Exam Details
Exam Code
:PCNSAExam Name
:Palo Alto Networks Certified Network Security Administrator (PCNSA)Certification
:Palo Alto Networks CertificationsVendor
:Palo Alto NetworksTotal Questions
:443 Q&AsLast Updated
:Aug 15, 2025
Palo Alto Networks Palo Alto Networks Certifications PCNSA Questions & Answers
-
Question 421:
Which action results in the firewall blocking network traffic with out notifying the sender?
A. Drop
B. Deny
C. Reset Server
D. Reset Client
-
Question 422:
An administrator is configuring a NAT rule.
At a minimum, which three forms of information are required? (Choose three.)
A. name
B. source zone
C. destination interface
D. destination address
E. destination zone
-
Question 423:
An administrator configured a Security policy rule with an Antivirus Security profile. The administrator did not change the action for the profile. If a virus gets detected, how will the firewall handle the traffic?
A. It allows the traffic because the profile was not set to explicitly deny the traffic.
B. It drops the traffic because the profile was not set to explicitly allow the traffic.
C. It uses the default action assigned to the virus signature.
D. It allows the traffic but generates an entry in the Threat logs.
-
Question 424:
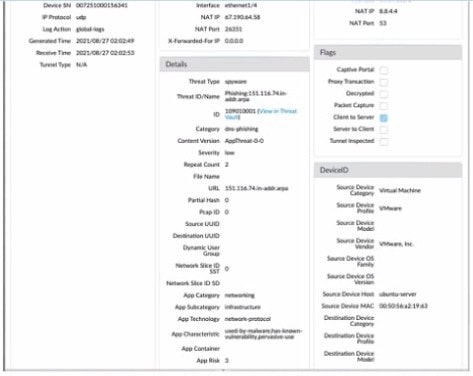
Given the detailed log information above, what was the result of the firewall traffic inspection?
A. It was blocked by the Vulnerability Protection profile action.
B. It was blocked by the Anti-Virus Security profile action.
C. It was blocked by the Anti-Spyware Profile action.
D. It was blocked by the Security policy action.
-
Question 425:
When is the content inspection performed in the packet flow process?
A. after the application has been identified
B. after the SSL Proxy re-encrypts the packet
C. before the packet forwarding process
D. before session lookup
-
Question 426:
Users from the internal zone need to be allowed to Telnet into a server in the DMZ zone.
Complete the security policy to ensure only Telnet is allowed.
Security Policy: Source Zone: Internal to DMZ Zone __________services "Application defaults", and action = Allow
A. Destination IP: 192.168.1.123/24
B. Application = `Telnet'
C. Log Forwarding
D. USER-ID = `Allow users in Trusted'
-
Question 427:
Which interface type requires no routing or switching but applies Security or NAT policy rules before passing allowed traffic?
A. Layer 3
B. Virtual Wire
C. Tap
D. Layer 2
-
Question 428:
Palo Alto Networks firewall architecture accelerates content map minimizing latency using which two components'? (Choose two )
A. Network Processing Engine
B. Single Stream-based Engine
C. Policy Engine
D. Parallel Processing Hardware
-
Question 429:
You receive notification about new malware that infects hosts through malicious files transferred by FTP.
Which Security profile detects and protects your internal networks from this threat after you update your firewall's threat signature database?
A. URL Filtering profile applied to inbound Security policy rules.
B. Data Filtering profile applied to outbound Security policy rules.
C. Antivirus profile applied to inbound Security policy rules.
D. Vulnerability Prote ction profile applied to outbound Security policy rules.
-
Question 430:
An internal host wants to connect to servers of the internet through using source NAT. Which policy is required to enable source NAT on the firewall?
A. NAT policy with source zone and destination zone specified
B. post-NAT policy with external source and any destination address
C. NAT policy with no source of destination zone selected
D. pre-NAT policy with external source and any destination address
Related Exams:
PAN-NGFE
Palo Alto Networks Network Next-Generation Firewall EngineerPAN-NSG
Palo Alto Networks Network Security GeneralistPAN-NSP
Palo Alto Networks Network Security ProfessionalPAN-SSEE
Palo Alto Networks Security Service Edge EngineerPAN-XDRE
Palo Alto Networks XDR EngineerPCCET
Palo Alto Networks Certified Cybersecurity Entry-level Technician (PCCET)PCCSA
Palo Alto Networks Certified Cybersecurity Associate (PCCSA)PCCSE
Prisma Certified Cloud Security Engineer (PCCSE)PCDRA
Palo Alto Networks Certified Detection and Remediation Analyst (PCDRA)PCNSA
Palo Alto Networks Certified Network Security Administrator (PCNSA)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Palo Alto Networks exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your PCNSA exam preparations and Palo Alto Networks certification application, do not hesitate to visit our Vcedump.com to find your solutions here.