Exam Details
Exam Code
:CAS-003Exam Name
:CompTIA Advanced Security Practitioner (CASP+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:791 Q&AsLast Updated
:Jan 22, 2024
CompTIA CompTIA Certifications CAS-003 Questions & Answers
-
Question 141:
After analyzing code, two developers al a company bring these samples to the security operations manager.

Which of the following would BEST solve these coding problems?
A. Use a privileged access management system
B. Prompt the administrator for the password .
C. Use salted hashes with PBKDF2.
D. Increase the complexity and length of the password
-
Question 142:
The Chief Information Security Officer (CISO) of a company that has highly sensitive corporate locations wants its security engineers to find a solution to growing concerns regarding mobile devices The CISO mandates the following requirements:
1.
The devices must be owned by the company for legal purposes.
2.
The device must be as fully functional as possible when off site.
3.
Corporate email must be maintained separately from personal email
4.
Employees must be able to install their own applications.
Which of the following will BEST meet the CISO's mandate? (Select TWO).
A. Disable the device's camera
B. Allow only corporate resources in a container.
C. Use an MDM to wipe the devices remotely
D. Block all sideloading of applications on devices
E. Use geofencmg on certain applications
F. Deploy phones in a BYOD model
-
Question 143:
A company recently migrated to a SaaS-based email solution. The solution is configured as follows:
1.
Passwords are synced to the cloud to allow for SSO
2.
Cloud-based antivirus is enabled
3.
Cloud-based anti-spam is enabled
4.
Subscription-based blacklist is enabled
Although the above controls are enabled, the company's security administrator is unable to detect an account compromise caused by phishing attacks in a timely fashion because email logs are not immediately available to review. Which of the following would allow the company to gam additional visibility and reduce additional costs? (Select TWO)
A. Migrate the email antivirus and anti-spam on-premises
B. Implement a third-party CASB solution.
C. Disable the current SSO model and enable federation
D. Feed the attacker IPs from the company IDS into the email blacklist
E. Install a virtual SIEM within the email cloud provider
F. Add email servers to NOC monitoring
-
Question 144:
A company enlists a trusted agent to implement a way to authenticate email senders positively Which of the following is the BEST method for the company to prove Vie authenticity of the message?
A. issue PlN-enabled hardware tokens
B. Create a CA win all users
C. Configure the server to encrypt all messages in transit
D. include a hash in the body of the message
-
Question 145:
A security engineer is making certain URLs from an internal application available on the Internet The development team requires the following
1.
The URLs are accessible only from internal IP addresses
2.
Certain countries are restricted
3.
TLS is implemented.
4.
System users transparently access internal application services in a round robin to maximize performance
Which of the following should the security engineer deploy7
A. DNS to direct traffic and a WAF with only the specific external URLs configured
B. A load balancer with GeolP restrictions and least-load-sensing traffic distribution
C. An application-aware firewall with geofencing and certificate services using DNS for traffic direction
D. A load balancer with IP ACL restrictions and a commercially available PKI certificate
-
Question 146:
An organization relies heavily on third-party mobile applications for official use within a BYOD deployment scheme. An excerpt from an approved text-based-chat client application AndroidManifest.xml is as follows:
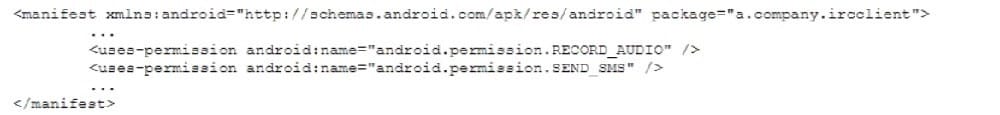
Which of the following would restrict application permissions while minimizing the impact to normal device operations?
A. Add the application to the enterprise mobile whitelist.
B. Use the MDM to disable the devices' recording microphones and SMS
C. Wrap the application before deployment
D. Install the application outside of the corporate container
-
Question 147:
After a large organization has completed the acquisition of a smaller company, the smaller company must implement new host-based security controls to connect its employees' devices to the network. Given that the network requires 802.1X EAP-PEAP to identify and authenticate devices, which of the following should the security administrator do to integrate the new employees devices into the network securely?
A. Distribute a NAC client and use the client to push the company's private key to all the new devices.
B. Distribute the device connection policy and a unique public/private key pair to each new employee's device.
C. Install a self-signed SSL certificate on the company's RADIUS server and distribute the certificate's public key to all new client devices.
D. Install an 802.1X supplicant on all new devices and let each device generate a self- signed certificate to use for network access.
-
Question 148:
A company is concerned about disgruntled employees transferring its intellectual property data through covert channels. Which of the following tools would allow employees to write data into ICMP echo response packets?
A. Thor
B. Jack the Ripper
C. Burp Suite
D. Loki
-
Question 149:
A company contracts a security consultant to perform a remote white-box penetration test. The company wants the consultant to focus on Internet-facing services without negatively impacting production services Which of the following is the consultant MOST likely to use to identify the company's attack surface? (Select TWO)
A. Web crawler
B. WHOIS registry
C. DNS records
D. Company's firewall ACL
E. Internal routing tables
F. Directory service queries
-
Question 150:
The information security manager of an e-commerce company receives an alert over the weekend that all the servers in a datacenter have gone offline Upon discussing this situation with the facilities manager, the information security manager learns there was planned electrical maintenance. The information security manager is upset at not being part of the maintenance planning, as this could have resulted in a loss of:
A. data confidentiality.
B. data security.
C. PCI compliance
D. business availability.
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-1202
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CAS-003 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.