Exam Details
Exam Code
:E05-001Exam Name
:Information Storage and Management v3Certification
:EMC CertificationsVendor
:EMCTotal Questions
:186 Q&AsLast Updated
:
EMC EMC Certifications E05-001 Questions & Answers
-
Question 51:
A customer wants 24x7 availability for a business application that uses a file system. Which operation ensures a consistent replica of the file system?
A. Unmount the file system prior to the creation of the replica
B. Stop the application prior to the creation of the replica
C. Flush the file system buffers after creation of the replica
D. Flush the file system buffers before creation of the replica
-
Question 52:
What is an accurate statement about the function of an archiving server?
A. Enables the ability to configure policies for archiving data
B. Installs agents on the archiving storage device
C. Scans the data that can be archived on application servers
D. Creates stub files on an archiving storage device
-
Question 53:
Which type of Fibre Channel (FC) ports do the labels "X" and "Y" represent in the exhibit?
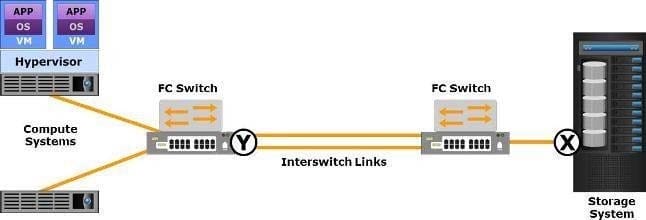
A. X is an F_Port and Y is an E_Port
B. X is an F_Port and Y is a G_Port
C. X is a G_Port and Y is an N_Port
D. X is an N_Port and Y is an E_Port
-
Question 54:
What is a benefit of a "recovery-in-place" backup approach in a virtualized data center?
A. Provides instant recovery of a failed virtual machine
B. Reduces the recovery point objective
C. Eliminates redundant data during virtual machine backups
D. Eliminates the backup window
-
Question 55:
What is a benefit of backing up data to a disk library?
A. Provides improved backup and recovery performance
B. Provides built-in portability to meet offsite requirements
C. Supports the shoe shining effect for improved backup performance
D. Pre-configured and dedicated appliance is only used for backups
-
Question 56:
What is a benefit of implementing a virtual machine (VM) storage migration?
A. Balances storage utilization by redistributing VMs across different storage systems
B. Enables VMs to keep functioning even if the source data is lost due to a failure
C. Improves the security of applications running inside VMs on the migrated storage system
D. Reduces the overall storage system capacity requirements for organizations
-
Question 57:
What accurately describes an attack vector in an IT infrastructure?
A. Series of steps that must be followed in order to complete an attack
B. Various entry points that can be used to launch an attack
C. Amount of effort required to exploit vulnerabilities in the infrastructure
D. Process of identifying the system components under attack
-
Question 58:
What contains the information about backup configuration and backup metadata?
A. Backup catalog
B. Proxy server
C. Tracking database
D. Backup image
-
Question 59:
What is an accurate statement about infrastructure discovery?
A. Creates an inventory of infrastructure components and provides information about the components
B. Standardizes on-going infrastructure management activities and assesses potential risks of the activities
C. Classifies, organizes, and analyzes all infrastructure management best practices stored in data lakes
D. Detects potential security attacks on a storage infrastructure and deploys specialized tools to eliminate the attacks
-
Question 60:
In which stage of the business continuity planning lifecycle does an organization identify critical business processes and assign recovery priorities?
A. Analyzing
B. Establishing objectives
C. Designing and developing
D. Implementing
Related Exams:
D-GAI-F-01
Dell GenAI Foundations AchievementD-MSS-DS-23
Dell Midrange Storage Solutions Design 2023D-OME-OE-A-24
Dell OpenManage Operate AchievementD-PDD-DY-23
Dell PowerProtect DD Deploy 2023D-PE-OE-23
Dell PowerEdge Operate 2023D-PEXE-IN-A-00
Dell PowerEdge XE9680 and XE8640 InstallD-PSC-MN-01
Dell GenAI Foundations AchievementD-PST-MN-A-24
Dell PowerStore Maintenance AchievementD-PWF-DS-23
Dell PowerFlex Design 2023D-RP-DY-A-24
Dell RecoverPoint Deploy Achievement
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EMC exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your E05-001 exam preparations and EMC certification application, do not hesitate to visit our Vcedump.com to find your solutions here.