Exam Details
Exam Code
:PCNSCExam Name
:Palo Alto Networks Certified Network Security Consultant (PCNSC)Certification
:Palo Alto Networks CertificationsVendor
:Palo Alto NetworksTotal Questions
:141 Q&AsLast Updated
:Aug 13, 2025
Palo Alto Networks Palo Alto Networks Certifications PCNSC Questions & Answers
-
Question 41:
How would an administrator monitor/capture traffic on the management interface of the Palo Alto Networks NGFW?
A. Use the tcpdump command
B. Use the debug dataplane packet-diag set capture stage management file command
C. USe the debug dataplane packet-dia set capture stage firewall file command
D. Enable all four stage of traffic capture (TX, RX, DROP, Firewall)
-
Question 42:
The firewall identified a popular application as a unknown-tcp. Which options are available to identify the application? (Choose two.)
A. Create a Security policy to identify the customer application.
B. Create a customer object for the customer application server to identify the custom application.
C. Submit an App-ID request to Palo Alto Networks.
D. Create a custom application.
-
Question 43:
Which two methods can be configured to validate the revocation status of a certificate? (Choose two)
A. CRL
B. Cert-Validation-Profile
C. OCSP
D. CRT
E. SSL /TLS Service Profile
-
Question 44:
Refer to the exhibit.

An administrator cannot see any of the Traffic logs from the Palo Alto Networks NGFW on Panorama. The configuration problem seems to be on the firewall side. Where is the best place on the Palo Alto Networks NGFW to check whether the configuration is correct?
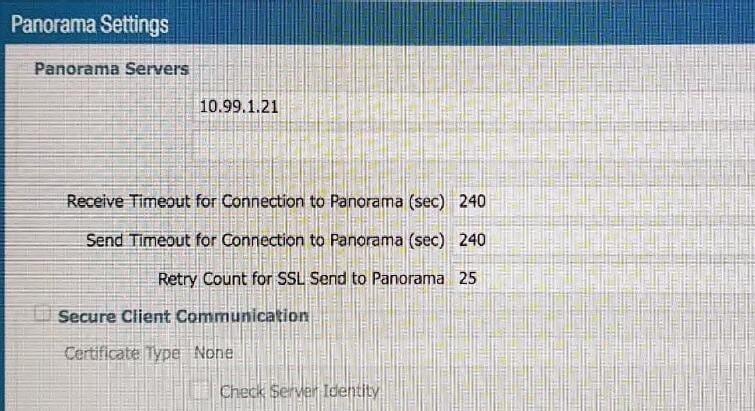
A.

B. C. D.
-
Question 45:
Which version of Global Protect supports split tunneling based on destination domain, client process, and HTTP/HTTPs video streaming application?
A. Glovbalprotect version 4.0 with PAn-OS 8.0
B. Glovbalprotect version 4.1 with PAn-OS 8.1
C. Glovbalprotect version 4.0 with PAn-OS 8.1
D. Glovbalprotect version 4.1 with PAn-OS 8.0
-
Question 46:
An administrator pushes a new configuration from panorama to a pair of firewalls that are configured as active/passive HA pair. Which NGFW receives the configuration from panorama?
A. the active firewall, which then synchronizes to the passive firewall
B. the passive firewall, which then synchronizes to the active firewall
C. both the active and passive firewalls independently, with no synchronization afterward
D. both the active and passive firewalls, which then synchronizes with each other
-
Question 47:
A client has a sensitive application server in their data center and is particularly concerned about resource exhaustion because of distributed denial-of-service attacks.
A. Define a custom App-ID to ensure that only legitimate application traffic reaches the server
B. Add a DoS Protection Profile with defined session count.
C. Add a Vulnerability Protection Profile to block the attack.
D. Add QoS Profiles to throttle incoming requests.
-
Question 48:
Which processing order will be enabled when a panorama administrator selects the setting "Objects defined in ancestors will takes higher precedence?
A. Descendant objects, will take precedence over ancestor objects.
B. Ancestor will have precedence over descendant objects.
C. Ancestor objects will have precedence over other ancestor objects.
D. Descendant object will take precedence over other descendant objects.
-
Question 49:
If an administrator wants to decrypt SMTP traffic and possesses the saver's certificate, which SSL decryption mode will allow the Palo Alto Networks NGFW to inspect traffic to the server?
A. TLS Bidirectional Inspection
B. SSL Inbound Inspection
C. SSH Forward now proxy
D. SMTP inbound Decryption
-
Question 50:
If the firewall is configured for credential phishing prevention using the "Domain Credential Filter" method, which login will be detected as credential theft?
A. Using the name user's corporate username and password.
B. First four letters of the username matching any valid corporate username.
C. Matching any valid corporate username.
D. Mapping to the IP address of the logged-in user.
Related Exams:
PAN-NGFE
Palo Alto Networks Network Next-Generation Firewall EngineerPAN-NSG
Palo Alto Networks Network Security GeneralistPAN-NSP
Palo Alto Networks Network Security ProfessionalPAN-SSEE
Palo Alto Networks Security Service Edge EngineerPAN-XDRE
Palo Alto Networks XDR EngineerPCCET
Palo Alto Networks Certified Cybersecurity Entry-level Technician (PCCET)PCCSA
Palo Alto Networks Certified Cybersecurity Associate (PCCSA)PCCSE
Prisma Certified Cloud Security Engineer (PCCSE)PCDRA
Palo Alto Networks Certified Detection and Remediation Analyst (PCDRA)PCNSA
Palo Alto Networks Certified Network Security Administrator (PCNSA)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Palo Alto Networks exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your PCNSC exam preparations and Palo Alto Networks certification application, do not hesitate to visit our Vcedump.com to find your solutions here.