Exam Details
Exam Code
:PCNSAExam Name
:Palo Alto Networks Certified Network Security Administrator (PCNSA)Certification
:Palo Alto Networks CertificationsVendor
:Palo Alto NetworksTotal Questions
:443 Q&AsLast Updated
:Aug 15, 2025
Palo Alto Networks Palo Alto Networks Certifications PCNSA Questions & Answers
-
Question 411:
What is the minimum timeframe that can be set on the firewall to check for new WildFire signatures?
A. every 30 minutes
B. every 5 minutes
C. once every 24 hours
D. every 1 minute
-
Question 412:
An administrator wants to create a NAT policy to allow multiple source IP addresses to be translated to the same public IP address. What is the most appropriate NAT policy to achieve this?
A. Dynamic IP and Port
B. Dynamic IP
C. Static IP
D. Destination
-
Question 413:
Which five Zero Trust concepts does a Palo Alto Networks firewall apply to achieve an integrated approach to prevent threats? (Choose five.)
A. User identification
B. Filtration protection
C. Vulnerability protection
D. Antivirus
E. Application identification
F. Anti-spyware
-
Question 414:
An administrator would like to silently drop traffic from the internet to a ftp server.
Which Security policy action should the administrator select?
A. Reset-server
B. Block
C. Deny
D. Drop
-
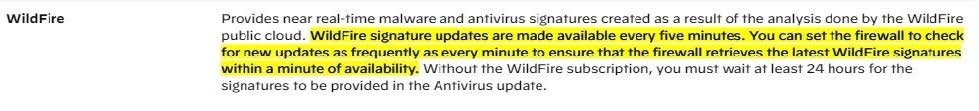
Question 415:
What in the minimum frequency for which you can configure the firewall too check for new wildfire antivirus signatures?
A. every 5 minutes
B. every 1 minute
C. every 24 hours
D. every 30 minutes
-
Question 416:
Which Palo Alto Networks firewall security platform provides network security for mobile endpoints by inspecting traffic deployed as internet gateways?
A. GlobalProtect
B. AutoFocus
C. Aperture
D. Panorama
-
Question 417:
How are Application Fillers or Application Groups used in firewall policy?
A. An Application Filter is a static way of grouping applications and can be configured as a nested member of an Application Group
B. An Application Filter is a dynamic way to group applications and can be configured as a nested member of an Application Group
C. An Application Group is a dynamic way of grouping applications and can be configured as a nested member of an Application Group
D. An Application Group is a static way of grouping applications and cannot be configured as a nested member of Application Group
-
Question 418:
Based on the screenshot what is the purpose of the group in User labelled ''it"?
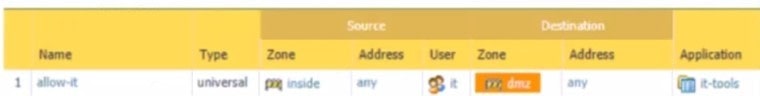
A. Allows users to access IT applications on all ports
B. Allows users in group "DMZ" lo access IT applications
C. Allows "any" users to access servers in the DMZ zone
D. Allows users in group "it" to access IT applications
-
Question 419:
Given the Cyber-Attack Lifecycle diagram, identify the stage in which the attacker can initiate malicious code against a targeted machine.
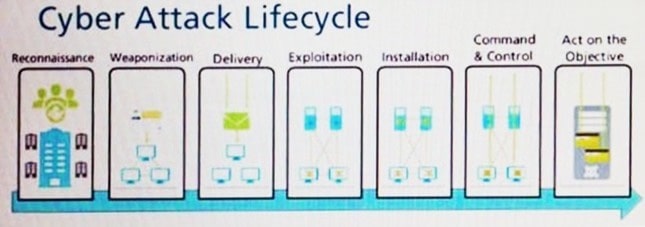
A. Exploitation
B. Installation
C. Reconnaissance
D. Act on Objective
-
Question 420:
Which two statements are true for the DNS security service introduced in PAN-OS version 10.0?
A. It functions like PAN-DB and requires activation through the app portal.
B. It removes the 100K limit for DNS entries for the downloaded DNS updates.
C. It eliminates the need for dynamic DNS updates.
D. It is automatically enabled and configured.
Related Exams:
PAN-NGFE
Palo Alto Networks Network Next-Generation Firewall EngineerPAN-NSG
Palo Alto Networks Network Security GeneralistPAN-NSP
Palo Alto Networks Network Security ProfessionalPAN-SSEE
Palo Alto Networks Security Service Edge EngineerPAN-XDRE
Palo Alto Networks XDR EngineerPCCET
Palo Alto Networks Certified Cybersecurity Entry-level Technician (PCCET)PCCSA
Palo Alto Networks Certified Cybersecurity Associate (PCCSA)PCCSE
Prisma Certified Cloud Security Engineer (PCCSE)PCDRA
Palo Alto Networks Certified Detection and Remediation Analyst (PCDRA)PCNSA
Palo Alto Networks Certified Network Security Administrator (PCNSA)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Palo Alto Networks exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your PCNSA exam preparations and Palo Alto Networks certification application, do not hesitate to visit our Vcedump.com to find your solutions here.