Exam Details
Exam Code
:NSE4_FGT-7.2Exam Name
:Fortinet NSE 4 - FortiOS 7.2Certification
:Fortinet CertificationsVendor
:FortinetTotal Questions
:185 Q&AsLast Updated
:Aug 11, 2025
Fortinet Fortinet Certifications NSE4_FGT-7.2 Questions & Answers
-
Question 51:
Which statement is correct regarding the use of application control for inspecting web applications?
A. Application control can identity child and parent applications, and perform different actions on them.
B. Application control signatures are organized in a nonhierarchical structure.
C. Application control does not require SSL inspection to identity web applications.
D. Application control does not display a replacement message for a blocked web application.
-
Question 52:
Which three options are the remote log storage options you can configure on FortiGate? (Choose three.)
A. FortiCache
B. FortiSIEM
C. FortiAnalyzer
D. FortiSandbox
E. FortiCloud
-
Question 53:
Refer to the exhibit.
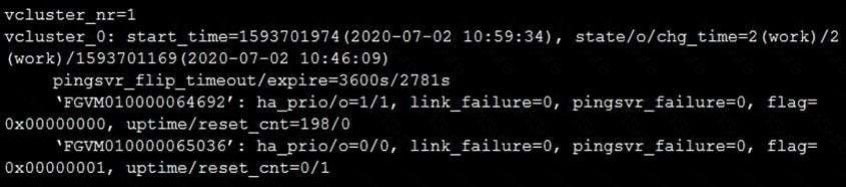
The exhibit displays the output of the CLI command: diagnose sys ha dump-by vcluster.
The override setting is enable for the FortiGate with SN FGVM010000064692.
Which two statements are true? (Choose two.)
A. FortiGate SN FGVM010000065036 HA uptime has been reset.
B. FortiGate devices are not in sync because one device is down.
C. FortiGate SN FGVM010000064692 is the primary because of higher HA uptime.
D. FortiGate SN FGVM010000064692 has the higher HA priority.
-
Question 54:
Why does FortiGate Keep TCP sessions in the session table for several seconds, even after both sides (client and server) have terminated the session?
A. To allow for out-of-order packets that could arrive after the FIN/ACK packets
B. To finish any inspection operations
C. To remove the NAT operation
D. To generate logs
-
Question 55:
A network administrator has enabled SSL certificate inspection and antivirus on FortiGate. When downloading an EICAR test file through HTTP, FortiGate detects the virus and blocks the file. When downloading the same file through HTTPS, FortiGate does not detect the virus and the file can be downloaded.
What is the reason for the failed virus detection by FortiGate?
A. The website is exempted from SSL inspection.
B. The EICAR test file exceeds the protocol options oversize limit.
C. The selected SSL inspection profile has certificate inspection enabled.
D. The browser does not trust the FortiGate self-signed CA certificate.
-
Question 56:
Refer to the exhibit.
The exhibit shows a diagram of a FortiGate device connected to the network, the firewall policy and VIP configuration on the FortiGate device, and the routing table on the ISP router.
When the administrator tries to access the web server public address (203.0.113.2) from the internet, the connection times out. At the same time, the administrator runs a sniffer on FortiGate to capture incoming web traffic to the server and does not see any output.
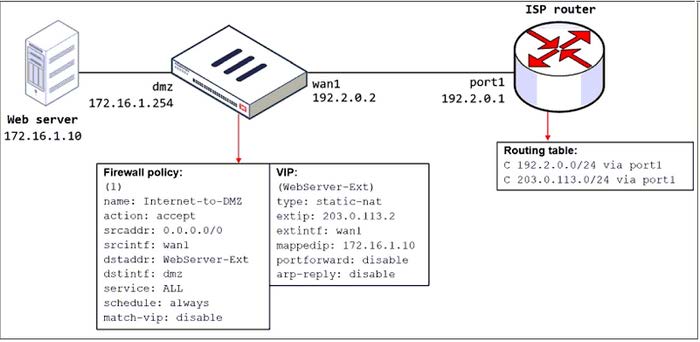
Based on the information shown in the exhibit, what configuration change must the administrator make to fix the connectivity issue?
A. Configure a loopback interface with address 203.0.113.2/32.
B. In the VIP configuration, enable arp-reply.
C. Enable port forwarding on the server to map the external service port to the internal service port.
D. In the firewall policy configuration, enable match-vip.
-
Question 57:
Refer to the exhibit.
The exhibit shows the FortiGuard Category Based Filter section of a corporate web filter profile.
An administrator must block access to download.com, which belongs to the Freeware and Software Downloads category. The administrator must also allow other websites in the same category.
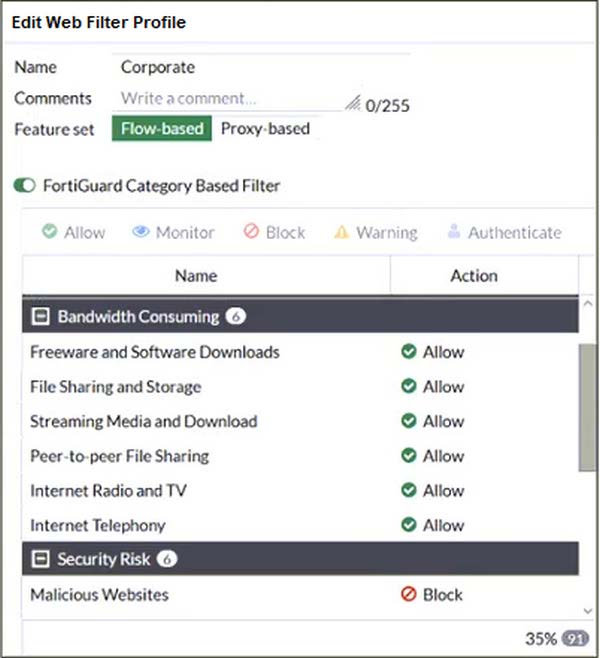
What are two solutions for satisfying the requirement? (Choose two.)
A. Configure a separate firewall policy with action Deny and an FQDN address object for *.download.com as destination address.
B. Configure a web override rating for download.com and select Malicious Websites as the subcategory.
C. Set the Freeware and Software Downloads category Action to Warning.
D. Configure a static URL filter entry for download.com with Type and Action set to Wildcard and Block, respectively.
-
Question 58:
What are two functions of ZTNA? (Choose two.)
A. ZTNA manages access through the client only.
B. ZTNA manages access for remote users only.
C. ZTNA provides a security posture check.
D. ZTNA provides role-based access.
-
Question 59:
Which two statements describe how the RPF check is used? (Choose two.)
A. The RPF check is a mechanism that protects FortiGate and the network from IP spoofing attacks.
B. The RPF check is run on the first sent and reply packet of any new session.
C. The RPF check is run on the first sent packet of any new session.
D. The RPF check is run on the first reply packet of any new session.
-
Question 60:
FortiGate is configured as a policy-based next-generation firewall (NGFW) and is applying web filtering and application control directly on the security policy.
Which two other security profiles can you apply to the security policy? (Choose two.)
A. Antivirus scanning
B. File filter
C. DNS filter
D. Intrusion prevention
Related Exams:
FCP_FAZ_AD-7.4
FCP - FortiAnalyzer 7.4 AdministratorFCP_FGT_AD-7.4
FCP - FortiGate 7.4 AdministratorFCP_FGT_AD-7.6
FortiGate 7.6 Administrator FCP_FGT_AD-7.6FCP_WCS_AD-7.4
FCP - AWS Cloud Security 7.4 AdministratorFCSS_EFW_AD-7.4
FCSS - Enterprise Firewall 7.4 AdministratorFCSS_NST_SE-7.4
FCSS - Network Security 7.4 Support EngineerFCSS_SASE_AD-24
FCSS - FortiSASE 24 AdministratorNSE4_FGT-5.6
Fortinet NSE 4 - FortiOS 5.6NSE4_FGT-6.0
Fortinet NSE 4 - FortiOS 6.0NSE4_FGT-6.4
Fortinet NSE 4 - FortiOS 6.4
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Fortinet exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your NSE4_FGT-7.2 exam preparations and Fortinet certification application, do not hesitate to visit our Vcedump.com to find your solutions here.