Exam Details
Exam Code
:E05-001Exam Name
:Information Storage and Management v3Certification
:EMC CertificationsVendor
:EMCTotal Questions
:186 Q&AsLast Updated
:Apr 25, 2025
EMC EMC Certifications E05-001 Questions & Answers
-
Question 41:
What is an accurate statement about hypervisor-based continuous data protection (CDP)?
A. Write splitter is embedded in the hypervisor
B. Journal is stored in a virtual machine
C. Journal and replica use the same storage volume
D. Virtual appliance runs on a storage system
-
Question 42:
A customer has a requirement to perform a backup each night. However, the customer has a limited amount of time for backups to run on week nights, Monday through Friday evenings.
Which backup granularity type is recommended to meet the backup window for those nights?
A. Incremental
B. Cumulative
C. Full
D. Differential
-
Question 43:
What is an accurate statement about Challenge Handshake Authentication Protocol (CHAP) control?
A. Enables initiators and targets to authenticate each other by using a shared secret code
B. Provides strong authentication for client-server applications by using secret-key cryptography
C. Allows a client to access protected resources from a resource server on behalf of a resource owner
D. Enables an organization to use authentication services from an identity provider
-
Question 44:
Why should a replica be consistent with its source?
A. Ensure the usability of the replica
B. Reduce the need to create multiple replicas
C. Ensure the security of the replica
D. Reduce the size of the replica
-
Question 45:
What is an accurate statement about full volume replication?
A. Target device is at least as large as the source device
B. Target device requires only a fraction of the space used by the source device
C. Target device is accessible only after the replication session starts
D. Target and source devices should be on different storage arrays
-
Question 46:
Which iSCSI host connectivity option is recommended in a CPU-intensive application environment?
A. iSCSI HBA
B. NIC with software-based iSCSI initiator
C. TCP offload engine
D. Converged Network Adapter
-
Question 47:
What is an example of an active attack on an IT infrastructure?
A. Attempt to modify information for malicious purposes
B. Attempt to copy the data from the storage system
C. Attempt to gain unauthorized access into the system
D. Attempt to gain access to the data in transit
-
Question 48:
The exhibit illustrates a software-defined storage environment. What do the labels "X" and "Y" represent in the exhibit?
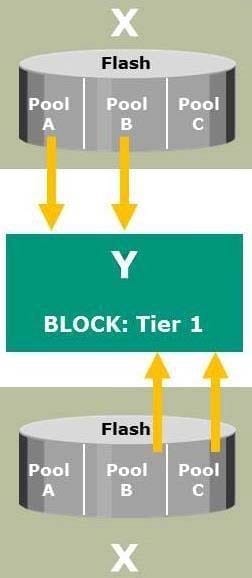
A. X is a virtual storage system and Y is a virtual storage pool
B. X is a virtual storage pool and Y is a virtual storage system
C. X is a physical storage pool and Y is a virtual storage system
D. X is a virtual storage pool and Y is a physical storage system
-
Question 49:
Which part of the Fibre Channel (FC) frame does the label "X" represent in the exhibit?

A. Frame Header
B. CRC
C. SOF
D. Data Field
-
Question 50:
In an FCoE SAN, what describes a Fibre Channel Forwarder function?
A. Transfer FCoe traffic over an FC SAN
B. Encapsulate IP packets into FC frames
C. Apply zoning configurations and provide fabric services
D. Provide both FC HBA and Nic functionality
Related Exams:
D-GAI-F-01
Dell GenAI Foundations AchievementD-MSS-DS-23
Dell Midrange Storage Solutions Design 2023D-OME-OE-A-24
Dell OpenManage Operate AchievementD-PDD-DY-23
Dell PowerProtect DD Deploy 2023D-PE-OE-23
Dell PowerEdge Operate 2023D-PEXE-IN-A-00
Dell PowerEdge XE9680 and XE8640 InstallD-PSC-MN-01
Dell GenAI Foundations AchievementD-PST-MN-A-24
Dell PowerStore Maintenance AchievementD-PWF-DS-23
Dell PowerFlex Design 2023D-RP-DY-A-24
Dell RecoverPoint Deploy Achievement
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EMC exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your E05-001 exam preparations and EMC certification application, do not hesitate to visit our Vcedump.com to find your solutions here.