Exam Details
Exam Code
:352-001Exam Name
:CCDE WrittenCertification
:Cisco CertificationsVendor
:CiscoTotal Questions
:705 Q&AsLast Updated
:Jul 03, 2023
Cisco Cisco Certifications 352-001 Questions & Answers
-
Question 661:
Which resource does a TCP SYN flood attack target?
A. connection tables on the target host
B. send buffers on transit routers
C. shared memory on the routers closest to the target
D. SYN cookies on the target host
-
Question 662:
What are three key design principles when using a classic hierarchical network model? (Choose three.)
A. The core layer controls access to resources for security.
B. The core layer should be configured with minimal complexity.
C. The core layer is designed first, followed by the distribution layer and then the access layer.
D. A hierarchical network design model aids fault isolation.
E. The core layer provides server access in a small campus.
F. A hierarchical network design facilitates changes.
-
Question 663:
Why might you want to synchronize IGP and BGP convergence by advertising an infinite metric in OSPF or setting the overload bit in IS-IS?
A. to prevent traffic loss when the path from a router to a BGP next hop traverses another router that has not yet learned the path via BGP
B. to prevent BGP from converging faster than IGP, which can cause temporary routing loops in the network
C. to prevent routes which are learned both from IGP and BGP from forming a routing loop
D. to prevent churning between multiple available routes reachable through IGP and BGP
-
Question 664:
A large enterprise customer is migrating thousands of retail offices from legacy TDM circuits to an Ethernetbased service. The network is running OSPF and has been stable for many years. It is now possible to backhaul the circuits directly to the data centers, bypassing the regional aggregation routers. Which two networking issues need to be addressed to ensure stability with the new design? (Choose two.)
A. Nothing will change if the number of offices is the same.
B. Nothing will change if the number of physical interfaces stays the same.
C. The RIB will increase significantly.
D. The FIB will increase significantly.
E. The amount of LSA flooding will increase significantly.
F. The size of the link-state database will increase significantly.
-
Question 665:
You are designing an optical network. Your goal is to ensure that your design contains the highest degree of resiliency. In which two ways will you leverage a wavelength-switched optical network solution in your network design? (Choose two.)
A. a wavelength-switched optical network assigns routing and wavelength information
B. a wavelength-switched optical network takes linear and nonlinear optical impairment calculation into account
C. a wavelength-switched optical network guarantees restoration based strictly on the shortest path available
D. a wavelength-switched optical network eliminates the need for dispersion compensating units in a network
-
Question 666:
You are the lead network designer hired by Service Provider XYZ to deploy CoS functionality on the core MPLS network (P routers). The goal of the network design is to provide a complete CoS solution to all customers that purchase services such as dedicated internet access, MPLS L3VPN, and L2VPN (pseudowire). Service Provider XYZ has these design requirements:
The network supports four service queues with equal treatment for delay, jitter, and packet loss.
Queues are numbered 0-3, where 0 is the default queue.
Three queues have one treatment.
One queue has either one or two treatments.
How would you design your solution to map the DSCP value properly so that the traffic is assigned to the respective queues in the Service Provider XYZ MPLS core network?
A. Classify traffic according to DSCP value into appropriate P router queues.
B. Map the appropriate DSCP value into the EXP field based on the number of queues in the MPLS P routers.
C. Map the appropriate DSCP value into the EXP field based on the number of queues in the MPLS PE routers.
D. Based on the DSCP value, traffic is mapped automatically into appropriate queues in the MPLS CE routers.
-
Question 667:
You are a network designer and have been asked to consult with your server operations team to further enhance the security of the network. The operations team provides you with these details about the network:
A pool of servers is accessed by numerous data centers and remote sites. The servers are accessed via a cluster of firewalls.
The firewalls are configured properly and are not dropping traffic.
The firewalls occasionally cause asymmetric routing of traffic within the server data center.
Which technology would you recommend to enhance security by limiting traffic that could originate from a hacker compromising a workstation and redirecting flows at the servers?
A. Access control lists to limit sources of traffic that exits the server-facing interface of the firewall cluster
B. Poison certain subnets by adding static routes to Null0 on the server farm core switches.
C. Unicast Reverse Path Forwarding in strict mode
D. Unicast Reverse Path Forwarding in loose mode
-
Question 668:
Refer to the exhibit.
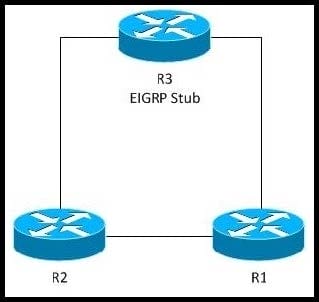
This diagram depicts the design of a small network that will run EIGRP on R1 and R2, and EIGRP Stub on R3. In which two ways will this network be impacted if there is link instability between R1 and R2? (Choose two.)
A. R1 will have routes in its routing table that originate from R2 and R3.
B. R3 will have routes in its routing table that originate from R1 and R2.
C. R2 will have routes in its routing table that originate from R1 and R3.
D. R3 will be transit for traffic between R1 and R2.
E. R3 will not be transit for traffic between R1 and R2.
-
Question 669:
FIFO queuing is being used on all routers in a network. The primary application running on the network is data backup using FTP. At certain times, users experience cyclical performance degradation.
What two things might mitigate this problem and help ensure bandwidth is used effectively in the network? (Choose two.)
A. traffic shaping
B. CB-WFQ
C. traffic policing
D. WRED
E. MDRR
-
Question 670:
Your firm has been awarded a contract to design a Criminal Justice Information Services Version 5.0-compliant network utilizing advanced authentication policies. Which two methods could be utilized? (Choose two.)
A. biometric
B. PKI
C. UKI
D. password
Related Exams:
300-915
Developing Solutions using Cisco IoT and Edge Platforms (DEVIOT)300-920
Developing Applications for Cisco Webex and Webex Devices (DEVWBX)352-011
Cisco Certified Design Expert Practical500-052
Cisco Unified Contact Center Express500-173
Designing the FlexPod Solution (FPDESIGN)500-174
Implementing and Administering the FlexPod Solution (FPIMPADM)500-201
Deploying Cisco Service Provider Mobile Backhaul Solutions500-210
SP Optical Technology Field Engineer Representative500-220
Cisco Meraki Solutions Specialist500-230
Cisco Service Provider Routing Field Engineer
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Cisco exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 352-001 exam preparations and Cisco certification application, do not hesitate to visit our Vcedump.com to find your solutions here.