Exam Details
Exam Code
:HPE6-A29Exam Name
:Aruba Certified Mobility Professional 6.4Certification
:HP CertificationsVendor
:HPTotal Questions
:60 Q&AsLast Updated
:
HP HP Certifications HPE6-A29 Questions & Answers
-
Question 141:
Fast Failover has been implemented between Local 1 and Local 2 separated by Routers. During testing
Local1 was disabled and all Campus APs backed up to Local 2 flawlessly.
But the RAPs did not, they all failed.
What could be the cause?
A. RAPs should be configured in their own AP-groups
B. A VPN IP Pool must be configured on Local 2
C. The RAP whitelist must be ported over to Local 2
D. IPSec must be enabled on Local 2
E. RAPs are not supported by Fast Failover
-
Question 142:
A university has 2 departments. Department 1 has its own mobility domain with one controller. Department 2 has multiple controllers configured in a second domain. The university is planning on offering a new application and needs users to be able to roam between both mobility domains.
What is the best way to accomplish this?
A. The 2 existing domains should be left as they are. A 3rd mobility domain should then be created and all 3 controllers need to be added to it
B. Merge the controllers into the same mobility domain
C. The IP subnets of all controllers need to be configured to match
D. This cannot be accomplished
E. Create a new domain between a department 1 controller and one of the department 2 controllers
-
Question 143:
When configuring Captive Portal, which protocols are supported when accessing the Captive Portal? (Choose two.)
A. HTTPS
B. VPN
C. HTTP
D. TELNET
E. SSH
-
Question 144:
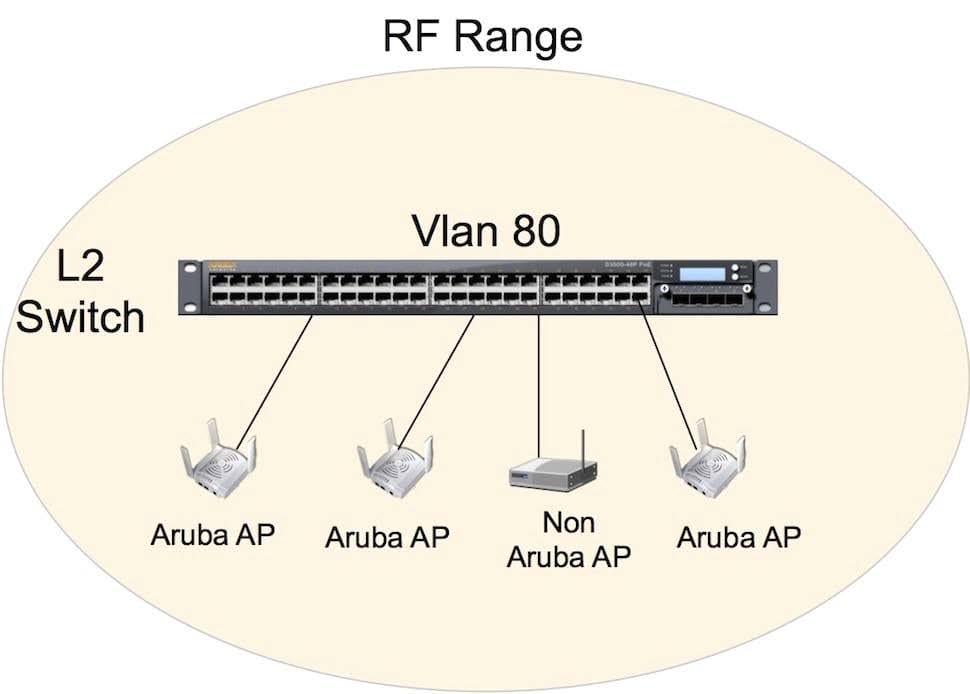
Referring to the diagram provided for this question, an employee brought an unauthorized AP from home and attached the LAN port to the cubicle Ethernet port. All Aruba APs and AMs as well as the employee AP are in VLAN 80 and within RF range of each other. No traffic from the wired or wireless network has passed through the unauthorized AP yet, but the AP began wireless broadcasts.
How will the Aruba system initially classify the employee's non-Aruba AP?
A. a valid AP
B. an AM
C. a Rogue AP
D. an interfering AP
E. a known interfering AP
-
Question 145:
Which profiles are required in an AP Group to enable an SSID with VLAN 1, WPA2 and LMSIP? (Choose three)
A. Virtual-ap ap mesh-radio-profile ap system profile
B. Wlan ssid-profile ap-system-profile virtual-ap profile
C. 802.1X authentication profile wlan ssid-profile virtual-ap profile
D. Virtual-ap profile ap-system profile aaa profile
-
Question 146:
A customer has configured a 3000 controller with the following commands: Vlan 55 Vlan 56 Vlan 57 Interface gigabitethernet 1/0 switchport mode trunk switchport trunk native vlan 55 switchport trunk allowed vlan 55-57 Which of the following sentences best describes this port?
A. All traffic in vlan 55 will be dropped and all traffic in vlan 56 and 57 will be trunked with and 802.1Q tag
B. All traffic in vlan 55, 56 and 57 will be trunked with an 802.1Q tag
C. All traffic in vlan 55 will be sent with an 802.1Q tag while vlan 56 and 57 traffic will be trunked untagged
D. All traffic in vlan 56 and 57 will be sent with an 802.1Q tag while vlan 55 traffic will be trunked untagged
-
Question 147:
Which of the following are valid RAP operating modes?
A. Always, Backup, Standard, Persistent
B. Always, Backup, Tunnel, Persistent
C. Always, Hotel-Connect, Tunnel, Standard
D. Backup, Hotel-Connect, Standard, Persistent
E. Backup, Normal, Tunnel, Always
-
Question 148:
Review the following truncated output from an Aruba controller for this item.
(example) #show rights logon
access-list List
Position Name Location
1 logon-control
2 captiveportal logon-control
Priority Source Destination Service Action
1 user any udp 68 deny 2 any any svc-icmp permit 3 any any svc-dns permit 4 any any svc-dhcp permit 5 any any svc-natt permit captiveportal
Priority Source Destination Service Action
1 user controller svc-https dst-nat 8081 2 user any svc-http dst-nat 8080 3 user any svc-https dst-nat 8081 4 user any svc-http-proxy1 dst-nat 8088 5 user any svc-http-proxy2 dst-nat 8088 6 user any svc-http-proxy3 dst-nat 8088 Based on the above output from an Aruba controller, an unauthenticated user assigned to the logon role
attempts to start an http session to IP address 172.16.43.170. What will happen?
A. the user's traffic will be passed to the IP address because of the policy statement:user any svc-http dstnat 8080
B. the user's traffic will be passed to the IP address because of the policy statement:user any svc-https dst-nat 8081
C. the user's traffic will be passed to the IP address because of the policy statement:user any svc-httpproxy1 dst-nat 8088
D. the user will not reach the IP address because of the policy statement:user any svc-http dst-nat 8080
E. the user will not reach the IP address because of the implicit deny any any at the end of the policy.
-
Question 149:
Which of the following will accept named VLANs as a parameter? (Choose three)
A. a VLAN pool
B. User Role for single VLAN
C. RADIUS Server attributes for role derivation
D. Firewall session rule
E. Port trunk configuration
-
Question 150:
What information do you need to generate a feature license key for an Aruba controller?
A. The controller's MAC address and the feature description.
B. controller's MAC address and the certificate number
C. controller's Serial Number and the feature description
D. controller's Serial Number and the certificate number
E. controller's MAC address and Serial Number
Related Exams:
HP0-003
HP OpenView Service Desk 5.xHP0-045
Supporting the ESL E-Series LobrariesHP0-052
Planning and Design of HP 9000/HP Integrity Server SolutionsHP0-053
Enterprise Integration and Management of HP ProLiant ServersHP0-054
Compaq/Oracle 8i I and P with Windows NTHP0-055
Implementing HP ProLiant ServersHP0-058
Configuration and Management of HP Integrity Mid-Range ServersHP0-063
LF PROFESSIONAL COLOR WORKFLOW MANAGEMENTHP0-064
HP BladeSystems C-Class Solutions 1HP0-065
Planning and Designing ProLiant Solutions for the Enterprise
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only HP exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your HPE6-A29 exam preparations and HP certification application, do not hesitate to visit our Vcedump.com to find your solutions here.