PCNSA Exam Details
-
Exam Code
:PCNSA -
Exam Name
:Palo Alto Networks Certified Network Security Administrator (PCNSA) -
Certification
:Palo Alto Networks Certifications -
Vendor
:Palo Alto Networks -
Total Questions
:443 Q&As -
Last Updated
:Jan 17, 2026
Palo Alto Networks PCNSA Online Questions & Answers
-
Question 1:
Which type of administrator account cannot be used to authenticate user traffic flowing through the firewall's data plane?
A. Kerberos user
B. SAML user
C. local database user
D. local user -
Question 2:
When creating a Source NAT policy, which entry in the Translated Packet tab will display the options Dynamic IP and Port, Dynamic, Static IP, and None?
A. Translation Type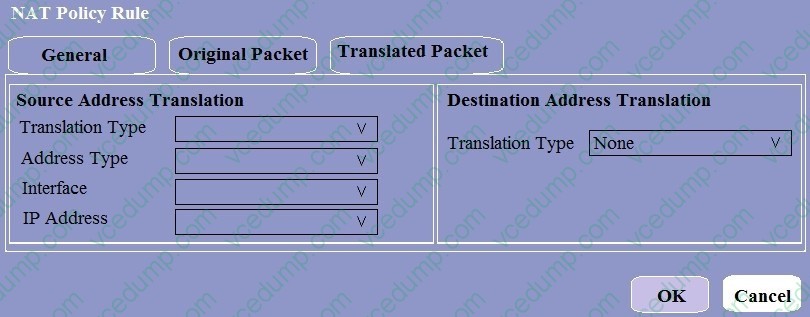
B. Interface
C. Address Type
D. IP Address -
Question 3:
Which two firewall components enable you to configure SYN flood protection thresholds? (Choose two.)
A. QoS profile
B. DoS Protection profile
C. Zone Protection profile
D. DoS Protection policy -
Question 4:
In a security policy what is the quickest way to rest all policy rule hit counters to zero?
A. Use the CLI enter the command reset rules all
B. Highlight each rule and use the Reset Rule Hit Counter > Selected Rules.
C. use the Reset Rule Hit Counter > All Rules option.
D. Reboot the firewall. -
Question 5:
Which rule type is appropriate for matching traffic both within and between the source and destination zones?
A. interzone
B. shadowed
C. intrazone
D. universal -
Question 6:
What is the correct process tor creating a custom URL category?
A. Objects > Security Profiles > URL Category > Add
B. Objects > Custom Objects > URL Filtering > Add
C. Objects > Security Profiles > URL Filtering > Add
D. Objects > Custom Objects > URL Category > Add -
Question 7:
Four configuration choices are listed, and each could be used to block access to a specific URL. If you configured each choices to block the sameURL then which choice would be the last to block access to the URL?
A. EDL in URL Filtering Profile.
B. Custom URL category in Security Policy rule.
C. Custom URL category in URL Filtering Profile.
D. PAN-DB URL category in URL Filtering Profile. -
Question 8:
Based on the security policy rules shown, ssh will be allowed on which port?
A. any port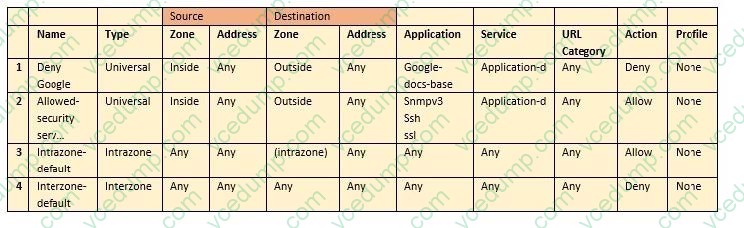
B. same port as ssl and snmpv3
C. the default port
D. only ephemeral ports -
Question 9:
What is the maximum volume of concurrent administrative account sessions?
A. Unlimited
B. 2
C. 10
D. 1 -
Question 10:
Your company requires positive username attribution of every IP address used by wireless devices to support a new compliance requirement. You must collect IP-to-user mappings as soon as possible with minimal downtime and minimal configuration changes to the wireless devices themselves. The wireless devices are from various manufactures.
Given the scenario, choose the option for sending IP-to-user mappings to the NGFW.
A. syslog
B. RADIUS
C. UID redistribution
D. XFF headers
Related Exams:
-
PAN-NGFE
Palo Alto Networks Network Next-Generation Firewall Engineer -
PAN-NSA
Palo Alto Networks Network Security Analyst -
PAN-NSG
Palo Alto Networks Network Security Generalist -
PAN-NSP
Palo Alto Networks Network Security Professional -
PAN-SSEE
Palo Alto Networks Security Service Edge Engineer -
PAN-XDRA
Palo Alto Networks XDR Analyst -
PAN-XDRE
Palo Alto Networks XDR Engineer -
PAN-XSIAMA
Palo Alto Networks XSIAM Analyst -
PAN-XSIAME
Palo Alto Networks XSIAM Engineer -
PAN-XSOARE
Palo Alto Networks XSOAR Engineer
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Palo Alto Networks exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your PCNSA exam preparations and Palo Alto Networks certification application, do not hesitate to visit our Vcedump.com to find your solutions here.