Exam Details
Exam Code
:CAS-003Exam Name
:CompTIA Advanced Security Practitioner (CASP+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:791 Q&AsLast Updated
:Jan 22, 2024
CompTIA CompTIA Certifications CAS-003 Questions & Answers
-
Question 171:
A Chief Information Security Officer (CISO) has created a survey that will be distributed to managers of mission-critical functions across the organization The survey requires the managers to determine how long their respective units can operate in the event of an extended IT outage before the organization suffers monetary losses from the outage To which of the following is the survey question related? (Select TWO)
A. Risk avoidance
B. Business impact
C. Risk assessment
D. Recovery point objective
E. Recovery time objective
F. Mean time between failures
-
Question 172:
A hospital is using a functional magnetic resonance imaging (fMRI) scanner, which is controlled legacy desktop connected to the network. The manufacturer of the fMRI will not support patching of the legacy system. The legacy desktop needs to be network accessible on TCP port 445 A security administrator is concerned the legacy system will be vulnerable to exploits Which of the following would be the BEST strategy to reduce the risk of an outage while still providing for security?
A. Install HIDS and disable unused services.
B. Enable application whitelisting and disable SMB.
C. Segment the network and configure a controlled interface
D. Apply only critical security patches for known vulnerabilities.
-
Question 173:
A security engineer discovers a PC may have been breached and accessed by an outside agent. The engineer wants to find out how this breach occurred before remediating the damage. Which of the following should the security engineer do FIRST to begin this investigation?
A. Create an image of the hard drive
B. Capture the incoming and outgoing network traffic
C. Dump the contents of the RAM
D. Parse the PC logs for information on the attacker.
-
Question 174:
As part of an organization's ongoing vulnerability assessment program, the Chief Information Security Officer (CISO) wants to evaluate the organization's systems, personnel, and facilities for various threats As part of the assessment the CISO plans to engage an independent cybersecurity assessment firm to perform social engineering and physical penetration testing against the organization's corporate offices and remote locations. Which of the following techniques would MOST likely be employed as part of this assessment? (Select THREE).
A. Privilege escalation
B. SQL injection
C. TOC/TOU exploitation
D. Rogue AP substitution
E. Tailgating
F. Vulnerability scanning
G. Vishing
H. Badge skimming
-
Question 175:
A security engineer wants to introduce key stretching techniques to the account database to make password guessing attacks more difficult Which of the following should be considered to achieve this? (Select TWO)
A. Digital signature
B. bcrypt
C. Perfect forward secrecy
D. SHA-256
E. P-384
F. PBKDF2
G. Record-level encryption
-
Question 176:
A company is deploying a DIP solution and scanning workstations and network drives for documents that contain potential Pll and payment card data. The results of the first scan are as follows:
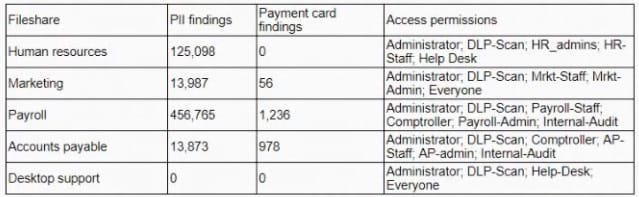
The security learn is unable to identify the data owners for the specific files in a timely manner and does not suspect malicious activity with any of the detected files. Which of the following would address the inherent risk until the data owners can be formally identified?
A. Move the files from the marketing share to a secured drive.
B. Search the metadata for each file to locate the file's creator and transfer the files to the personal drive of the listed creator.
C. Configure the DLP tool to delete the files on the shared drives
D. Remove the access for the internal audit group from the accounts payable and payroll shares
-
Question 177:
An attacker wants to gain information about a company's database structure by probing the database listener. The attacker tries to manipulate the company's database to see if it has any vulnerabilities that can be exploited to help carry out an attack. To prevent this type of attack, which of the following should the company do to secure its database?
A. Mask the database banner
B. Tighten database authentication and limit table access
C. Harden web and Internet resources
D. Implement challenge-based authentication
-
Question 178:
An organization based in the United States is planning to expand its operations into the European market later in the year Legal counsel is exploring the additional requirements that must be established as a result of the expansion. The BEST course of action would be to:
A. revise the employee provisioning and deprovisioning procedures
B. complete a quantitative risk assessment
C. draft a memorandum of understanding
D. complete a security questionnaire focused on data privacy.
-
Question 179:
A security administrator is performing an audit of a local network used by company guests and executes a series of commands that generates the following output:
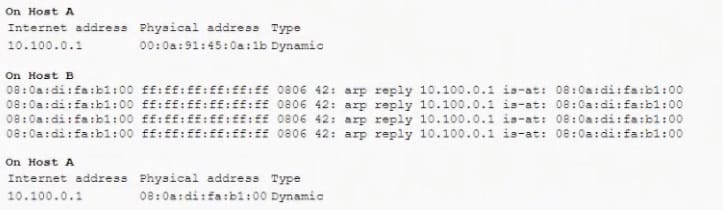
Which of the following actions should the security administrator take to BEST mitigate the issue that transpires from the above information?
A. Implement switchport security
B. Implement 802 1X
C. Enforce static ARP mappings using GPO
D. Enable unicast RPF
-
Question 180:
A financial services company has proprietary trading algorithms, which were created and are maintained by a team of developers on their private source code repository. If the details of this operation became known to competitors, the company's ability to profit from its trading would disappear immediately. Which of the following would the company MOST likely use to protect its trading algorithms?
A. Single-tenancy cloud
B. Managed security service providers
C. Virtual desktop infrastructure
D. Cloud security broker
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-1202
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CAS-003 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.