Exam Details
Exam Code
:E05-001Exam Name
:Information Storage and Management v3Certification
:EMC CertificationsVendor
:EMCTotal Questions
:186 Q&AsLast Updated
:Apr 25, 2025
EMC EMC Certifications E05-001 Questions & Answers
-
Question 61:
What is an accurate statement about OAuth security control?
A. Allows a client to access protected resources from a resource server on behalf of a resource owner
B. Provides strong authentication for client-server applications by using secret-key cryptography
C. Enables initiators and targets to authenticate each other by using a shared secret code
D. Enables an organization to use authentication services from an identity provider
-
Question 62:
A company has an FC SAN environment. The company's network administrator wants to ensure that a particular switch port cannot function as an EPort and cannot be used to create an interswitch link. Which security mechanism should be used?
A. Persistent port disable
B. Virtual SAN
C. Port type locking
D. Port binding
-
Question 63:
Which type of Fibre Channel (FC) ports do the labels "X" and "Y" represent in the exhibit?
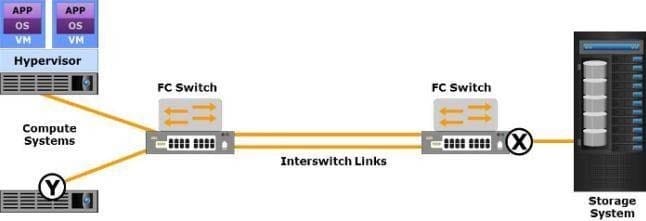
A. X is an E_Port and Y is an N_Port
B. X is an F_Port and Y is an E_Port
C. X is an F_Port and Y is an F_Port
D. X is an N_Port and Y is an N_Port
-
Question 64:
What is a function of the NDMP server in an NDMP-based backup approach?
A. Reads the data from the storage device and sends the data to the backup device
B. Reads the data from the backup server and sends the data to the backup device
C. Instructs the NAS head to start the backup operation
D. Instructs the backup agent on the client to send the data to the backup device
-
Question 65:
What is an accurate statement about OpenID control?
A. Enables an organization to use authentication services from an identity provider
B. Enables initiators and targets to authenticate each other by using a shared secret code
C. Provides strong authentication for client-server applications by using secret-key cryptography
D. Allows a client to access protected resources from a resource server on behalf of a resource owner
-
Question 66:
What is an accurate statement about three-way NDMP backup in a NAS environment?
A. Backup data is sent directly from NAS to the backup device
B. Backup data is sent to the backup device through the application servers
C. A dedicated backup device is required for each NAS
D. All NAS systems should have the same operating environment
-
Question 67:
Which EMC product is a VNX array-based local replication software that creates a full volume mirror of the source?
A. SnapView Snapshot
B. SnapView Clone
C. TimeFinder/Snap
D. TimeFinder/Clone
-
Question 68:
An organization has several virtual machines (VMs) deployed in their data center. The VM files are stored on a block-based storage system. The applications on the VMs are impacted during VM backup because the backup agents on the VMs are consuming a large amount of resources.
Which alternate backup solution is recommended to address this issue?
A. Image-based backup
B. Three-way NDMP backup
C. Two-way NDMP backup
D. Target-based deduplication backup
-
Question 69:
In a copy on first access (CoFA) technique, when is data copied from the source to the target?
A. All writes are issued to a location on the source
B. All writes are issued to a location on the target
C. A read or write is issued for the first time to a location on the target
D. A read is issued for the first time from a location on the source
-
Question 70:
What determines how far back the recovery points can go in a continuous data protection (CDP) solution?
A. Amount of space that is configured for the journal
B. Size of the CDP appliance used for replication
C. Size of the source and replica volumes
D. Type of write splitter used for replication
Related Exams:
D-GAI-F-01
Dell GenAI Foundations AchievementD-MSS-DS-23
Dell Midrange Storage Solutions Design 2023D-OME-OE-A-24
Dell OpenManage Operate AchievementD-PDD-DY-23
Dell PowerProtect DD Deploy 2023D-PE-OE-23
Dell PowerEdge Operate 2023D-PEXE-IN-A-00
Dell PowerEdge XE9680 and XE8640 InstallD-PSC-MN-01
Dell GenAI Foundations AchievementD-PST-MN-A-24
Dell PowerStore Maintenance AchievementD-PWF-DS-23
Dell PowerFlex Design 2023D-RP-DY-A-24
Dell RecoverPoint Deploy Achievement
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EMC exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your E05-001 exam preparations and EMC certification application, do not hesitate to visit our Vcedump.com to find your solutions here.