Exam Details
Exam Code
:PCNSAExam Name
:Palo Alto Networks Certified Network Security Administrator (PCNSA)Certification
:Palo Alto Networks CertificationsVendor
:Palo Alto NetworksTotal Questions
:443 Q&AsLast Updated
:Aug 15, 2025
Palo Alto Networks Palo Alto Networks Certifications PCNSA Questions & Answers
-
Question 131:
In a File Blocking profile, which two actions should be taken to allow file types that support critical apps? (Choose two.)
A. Clone and edit the Strict profile.
B. Use URL filtering to limit categories in which users can transfer files.
C. Set the action to Continue.
D. Edit the Strict profile.
-
Question 132:
Access to which feature requires the PAN-OS Filtering license?
A. PAN-DB database
B. DNS Security
C. Custom URL categories
D. URL external dynamic lists
-
Question 133:
Which dataplane layer of the graphic shown provides pattern protection for spyware and vulnerability exploits on a Palo Alto Networks Firewall?
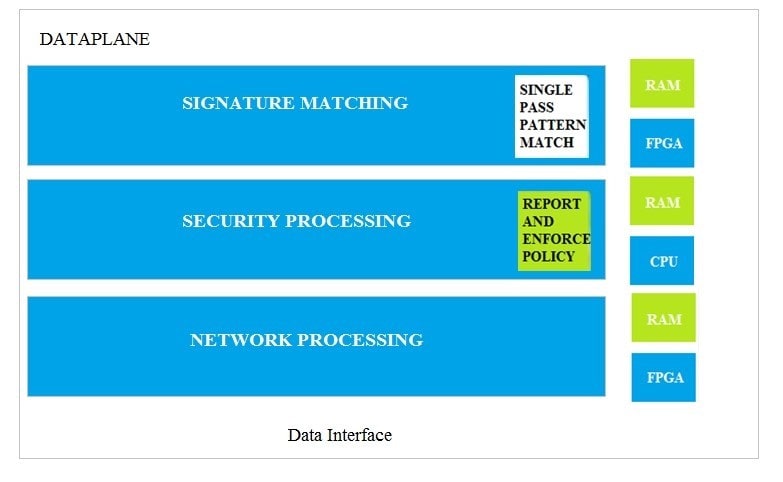
A. Signature Matching
B. Network Processing
C. Security Processing
D. Security Matching
-
Question 134:
What is the main function of Policy Optimizer?
A. reduce load on the management plane by highlighting combinable security rules
B. migrate other firewall vendors' security rules to Palo Alto Networks configuration
C. eliminate "Log at Session Start" security rules
D. convert port-based security rules to application-based security rules
-
Question 135:
Which license must an Administrator acquire prior to downloading Antivirus Updates for use with the firewall?
A. Threat Prevention License
B. Threat Implementation License
C. Threat Environment License
D. Threat Protection License
-
Question 136:
URL categories can be used as match criteria on which two policy types? (Choose two.)
A. authentication
B. decryption
C. application override
D. NAT
-
Question 137:
Which definition describes the guiding principle of the zero-trust architecture?
A. never trust, never connect
B. always connect and verify
C. never trust, always verify
D. trust, but verity
-
Question 138:
All users from the internal zone must be allowed only Telnet access to a server in the DMZ zone. Complete the two empty fields in the Security Policy rules that permits only this type of access.

Choose two.
A. Service = "any"
B. Application = "Telnet"
C. Service - "application-default"
D. Application = "any"
-
Question 139:
An administrator is reviewing the Security policy rules shown in the screenshot below. Which statement is correct about the information displayed?
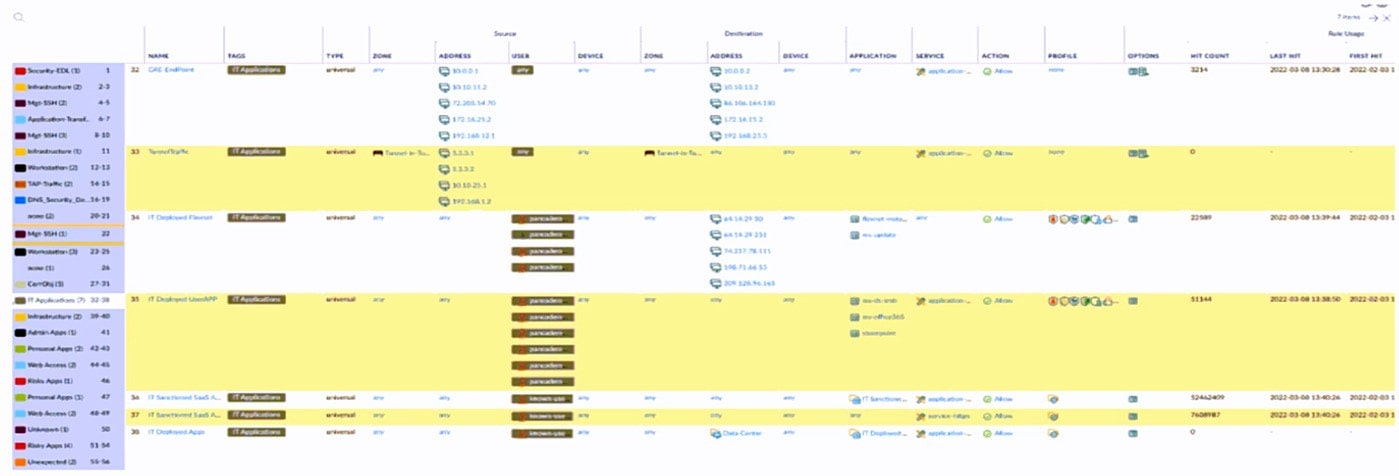
A. Eleven rules use the "Infrastructure* tag.
B. The view Rulebase as Groups is checked.
C. There are seven Security policy rules on this firewall.
D. Highlight Unused Rules is checked.
-
Question 140:
When HTTPS for management and GlobalProtect are enabled on the same interface, which TCP port is used for management access?
A. 80
B. 8443
C. 4443
D. 443
Related Exams:
PAN-NGFE
Palo Alto Networks Network Next-Generation Firewall EngineerPAN-NSG
Palo Alto Networks Network Security GeneralistPAN-NSP
Palo Alto Networks Network Security ProfessionalPAN-SSEE
Palo Alto Networks Security Service Edge EngineerPAN-XDRE
Palo Alto Networks XDR EngineerPCCET
Palo Alto Networks Certified Cybersecurity Entry-level Technician (PCCET)PCCSA
Palo Alto Networks Certified Cybersecurity Associate (PCCSA)PCCSE
Prisma Certified Cloud Security Engineer (PCCSE)PCDRA
Palo Alto Networks Certified Detection and Remediation Analyst (PCDRA)PCNSA
Palo Alto Networks Certified Network Security Administrator (PCNSA)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Palo Alto Networks exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your PCNSA exam preparations and Palo Alto Networks certification application, do not hesitate to visit our Vcedump.com to find your solutions here.