Exam Details
Exam Code
:PCNSAExam Name
:Palo Alto Networks Certified Network Security Administrator (PCNSA)Certification
:Palo Alto Networks CertificationsVendor
:Palo Alto NetworksTotal Questions
:443 Q&AsLast Updated
:Aug 15, 2025
Palo Alto Networks Palo Alto Networks Certifications PCNSA Questions & Answers
-
Question 151:
Which type of address object is www.paloaltonetworks.com?
A. IP range
B. IP netmask
C. named address
D. FQDN
-
Question 152:
Which path is used to save and load a configuration with a Palo Alto Networks firewall?
A. Device>Setup>Services
B. Device>Setup>Management
C. Device>Setup>Operations
D. Device>Setup>Interfaces
-
Question 153:
An administrator needs to allow users to use their own office applications.
How should the administrator configure the firewall to allow multiple applications in a dynamic environment?
A. Create an Application Filter and name it Office Programs, the filter it on the business- systems category, office-programs subcategory
B. Create an Application Group and add business-systems to it
C. Create an Application Filter and name it Office Programs, then filter it on the business- systems category
D. Create an Application Group and add Office 365, Evernote, Google Docs, and Libre Office
-
Question 154:
What does an application filter help you to do?
A. It dynamically provides application statistics based on network, threat, and blocked activity,
B. It dynamically filters applications based on critical, high, medium, low. or informational severity.
C. It dynamically groups applications based on application attributes such as category and subcategory.
D. It dynamically shapes defined application traffic based on active sessions and bandwidth usage.
-
Question 155:
In the example security policy shown, which two websites fcked? (Choose two.)
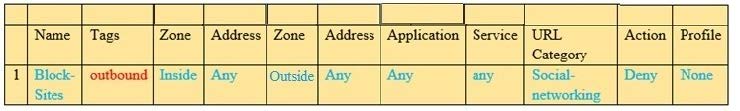
A. LinkedIn
B. Facebook
C. YouTube
D. Amazon
-
Question 156:
Which three interface deployment methods can be used to block traffic flowing through the Palo Alto Networks firewall? (Choose three.)
A. Layer 2
B. Virtual Wire
C. Tap
D. Layer 3
E. HA
-
Question 157:
The CFO found a malware infected USB drive in the parking lot, which when inserted infected their corporate laptop the malware contacted a known command-and-control server which exfiltrating corporate data. Which Security profile feature could have been used to prevent the communications with the command-and-control server?
A. Create a Data Filtering Profile and enable its DNS sinkhole feature.
B. Create an Antivirus Profile and enable its DNS sinkhole feature.
C. Create an Anti-Spyware Profile and enable its DNS sinkhole feature.
D. Create a URL Filtering Profile and block the DNS sinkhole URL category.
-
Question 158:
Which security policy rule would be needed to match traffic that passes between the Outside zone and Inside zone, but does not match traffic that passes within the zones?
A. intrazone
B. interzone
C. universal
D. global
-
Question 159:
Why does a company need an Antivirus profile?
A. To prevent command-and-control traffic
B. To protect against viruses, worms, and trojans
C. To prevent known exploits
D. To prevent access to malicious web content
-
Question 160:
Which Security profile would you apply to identify infected hosts on the protected network uwall user database?
A. Anti-spyware
B. Vulnerability protection
C. URL filtering
D. Antivirus
Related Exams:
PAN-NGFE
Palo Alto Networks Network Next-Generation Firewall EngineerPAN-NSG
Palo Alto Networks Network Security GeneralistPAN-NSP
Palo Alto Networks Network Security ProfessionalPAN-SSEE
Palo Alto Networks Security Service Edge EngineerPAN-XDRE
Palo Alto Networks XDR EngineerPCCET
Palo Alto Networks Certified Cybersecurity Entry-level Technician (PCCET)PCCSA
Palo Alto Networks Certified Cybersecurity Associate (PCCSA)PCCSE
Prisma Certified Cloud Security Engineer (PCCSE)PCDRA
Palo Alto Networks Certified Detection and Remediation Analyst (PCDRA)PCNSA
Palo Alto Networks Certified Network Security Administrator (PCNSA)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Palo Alto Networks exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your PCNSA exam preparations and Palo Alto Networks certification application, do not hesitate to visit our Vcedump.com to find your solutions here.