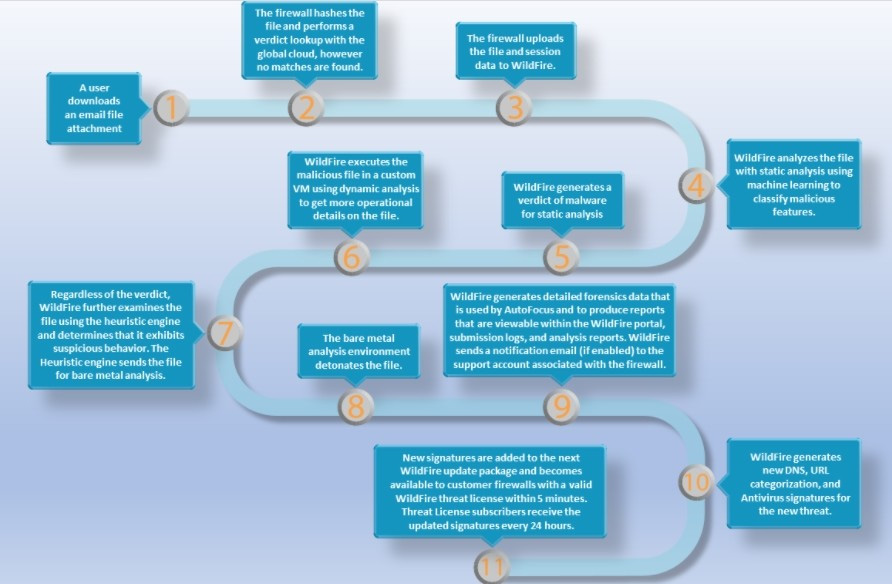
Question 5:
DRAG DROP
Place the steps in the WildFire process workflow in their correct order.
Select and Place:
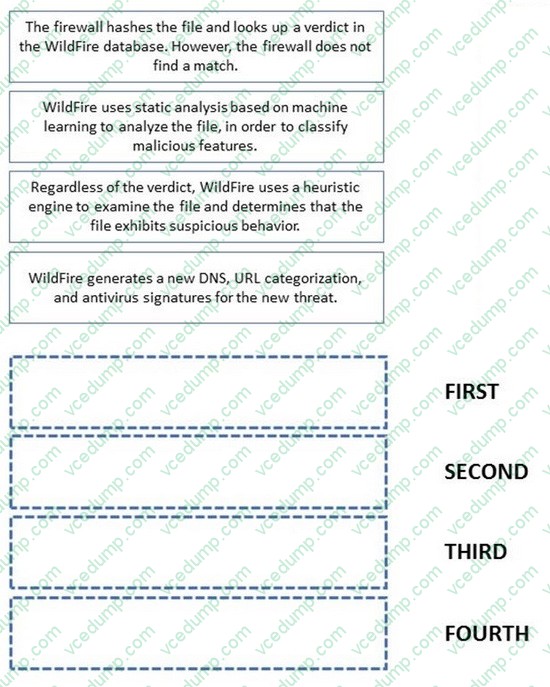
-
Question 6:
What is the benefit of the Artificial Intelligence Operations (AIOps) Plugin for Panorama?
A. It automatically pushes the configuration to Panorama after strengthening the overall security posture
B. It proactively enforces best practices by validating new commits and advising if a policy needs work before pushing it to Panorama
C. The AIOps plugin in Panorama auto-corrects the security rules that failed the Best Practice Assessment
D. The AIOps plugin in Panorama retroactively checks the policy changes during the commits -
Question 7:
A firewall architect is attempting to install a new Palo Alto Networks NGFW. The company has previously had issues moving all administrative functions onto a data plane interface to meet the design limitations of the environment. The architect is able to access the device for HTTPS and SSH; however, the NGFW can neither validate licensing nor get updates. Which action taken by the architect will resolve this issue?
A. Create a service route that sets the source interface to the data plane interface in question
B. Validate that all upstream devices will allow and properly route the outbound traffic to the external destinations needed
C. Create a loopback from the management interface to the data plane interface, then make a service route from the management interface to the data plane interface
D. Enable OCSP for the data plane interface so the firewall will create a certificate with the data plane interface's IP -
Question 8:
A customer wants to enhance the protection provided by their Palo Alto Networks NGFW deployment to cover public-facing company-owned domains from misconfigurations that point records to third-party sources. Which two actions should the network administrator perform to achieve this goal? (Choose two)
A. Verify the NGFWs have the Advanced DNS Security and Advanced Threat Prevention licenses installed and validated
B. Create or update a Vulnerability Protection profile to the DNS Policies / DNS Zone Misconfiguration section, then add the domains to be protected
C. Verify the NGFWs have the Advanced DNS Security and Advanced URL Filtering licenses installed and validated
D. Create or update an Anti-Spyware profile, go to the DNS Policies / DNS Zone Misconfiguration section, then add the domains to be protected -
Question 9:
How can a firewall be set up to automatically block users as soon as they are found to exhibit malicious behavior via a threat log?
A. Configure a dynamic address group for the addresses to be blocked with the tag "malicious." Add a Log Forwarding profile to the other policies, which adds the "malicious" tag to these addresses when logs are generated in the threat log. Under Device > User Identification > Trusted Source Address, add the condition "NOT malicious."
B. Configure a dynamic user group for the users to be blocked with the tag "malicious." Add a Log Forwarding profile to the other policies, which adds the "malicious" tag to these users when logs are generated in the threat log. Create policies to block traffic from this user group.
C. Configure the appropriate security profiles for Antivirus, Anti-Spyware, and Vulnerability Prevention, create signature policies for the relevant signatures and/or severities. Under the "Actions" tab in "Signature Policies," select "block-user."
D. N/A -
Question 10:
What must be taken into consideration when preparing a log forwarding design for all of a customer's deployed Palo Alto Networks firewalls?
A. The logs will not contain the names of the identified applications unless the "Enable enhanced application logging" option is selected
B. Traffic and threat logs will not be forwarded unless the relevant Log Forwarding profile is attached to the security rules
C. App-ID engine will not identify any application traffic unless the "Enable enhanced application logging" option is selected
D. Traffic and threat logs will not be forwarded unless the relevant Log Forwarding profile is selected in "Logging and Reporting Settings"
Related Exams:
-
PAN-NGFE
Palo Alto Networks Network Next-Generation Firewall Engineer -
PAN-NSA
Palo Alto Networks Network Security Analyst -
PAN-NSG
Palo Alto Networks Network Security Generalist -
PAN-NSP
Palo Alto Networks Network Security Professional -
PAN-SSEE
Palo Alto Networks Security Service Edge Engineer -
PAN-XDRA
Palo Alto Networks XDR Analyst -
PAN-XDRE
Palo Alto Networks XDR Engineer -
PAN-XSIAMA
Palo Alto Networks XSIAM Analyst -
PAN-XSIAME
Palo Alto Networks XSIAM Engineer -
PAN-XSOARE
Palo Alto Networks XSOAR Engineer
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Palo Alto Networks exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your PCNSE exam preparations and Palo Alto Networks certification application, do not hesitate to visit our Vcedump.com to find your solutions here.