Exam Details
Exam Code
:E05-001Exam Name
:Information Storage and Management v3Certification
:EMC CertificationsVendor
:EMCTotal Questions
:186 Q&AsLast Updated
:Apr 25, 2025
EMC EMC Certifications E05-001 Questions & Answers
-
Question 31:
What is an activity in the risk assessment step of risk management?
A. Determine the likelihood of a risk
B. Plan and deploy security controls
C. Continuously observe the existing risks
D. Identify the sources of threats that increase the risks
-
Question 32:
In an FC SAN environment, which security mechanism prevents a switch port from being enabled even after a switch reboot?
A. Port locking
B. Port type locking
C. Port binding
D. Fabric binding
-
Question 33:
In a virtualized environment, which method enables a virtual machine to be rolled back in case of a logical corruption to the virtual machine?
A. Virtual volume replication
B. VM snapshot
C. Storage array volume replication
D. VM clone
-
Question 34:
In continuous data protection (CDP) remote replication, where are the two split write I/Os of an incoming write I/O directed?
A. One I/O goes to the local CDP appliance and the other I/O goes to the production volume
B. One I/O goes to the compute system and the other I/O goes to the production volume
C. One I/O goes to the remote CDP appliance and the other I/O goes to the replica
D. One I/O goes to the journal volume and the other I/O goes to the replica
-
Question 35:
What enables an administrator to create device groups in an IP-SAN for restricting device communications to a group?
A. iSNS discovery domain
B. NIC teaming
C. Demilitarized zone
D. Security identifier
-
Question 36:
An administrator has defined a backup policy. Full backups will be performed at 8 PM every Monday and incremental backups performed at 8 PM the remaining days.
How many backup copies are required to restore the files if they were accidentally deleted on Friday morning?
A. 1
B. 2
C. 3
D. 4
-
Question 37:
Which method is used to establish a VPN connection between a primary and remote data center to perform secure remote replication?
A. Site-to-site VPN connection
B. Remote access VPN connection
C. Intra-site VPN connection
D. Long distance VPN connection
-
Question 38:
An organization plans to deploy a deduplication solution by retaining their legacy backup application. They are concerned about the application servers' performance and a long backup window during backups.
Which deduplication solution(s) should be recommended to the organization?
A. Post-process
B. Source-based global deduplication
C. Variable-length segment and source-based
D. Fixed-length block and source-based
-
Question 39:
The exhibit represents an FCIP tunnel configuration that merges the two FC SANs at either end of the tunnel. Which types of ports do the labels "X" and "Y" represent on the FCIP gateway shown in the exhibit?
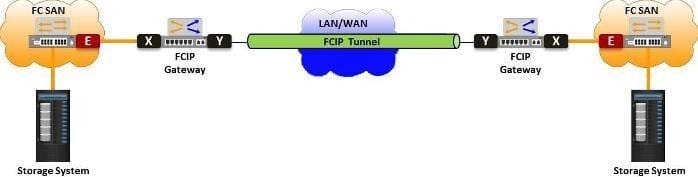
A. X = E_Port and Y = VE_Port
B. X = F_Port and Y = VN_Port
C. X =VF_Port and Y = E_Port
D. X = VN_Port and Y = VE_Port
-
Question 40:
A service provider is offering cloud services to Enterprise P and Enterprise Q.
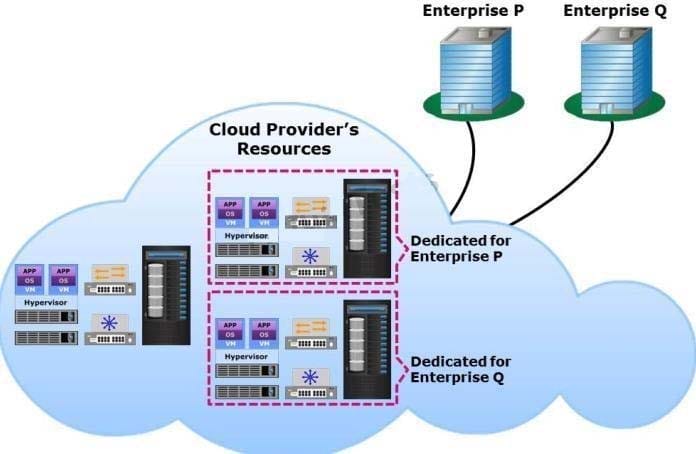
Which cloud deployment model does the exhibit represent?
A. Externally-hosted private cloud
B. On-premise community cloud
C. Public cloud
D. Externally-hosted community cloud
Related Exams:
D-GAI-F-01
Dell GenAI Foundations AchievementD-MSS-DS-23
Dell Midrange Storage Solutions Design 2023D-OME-OE-A-24
Dell OpenManage Operate AchievementD-PDD-DY-23
Dell PowerProtect DD Deploy 2023D-PE-OE-23
Dell PowerEdge Operate 2023D-PEXE-IN-A-00
Dell PowerEdge XE9680 and XE8640 InstallD-PSC-MN-01
Dell GenAI Foundations AchievementD-PST-MN-A-24
Dell PowerStore Maintenance AchievementD-PWF-DS-23
Dell PowerFlex Design 2023D-RP-DY-A-24
Dell RecoverPoint Deploy Achievement
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EMC exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your E05-001 exam preparations and EMC certification application, do not hesitate to visit our Vcedump.com to find your solutions here.