Exam Details
Exam Code
:412-79V10Exam Name
:EC-Council Certified Security Analyst (ECSA) V10Certification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:201 Q&AsLast Updated
:Jun 27, 2025
EC-COUNCIL EC-COUNCIL Certifications 412-79V10 Questions & Answers
-
Question 181:
In the TCP/IP model, the transport layer is responsible for reliability and flow control from source to the destination. TCP provides the mechanism for flow control by allowing the sending and receiving hosts to communicate. A flow control mechanism avoids the problem with a transmitting host overflowing the buffers in the receiving host.
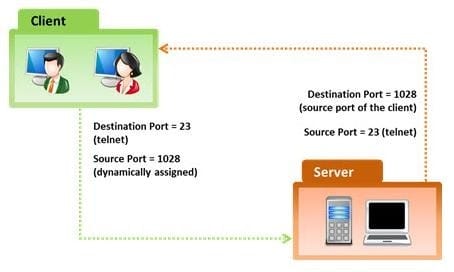
Which of the following flow control mechanism guarantees reliable delivery of data?
A. Sliding Windows
B. Windowing
C. Positive Acknowledgment with Retransmission (PAR)
D. Synchronization
-
Question 182:
The SnortMain () function begins by associating a set of handlers for the signals, Snort receives. It does this using the signal () function. Which one of the following functions is used as a programspecific signal and the handler for this calls the DropStats() function to output the current Snort statistics?
A. SIGUSR1
B. SIGTERM
C. SIGINT
D. SIGHUP
-
Question 183:
SQL injection attack consists of insertion or "injection" of either a partial or complete SQL query via the
data input or transmitted from the client (browser) to the web application.
A successful SQL injection attack can:
i)Read sensitive data from the database
iii)Modify database data (insert/update/delete)
iii)Execute administration operations on the database (such as shutdown the DBMS)
iV)Recover the content of a given file existing on the DBMS file system or write files into the file system
v)Issue commands to the operating system
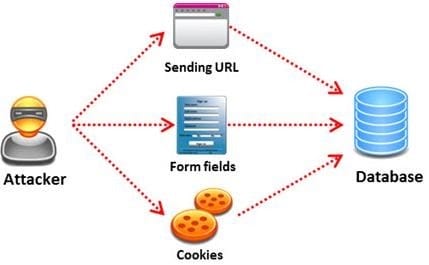
Pen tester needs to perform various tests to detect SQL injection vulnerability. He has to make a list of all input fields whose values could be used in crafting a SQL query, including the hidden fields of POST requests and then test them separately, trying to interfere with the query and to generate an error.
In which of the following tests is the source code of the application tested in a non-runtime environment to detect the SQL injection vulnerabilities?
A. Automated Testing
B. Function Testing
C. Dynamic Testing
D. Static Testing
-
Question 184:
Which of the following documents helps in creating a confidential relationship between the pen tester and client to protect critical and confidential information or trade secrets?
A. Penetration Testing Agreement
B. Rules of Behavior Agreement
C. Liability Insurance
D. Non-Disclosure Agreement
-
Question 185:
Which of the following is developed to address security concerns on time and reduce the misuse or threat of attacks in an organization?
A. Vulnerabilities checklists
B. Configuration checklists
C. Action Plan
D. Testing Plan
-
Question 186:
One of the steps in information gathering is to run searches on a company using complex keywords in Google.

Which search keywords would you use in the Google search engine to find all the PowerPoint presentations containing information about a target company, ROCHESTON?
A. ROCHESTON fileformat:+ppt
B. ROCHESTON ppt:filestring
C. ROCHESTON filetype:ppt
D. ROCHESTON +ppt:filesearch
-
Question 187:
How many bits is Source Port Number in TCP Header packet?
A. 48
B. 32
C. 64
D. 16
-
Question 188:
Which one of the following tools of trade is an automated, comprehensive penetration testing product for assessing the specific information security threats to an organization?
A. Sunbelt Network Security Inspector (SNSI)
B. CORE Impact
C. Canvas
D. Microsoft Baseline Security Analyzer (MBSA)
-
Question 189:
DMZ is a network designed to give the public access to the specific internal resources and you might want to do the same thing for guests visiting organizations without compromising the integrity of the internal resources. In general, attacks on the wireless networks fall into four basic categories. Identify the attacks that fall under Passive attacks category.(Select all that apply)
A. Wardriving
B. Spoofing
C. Sniffing
D. Network Hijacking
-
Question 190:
Which one of the following is a supporting tool for 802.11 (wireless) packet injections, it spoofs 802.11 packets to verify whether the access point is valid or not?
A. Airsnort
B. Aircrack
C. Airpwn
D. WEPCrack
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-055
Sun Certified Programmer for the Java 2 Platform.SE 5.0212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 412-79V10 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.