Exam Details
Exam Code
:352-001Exam Name
:CCDE WrittenCertification
:Cisco CertificationsVendor
:CiscoTotal Questions
:705 Q&AsLast Updated
:Jul 03, 2023
Cisco Cisco Certifications 352-001 Questions & Answers
-
Question 521:
A designer is working with a large bank to redesign their network. The designer wants to minimize complaints regarding slow application response times across the WAN. It is suspected that currently traffic is not being classified and marked correctly somewhere in the network. Which tool should the designer recommend to validate quality of service mappings and use?
A. SNMP
B. IPFIX
C. IP SLA
D. protocol analyzer
E. NBAR
-
Question 522:
What are two benefits of protecting the control plane of a network device? (Choose two.)
A. prevents the delivery of packets from spoof sources
B. preserves the confidentiality of traffic encrypted by IPsec
C. maintains routing protocol adjacencies with local neighbors
D. maintains remote management access to the router
-
Question 523:
Voice traffic between two campus enterprise networks is growing. The network designers decide to add a second 10-Mb Metro Ethernet service parallel to their original 10-Mb service in order to provide more bandwidth and diversity. The QoS profile will be the same on the new 10-Mb service due to the voice stability on the first Metro Ethernet link. When the second link is added to the OSPF domain, which traffic design consideration would have the most impact on the voice traffic when both links are active?
A. per-destination IP address basis
B. per-flow basis
C. per-packet basis
D. per-source IP address basis
-
Question 524:
A network designer has provisioned a router to use IPsec to encrypt the traffic over a GRE tunnel going to a web server at a remote location. From the router, the network designer can ping the web server, although the users in the office comment that they are unable to reach it. (Note: The DF bit is not set.) Which aspect should be changed in the design of the virtual connection?
A. IP addresses of the GRE tunnel endpoints
B. IPsec configuration
C. MTU size on the GRE tunnel
D. encapsulation of the GRE tunnel
-
Question 525:
A network design shows two routers directly connected to an Ethernet switch using optical connections. There is an OSPF adjacency between the routers. In this design, which solution will ensure that interface down detection is reported as quickly as possible to the IGP?
A. optimized OSPF SPF timers
B. Bidirectional Forwarding Detection
C. automatic protection switching
D. optimized OSPF LSA timers
E. Ethernet OAM CFM monitoring
-
Question 526:
You work for a large company that has just acquired another smaller company. You have been asked to lead a group of SAN experts from both companies to design the integration plan that will be used to interconnect the SANs and migrate the data from the newly acquired company to the main storage arrays. The first thing that the team discovers is that the two SANs have the same domain IDs.
As the SAN team lead, what would you advise your team to do so that you can interconnect the two SANs while minimizing disruption?
A. Use FCIP with Write Acceleration and IVR version 1 with a transit VSAN to expedite the data transfer between the two SANs.
B. Change the domain IDs on both SANs so that they are both unique and then connect ISLs between the SANs.
C. Use IVR NAT with a transit VSAN between the SANs.
D. The two SANs cannot be merged without disruption.
-
Question 527:
You have been hired by Acme Corporation to evaluate their existing network and determine if the current network design is secure enough to prevent man-in-the-middle attacks. When evaluating the network, which switch security option should you investigate to ensure that authorized ARP responses take place according to known IP-to-MAC address mapping?
A. ARP rate limiting
B. DHCP snooping
C. Dynamic ARP Inspections
D. IP Source Guard
-
Question 528:
A new video multicast application is deployed in the network. The application team wants to use the 239.0.0.1 multicast group to stream the video to users. They want to know if this choice will impact the existing multicast design. What impact will their choice have on the existing multicast design?
A. Because 239.0.0.1 is a private multicast range, a flood of PIM packets that have to be processed by the CPU and hostswill be sent by the routers in the network.
B. Because 239.0.0.1 is a private multicast range, the rendezvous point has to send out constant group updates that will have to be processed by the CPU and hosts.
C. The multicast application sends too many packets into the network and the network infrastructure drops packets.
D. The 239.0.0.1 group address maps to a system MAC address, and all multicast traffic will have to be sent to the CPU and flooded out all ports.
-
Question 529:
Refer to the exhibit.
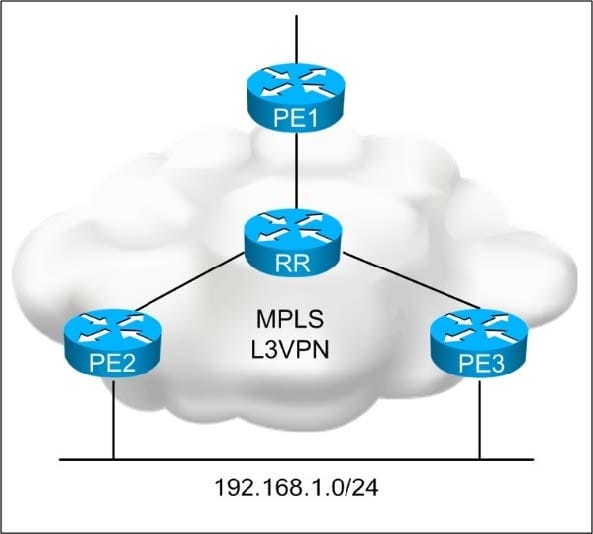
You are designing an IPv4 unicast Layer 3 VPN load-balancing solution. Which L3VPN feature needs to be configured on the PE routers to support the design requirement?
A. nonmatching route distinguishers
B. matching route target values
C. disable split horizon on PE2 and PE3
D. matching route distinguishers
-
Question 530:
Refer to the exhibit.

You are developing a migration plan to enable IPv6 in your IPv4 network. Starting at R3 and assuming default IS-IS operations, what is likely to happen when you enable IPv6 routing on the link from R3 to R2?
A. Only R3 and R2 have IPv4 and IPv6 reachability.
B. R2 receives an IPv6 default route from R3.
C. Loopback reachability between all routers for IPv4 is lost.
D. All routers except R2 are reachable through IPv4.
E. R3 advertises the link from R3-R2 to R1, R4 and R5 only.
Related Exams:
300-915
Developing Solutions using Cisco IoT and Edge Platforms (DEVIOT)300-920
Developing Applications for Cisco Webex and Webex Devices (DEVWBX)352-011
Cisco Certified Design Expert Practical500-052
Cisco Unified Contact Center Express500-173
Designing the FlexPod Solution (FPDESIGN)500-174
Implementing and Administering the FlexPod Solution (FPIMPADM)500-201
Deploying Cisco Service Provider Mobile Backhaul Solutions500-210
SP Optical Technology Field Engineer Representative500-220
Cisco Meraki Solutions Specialist500-230
Cisco Service Provider Routing Field Engineer
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Cisco exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 352-001 exam preparations and Cisco certification application, do not hesitate to visit our Vcedump.com to find your solutions here.