Exam Details
Exam Code
:CAS-003Exam Name
:CompTIA Advanced Security Practitioner (CASP+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:791 Q&AsLast Updated
:Jan 22, 2024
CompTIA CompTIA Certifications CAS-003 Questions & Answers
-
Question 161:
A company wants to implement a cloud-based security solution that will sinkhole malicious DNS requests. The security administrator has implemented technical controls to direct DNS requests to the cloud servers but wants to extend the solution to all managed and unmanaged endpoints that may have user-defined DNS manual settings Which of the following should the security administrator implement to ensure the solution will protect all connected devices?
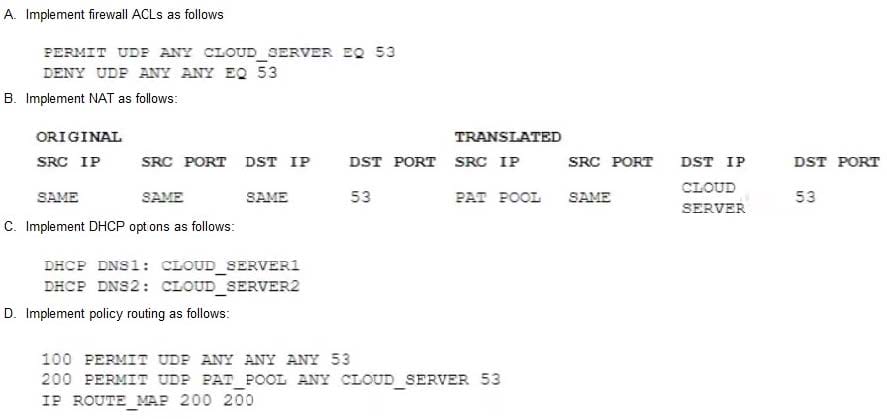
A. Option A
B. Option B
C. Option C
D. Option D
-
Question 162:
An organization is integrating an ICS and wants to ensure the system is cyber resilient. Unfortunately, many of the specialized components are legacy systems that cannot be patched. The existing enterprise consists of mission-critical systems that require 99.9% uptime. To assist in the appropriate design of the system given the constraints, which of the following MUST be assumed?
A. Vulnerable components
B. Operational impact due to attack
C. Time criticality of systems
D. Presence of open-source software
-
Question 163:
A small firm's newly created website has several design flaws The developer created the website to be fully compatible with ActiveX scripts in order to use various digital certificates and trusting certificate authorities. However, vulnerability testing indicates sandboxes were enabled, which restricts the code's access to resources within the user's computer. Which of the following is the MOST likely cause of the error?
A. The developer inadvertently used Java applets.
B. The developer established a corporate account with a non-reputable certification authority.
C. The developer used fuzzy logic to determine how the web browser would respond once ports 80 and 443 were both open
D. The developer did not consider that mobile code would be transmitted across the network.
-
Question 164:
A company is implementing a new secure identity application, given the following requirements
1.
The cryptographic secrets used in the application must never be exposed to users or the OS
2.
The application must work on mobile devices.
3.
The application must work with the company's badge reader system
Which of the following mobile device specifications are required for this design? (Select TWO).
A. Secure element
B. Biometrics
C. UEFI
D. SEAndroid
E. NFC
F. HSM
-
Question 165:
An engineer wants to assess the OS security configurations on a company's servers. The engineer has downloaded some files to orchestrate configuration checks When the engineer opens a file in a text editor, the following excerpt appears:

Which of the following capabilities would a configuration compliance checker need to support to interpret this file?
A. Nessus
B. Swagger file
C. SCAP
D. Netcat
E. WSDL
-
Question 166:
An employee decides to log into an authorized system. The system does not prompt the employee for authentication prior to granting access to the console, and it cannot authenticate the network resources. Which of the following attack types can this lead to if it is not mitigated?
A. Memory leak
B. Race condition
C. Smurf
D. Resource exhaustion
-
Question 167:
An e-commerce company that provides payment gateways is concerned about the growing expense and time associated with PCI audits of its payment gateways and external audits by customers for their own compliance reasons The Chief Information Officer (CIO) asks the security team to provide a list of options that will:
1.
Reduce the overall cost of these audits
2.
Leverage existing infrastructure where possible
3.
Keep infrastructure costs to a minimum
4.
Provide some level of attestation of compliance
Which of the following will BEST address the CIO"s concerns? (Select TWO)
A. Invest in new UBA to detect report, and remediate attacks faster
B. Segment the network to reduce and limit the audit scope
C. Undertake ISO certification for all core infrastructure including datacenters.
D. Implement a GRC system to track and monitor controls
E. Implement DLP controls on HTTP'HTTPS and email
F. Install EDR agents on all corporate endpoints
-
Question 168:
A company has completed the implementation of technical and management controls as required by its adopted security, ponies and standards. The implementation took two years and consumed s the budget approved to security projects. The board has denied any further requests for additional budget. Which of the following should the company do to address the residual risk?
A. Transfer the risk
B. Baseline the risk.
C. Accept the risk
D. Remove the risk
-
Question 169:
Following a recent security incident on a web server the security analyst takes HTTP traffic captures for further investigation The analyst suspects certain jpg files have important data hidden within them. Which of the following tools will help get all the pictures from within the HTTP traffic captured to a specified folder?
A. tshark
B. memdump
C. nbtstat
D. dd
-
Question 170:
Given the following information about a company's internal network:
User IP space: 192.168.1.0/24 Server IP space: 192.168.192.0/25
A security engineer has been told that there are rogue websites hosted outside of the proper server space, and those websites need to be identified. Which of the following should the engineer do?
A. Use a protocol analyzer on 192.168.1.0/24
B. Use a port scanner on 192.168.1.0/24
C. Use an HTTP interceptor on 192.168.1.0/24
D. Use a port scanner on 192.168.192.0/25
E. Use a protocol analyzer on 192.168.192.0/25
F. Use an HTTP interceptor on 192.168.192.0/25
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-1202
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CAS-003 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.