Exam Details
Exam Code
:352-001Exam Name
:CCDE WrittenCertification
:Cisco CertificationsVendor
:CiscoTotal Questions
:705 Q&AsLast Updated
:Jul 03, 2023
Cisco Cisco Certifications 352-001 Questions & Answers
-
Question 1:
Refer to the exhibit. Which two features can be used to make multicast work in this situation? (Choose two.)
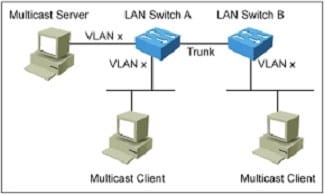
A. Disable IGMP snooping on both switches
B. Disable the IGMP query election process
C. Enable the IGMP querier feature on LAN switch A
D. Configure a static MAC entry for the multicast server
E. Disable PIM snooping on both switches
-
Question 2:
A network designer decides to connect two labs together to test multicast features interoperability. Before the networks are connected together, the network administrator mentions that overlapping multicast IP addresses between the two labs will cause issues because all the routers on the network are provisioned for Source-Specific Multicast using IGMPv3.
Which statement about the connectivity of both multicast domains is true?
A. IGMPv3 can support overlapping multicast IP addresses between the labs
B. IGMPv3 cannot support overlapping multicast IP addresses between the labs
C. IGMPv3 requires NAT to support the overlapping multicast IP addresses between the labs
D. IGMPv3 requires a unique RP when connecting both labs together
-
Question 3:
Company ABC has started to implement IPv6 in their network and has rolled out dual-stack endpoint devices to their employees. Which security measure prevents ABC from replay attacks?
A. IPv6 Source Guard
B. Router Advertisement Guard
C. IPv6 Destination Guard
D. SeND with Nonce
-
Question 4:
Which description of the RPF check in the multicast forwarding traffic is true?
A. The source address of the multicast packet is checked in the unicast routing table. If the multicast packet arrived from the interface that matches with the interface to reach the source address, this packet passes the RPF check.
B. The unicast address of the multicast packet is checked in the BGP database. If the multicast packet arrived from the interface that matches with the interface to reach BGP peer that advertised the multicast prefix, this packet passes the RPF check.
C. The destination address of the multicast packet is checked in the BGP database. If the multicast packet arrived from the interface that matches with the interface to reach BGP peer that advertised the multicast prefix, this packet fails the RPF check.
D. The source address of the multicast packet is checked in the unicast routing table. If the multicast packet arrived from the interface that matches with the interface to reach the source address, this packet fails the RPF check.
-
Question 5:
When designing a Source Specific Multicast solution, what must you consider?
A. It lacks support for URL Rendezvous Directory
B. Initial multicast traffic will flow over the RPT
C. The IANA assigned range is 232.0.0.0/8
D. Embedded RP can be used for RP discovery
-
Question 6:
The BGP table contains hundreds of thousands of routes. Which design technique improves the convergence time?
A. Enable TCP path MTU discovery to every neighbor
B. Use TCP ports higher than 1024 for your BGP sessions
C. Deploy BGP route reflectors instead of full-mesh iBGP
D. Deploy BGP confederations within your backbone
-
Question 7:
An existing wireless network was designed to support data traffic only. You must now install Context Aware services for location tracking.
Which two changes must be applied to the existing wireless network to increase the location accuracy? (Choose two.)
A. Use directional antennas to provide more cell overlapping
B. Install additional access points in monitor mode where the co-channel interference would otherwise be affected
C. Add access points along the perimeter of the coverage area
D. Increase the access point density to create an average inter-access point distance of less than 40 feet or 12.2 meters
E. Fine tune the radio configuration of the access point to have a higher average transmission power to achieve better coverage
-
Question 8:
A large enterprise network has two data centers and a WAN edge in a hub-and-spoke network topology. The entire network is in a single OSPF area. Spoke routers are connected to unreliable WAN links.
Which two changes must be made to deploy LSA filtering on the spoke routers? (Choose two.)
A. Configure the hub routers as ASBRs
B. Keep the spoke routers in normal areas
C. Configure the hub routers as ABRs
D. Place spoke routers in totally stubby areas
E. Place spoke routers in stub areas
-
Question 9:
Which ISAKMP feature can be used to reduce device CPU load by not sending keepalive messages for known active ISAKMP security associations?
A. DPD
B. IKEv2
C. SPI
D. main mode
-
Question 10:
A large enterprise customer has more than 300 worldwide locations, each with at least two different WAN connections to their five regional data centers across US, Europe, and Asia. These data centers offer different application services and work as primary, with a remote data center as backup. You must provide a solution to securely select the traffic path for specific applications based on an IT policy.
Which solution allows the easiest management of the path decision from the data center sites?
A. Apply policy-based routing at each remote site
B. Use LISP over the current WAN
C. Set up each center with its own AS and use BGP AS-PATH prepend configuration
D. Add Cisco MPLS TE devices in the data centers and activate Cisco MPLS TE
Related Exams:
300-915
Developing Solutions using Cisco IoT and Edge Platforms (DEVIOT)300-920
Developing Applications for Cisco Webex and Webex Devices (DEVWBX)352-011
Cisco Certified Design Expert Practical500-052
Cisco Unified Contact Center Express500-173
Designing the FlexPod Solution (FPDESIGN)500-174
Implementing and Administering the FlexPod Solution (FPIMPADM)500-201
Deploying Cisco Service Provider Mobile Backhaul Solutions500-210
SP Optical Technology Field Engineer Representative500-220
Cisco Meraki Solutions Specialist500-230
Cisco Service Provider Routing Field Engineer
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Cisco exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 352-001 exam preparations and Cisco certification application, do not hesitate to visit our Vcedump.com to find your solutions here.