FCSS_SASE_AD-25 Exam Details
-
Exam Code
:FCSS_SASE_AD-25 -
Exam Name
:FCSS - FortiSASE 25 Administrator -
Certification
:Fortinet Certifications -
Vendor
:Fortinet -
Total Questions
:51 Q&As -
Last Updated
:Jan 19, 2026
Fortinet FCSS_SASE_AD-25 Online Questions & Answers
-
Question 1:
What can be configured on FortiSASE as an additional layer of security for FortiClient registration?
A. security posture tags
B. application inventory
C. user verification
D. device identification -
Question 2:
How do security profile group objects behave when central management is enabled on FortiSASE?
A. Objects support two-way synchronization.
B. Objects created on FortiSASE can be retrieved on FortiManager.
C. Objects that are only flow-based are supported.
D. Objects are considered read-only on FortiSASE. -
Question 3:
Refer to the exhibits.
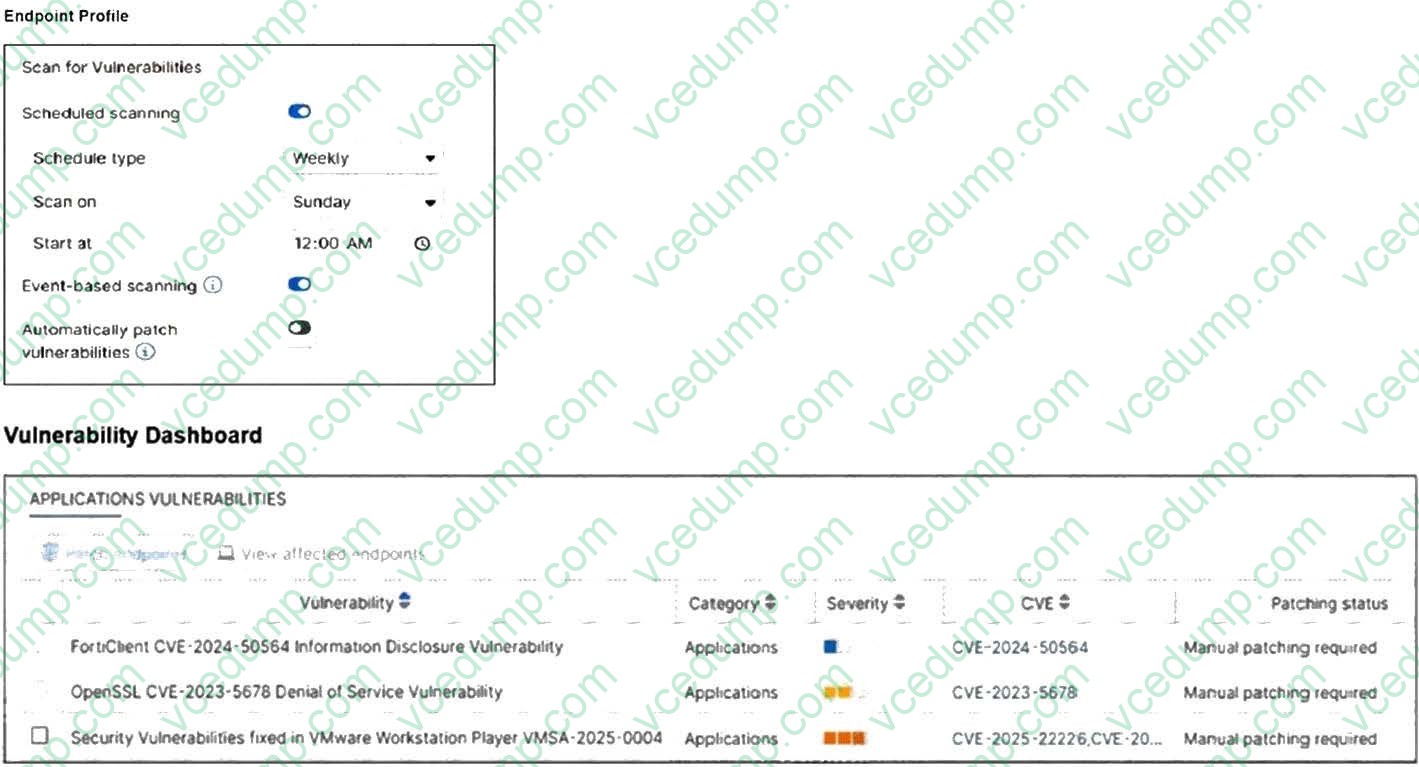
How will the application vulnerabilities be patched, based on the exhibits provided?
A. The vulnerability will be patched automatically based on the endpoint profile configuration.
B. The vulnerability will be patched by installing the patch from the vendor's website.
C. The end user will patch the vulnerabilities using the FortiClient software.
D. An administrator will patch the vulnerability remotely using FortiSASE. -
Question 4:
Refer to the exhibits.
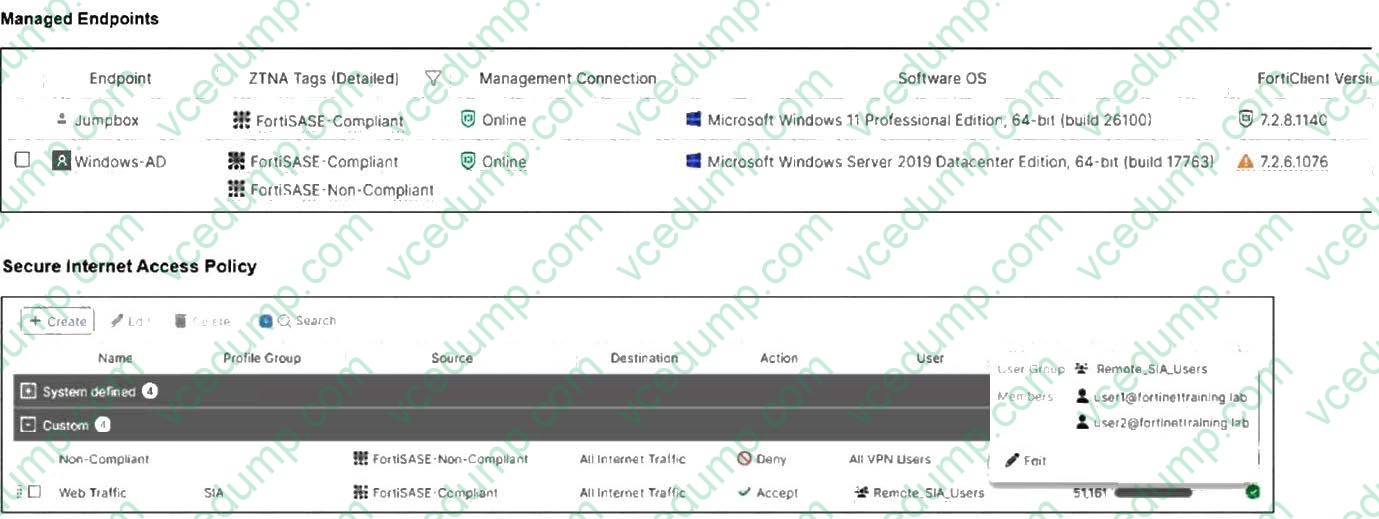
Jumpbox and Windows-AD are endpoints from the same remote location. Jumpbox can access the internet through FortiSASE, while Windows-AD can no longer access the internet. Based on the information in the exhibits, which reason explains the outage on Windows-AD?
A. Windows-AD is excluded from FortiSASE management.
B. The FortiClient version installed on Windows AD does not match the expected version on FortiSASE.
C. The device posture for Windows-AD has changed.
D. The remote VPN user on Windows-AD no longer matches any VPN policy. -
Question 5:
In a FortiSASE secure web gateway (SWG) deployment, which two features protect against web-based threats? (Choose two.)
A. SSL deep inspection for encrypted web traffic
B. malware protection with sandboxing capabilities
C. web application firewall (WAF) for web applications
D. intrusion prevention system (IPS) for web traffic -
Question 6:
A customer wants to ensure secure access for private applications for their users by replacing their VPN. Which two SASE technologies can you use to accomplish this task? (Choose two.)
A. zero trust network access (ZTNA)
B. secure SD-WAN
C. secure web gateway (SWG) and cloud access security broker (CASB)
D. SD-WAN on-ramp -
Question 7:
What is required to enable the MSSP feature on FortiSASE?
A. Role-based access control (RBAC) must be assigned to identity and access management (IAM) users using the FortiCloud IAM portal.
B. The MSSP add-on license must be applied to FortiSASE.
C. MSSP user accounts and permissions must be configured on the FortiSASE portal.
D. Multi-tenancy must be enabled on the FortiSASE portal. -
Question 8:
Refer to the exhibit.
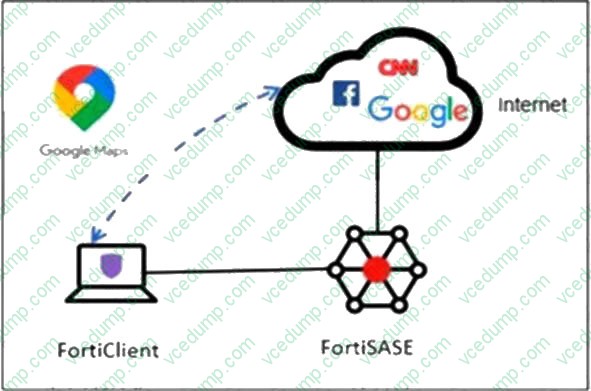
An organization must inspect all the endpoint internet traffic on FortiSASE, and exclude Google Maps traffic from the FortiSASE VPN tunnel and redirect it to the endpoint physical interface.
Which configuration must you apply to achieve this requirement?
A. Configure a steering bypass tunnel firewall policy using Google Maps FQDN to exclude and redirect the traffic.
B. Add the Google Maps URL in the zero trust network access (ZTNA) TCP access proxy forwarding rule.
C. Add the Google Maps URL as a steering bypass destination in the endpoint profile.
D. Exempt Google Maps in URL filtering in the web filter profile. -
Question 9:
How can digital experience monitoring (DEM) on an endpoint assist in diagnosing connectivity and network issues?
A. FortiSASE runs a ping from the endpoint to calculate the TTL to the SaaS application.
B. FortiSASE runs SNMP traps to the endpoint using the DEM agent to verify the SaaS application health status.
C. FortiSASE runs a netstat from the endpoint to the SaaS application to see if ports are open.
D. FortiSASE runs a trace job on the endpoint using the DEM agent to the Software-as-a-Service (SaaS) application. -
Question 10:
An organization must block user attempts to log in to non-company resources while using Microsoft Office 365 to prevent users from accessing unapproved cloud resources. Which FortiSASE feature can you implement to meet this requirement?
A. application control with inline-CASB
B. data loss prevention (DLP) with Microsoft Purview Information Protection (MPIP)
C. web filter with inline-CASB
D. DNS filter with domain filter
Related Exams:
-
EMEA-ADVANCED-SUPPORT
Fortinet EMEA Advanced Support -
FCP_FAC_AD-6.5
FCP - FortiAuthenticator 6.5 Administrator -
FCP_FAZ_AD-7.4
FCP - FortiAnalyzer 7.4 Administrator -
FCP_FAZ_AN-7.4
FCP - FortiAnalyzer 7.4 Analyst -
FCP_FCT_AD-7.2
FCP - Forti Client EMS 7.2 Administrator -
FCP_FGT_AD-7.4
FCP - FortiGate 7.4 Administrator -
FCP_FGT_AD-7.6
FortiGate 7.6 Administrator FCP_FGT_AD-7.6 -
FCP_FMG_AD-7.4
FCP - FortiManager 7.4 Administrator -
FCP_FMG_AD-7.6
FortiManager 7.6 Administrator -
FCP_FML_AD-7.4
FCP - FortiMail 7.4 Administrator
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Fortinet exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your FCSS_SASE_AD-25 exam preparations and Fortinet certification application, do not hesitate to visit our Vcedump.com to find your solutions here.