Exam Details
Exam Code
:CAS-003Exam Name
:CompTIA Advanced Security Practitioner (CASP+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:791 Q&AsLast Updated
:Jan 22, 2024
CompTIA CompTIA Certifications CAS-003 Questions & Answers
-
Question 151:
Designing a system in which only information that is essential for a particular job task is allowed to be viewed can be accomplished successfully by using:
A. mandatory vacations.
B. job rotations
C. role-based access control
D. discretionary access
E. separation of duties
-
Question 152:
A security manager is determining the best DLP solution for an enterprise A list of requirements was created to use during the source selection. The security manager wants to confirm a solution exists for the requirements that have been defined. Which of the following should the security manager use?
A. NDA
B. RFP
C. RFQ
D. MSA
E. RFI
-
Question 153:
A Chief Information Security Officer (CISO) is running a test to evaluate the security of the corporate network and attached devices. Which of the following components should be executed by an outside vendor?
A. Penetration tests
B. Vulnerability assessment
C. Tabletop exercises
D. Blue-team operations
-
Question 154:
Following the most recent patch deployment, a security engineer receives reports that the ERP application is no longer accessible. The security engineer reviews the situation and determines a critical security patch that was applied to the ERP server is the cause. The patch is subsequently backed out Which of the following security controls would be BEST to implement to mitigate the threat caused by the missing patch?
A. Anti-malware
B. Patch testing
C. HIPS
D. Vulnerability scanner
-
Question 155:
A DevOps team wants to move production data into the QA environment for testing. This data contains credit card numbers and expiration dates that are not tied to any individuals The security analyst wants to reduce risk. Which of the following will lower the risk before moving the data?
A. Redacting all but the last four numbers of the cards
B. Hashing the card numbers
C. Scrambling card and expiration data
D. Encrypting card and expiration numbers
-
Question 156:
A remote user reports the inability to authenticate to the VPN concentrator. During troubleshooting, a security administrator captures an attempted authentication and discovers the following being presented by the user's VPN client: Which of the following BEST describes the reason the user is unable to connect to the VPN service?
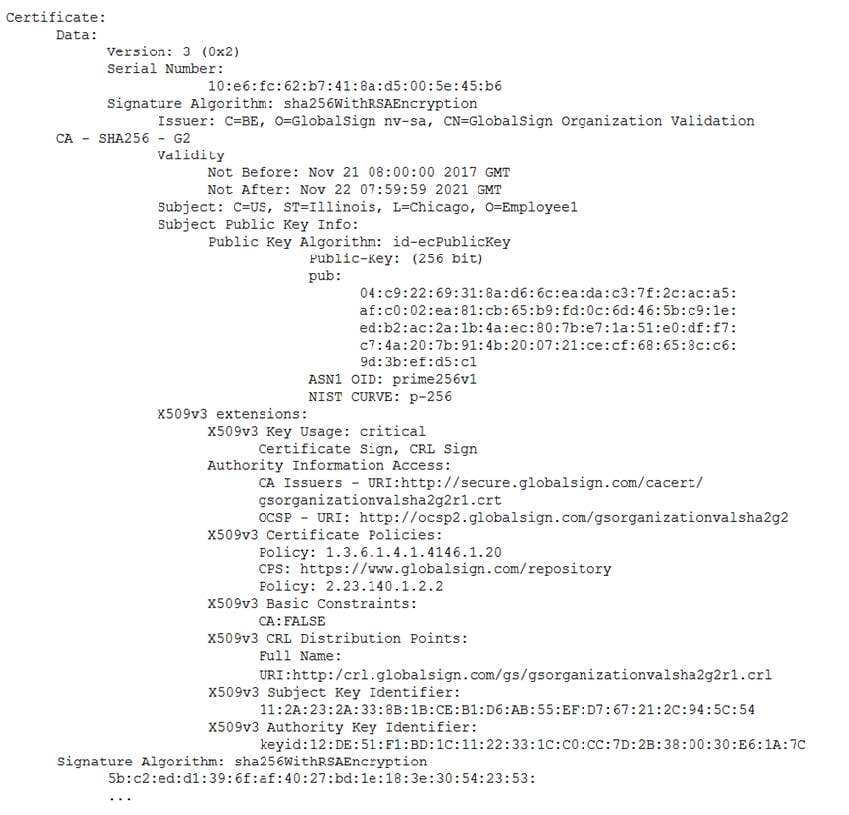
A. The user's certificate is not signed by the VPN service provider
B. The user's certificate has been compromised and should be revoked.
C. The user's certificate was not created for VPN use
D. The user's certificate was created using insecure encryption algorithms
-
Question 157:
A large, multinational company currently has two separate databases One is used for ERP while the second is used for CRM To consolidate services and infrastructure, it is proposed to combine the databases The company's compliance manager is asked to review the proposal and is concerned about this integration Which of the following would pose the MOST concern to the compliance manager?
A. The attack surface of the combined database is lower than the previous separate systems, so there likely are wasted resources on additional security controls that will not be needed
B. There are specific regulatory requirements the company might be violating by combining these two types of services into one shared platform.
C. By consolidating services in this manner, there is an increased risk posed to the organization due to the number of resources required to manage the larger data pool.
D. Auditing the combined database structure will require more short-term resources, as the new system will need to be learned by the auditing team to ensure all security controls are in
-
Question 158:
Which of the following risks does expanding business into a foreign country carry?
A. Data sovereignty laws could result in unexpected liability
B. Export controls might decrease software costs
C. Data ownership might revert to the regulatory entities in the new country
D. Some security tools might be monitored by legal authorities
-
Question 159:
A security analyst has been assigned incident response duties and must instigate the response on a Windows device that appears to be compromised. Which of the following commands should be executed on the client FIRST?
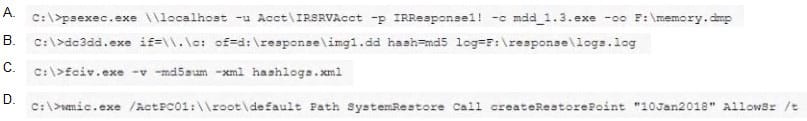
A. Option A
B. Option B
C. Option C
D. Option D
-
Question 160:
The Chief Information Security Officer (CISO) of an organization is concerned with the transmission of cleartext authentication information across the enterprise. A security assessment has been performed and has identified the use of ports
80. 389. and 3268. Which of the following solutions would BEST address the CISO's concerns?
A. Disable the ports that are determined to contain authentication information
B. Force HTTPS. enable LDAPS. and disable cleartext global catalog communication.
C. Deploy a VPN between networks that transmits authentication information via cleartext
D. Proxy HTTP traffic and migrate to a more secure directory service
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-1202
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CAS-003 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.