Exam Details
Exam Code
:PCNSAExam Name
:Palo Alto Networks Certified Network Security Administrator (PCNSA)Certification
:Palo Alto Networks CertificationsVendor
:Palo Alto NetworksTotal Questions
:443 Q&AsLast Updated
:Aug 15, 2025
Palo Alto Networks Palo Alto Networks Certifications PCNSA Questions & Answers
-
Question 141:
Which Palo Alto networks security operating platform service protects cloud-based application such as Dropbox and salesforce by monitoring permissions and shared and scanning files for Sensitive information?
A. Prisma SaaS
B. AutoFocus
C. Panorama
D. GlobalProtect
-
Question 142:
You receive notification about a new malware that infects hosts An infection results in the infected host attempting to contact a command-and-control server Which Security Profile when applied to outbound Security policy rules detects and prevents this threat from establishing a command-and-control connection?
A. Antivirus Profile
B. Data Filtering Profile
C. Vulnerability Protection Profile
D. Anti-Spyware Profile
-
Question 143:
Which statements is true regarding a Heatmap report?
A. When guided by authorized sales engineer, it helps determine te areas of greatest security risk.
B. It provides a percentage of adoption for each assessment area.
C. It runs only on firewall.
D. It provides a set of questionnaires that help uncover security risk prevention gaps across all areas of network and security architecture.
-
Question 144:
Which two security profile types can be attached to a security policy? (Choose two.)
A. antivirus
B. DDoS protection
C. threat
D. vulnerability
-
Question 145:
Which User-ID mapping method should be used for an environment with clients that do not authenticate to Windows Active Directory?
A. Windows session monitoring via a domain controller
B. passive server monitoring using the Windows-based agent
C. Captive Portal
D. passive server monitoring using a PAN-OS integrated User-ID agent
-
Question 146:
Refer to the exhibit. An administrator is using DNAT to map two servers to a single public IP address. Traffic will be steered to the specific server based on the application, where Host A (10.1.1.100) receives HTTP traffic and Host B
(10.1.1.101) receives SSH traffic.
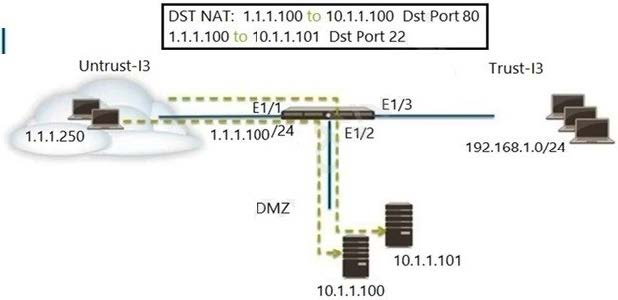
Which two Security policy rules will accomplish this configuration? (Choose two.)
A. Untrust (Any) to DMZ (1.1.1.100), ssh - Allow
B. Untrust (Any) to Untrust (10.1.1.1), web-browsing -Allow
C. Untrust (Any) to Untrust (10.1.1.1), ssh -Allow
D. Untrust (Any)to DMZ (10.1.1.100. 10.1.1.101), ssh, web-browsing-Allow
E. Untrust (Any) to DMZ (1.1.1.100), web-browsing - Allow
-
Question 147:
What must be configured for the firewall to access multiple authentication profiles for external services to authenticate a non-local account?
A. authentication sequence
B. LDAP server profile
C. authentication server list
D. authentication list profile
-
Question 148:
To what must an interface be assigned before it can process traffic?
A. Security Zone
B. Security policy
C. Security Protection
D. Security profile
-
Question 149:
According to the best practices for mission critical devices, what is the recommended interval for antivirus updates?
A. by minute
B. hourly
C. daily
D. weekly
-
Question 150:
What are three characteristics of the Palo Alto Networks DNS Security service? (Choose three.)
A. It uses techniques such as DGA.DNS tunneling detection and machine learning.
B. It requires a valid Threat Prevention license.
C. It enables users to access real-time protections using advanced predictive analytics.
D. It requires a valid URL Filtering license.
E. It requires an active subscription to a third-party DNS Security service.
Related Exams:
PAN-NGFE
Palo Alto Networks Network Next-Generation Firewall EngineerPAN-NSG
Palo Alto Networks Network Security GeneralistPAN-NSP
Palo Alto Networks Network Security ProfessionalPAN-SSEE
Palo Alto Networks Security Service Edge EngineerPAN-XDRE
Palo Alto Networks XDR EngineerPCCET
Palo Alto Networks Certified Cybersecurity Entry-level Technician (PCCET)PCCSA
Palo Alto Networks Certified Cybersecurity Associate (PCCSA)PCCSE
Prisma Certified Cloud Security Engineer (PCCSE)PCDRA
Palo Alto Networks Certified Detection and Remediation Analyst (PCDRA)PCNSA
Palo Alto Networks Certified Network Security Administrator (PCNSA)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Palo Alto Networks exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your PCNSA exam preparations and Palo Alto Networks certification application, do not hesitate to visit our Vcedump.com to find your solutions here.