Exam Details
Exam Code
:352-001Exam Name
:CCDE WrittenCertification
:Cisco CertificationsVendor
:CiscoTotal Questions
:705 Q&AsLast Updated
:Jul 03, 2023
Cisco Cisco Certifications 352-001 Questions & Answers
-
Question 511:
A company wants to use an external appliance between its data center and WAN to optimize email and HTTP communications. The traffic flow must pass this appliance in both directions. The appliance is connected with only one interface to a Cisco IOS router and has a single IP address. Which two adjustments can you make to the network design so that the appliance is added into the traffic path? (Choose two.)
A. Configure static routes to route the traffic to the appliance.
B. Adjust the dynamic routing to route the traffic to the appliance.
C. Configure NAT to force the traffic to the appliance.
D. Configure a route map at the data center-side interface to forward the traffic to the appliance IP address.
E. Configure a route map at the appliance-facing interface to forward the traffic to the appliance IP address.
F. Configure a route map at the WAN-side interface to forward the traffic to the appliance IP address.
-
Question 512:
You have discovered packets you think are part of an attack. What benefit would you gain from redirecting them through a packet scrubbing device?
A. Packet scrubbing forwards valid traffic.
B. Packet scrubbing is "line rate."
C. Packet scrubbing filters all traffic.
D. Packet scrubbing provides better logging of suspected attacks.
-
Question 513:
Two MPLS service providers (SP1 and SP2) are offering inter-provider RFC 2547/4364- based IP-VPN service to an enterprise customer. IP traffic among some of the customer's sites has to traverse both of the service providers. The service providers and the enterprise do not know what the minimum MTU is along the end-to-end path.
What could be done to guarantee that large packets are not dropped for MTU-related reasons?
A. enable Path MTU Discovery on all devices within SP1 and SP2
B. enable Path MTU Discovery on all devices within the enterprise
C. configure the IP sender or senders to set the DF flag in the IP header
D. configure the IP sender or senders to clear the DF flag in the IP header
-
Question 514:
Refer to the exhibit.
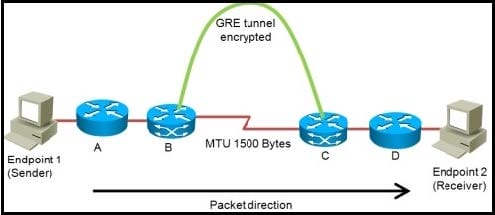
You are planning the design of an encrypted WAN. IP packets will be transferred over
encrypted GRE tunnels between routers B and C. The packet size is limited to a maximum of 1500 bytes inside the WAN between routers B and C. If endpoint 1 tries to send 1500- byte IP packets to endpoint 2, in what three ways will the network design handle the fragmentation in three different possible network configurations?(Choose three.)
A. When router B fragments packets after the encryption, router C must reassemble these fragmented packets.
B. When router B fragments packets before the encryption, router C must reassemble these fragmented packets.
C. When router B fragments packets after the encryption, the endpoint 2 must reassemble these fragmented packets.
D. When router B fragments packets before the encryption, endpoint 2 must reassemble these fragmented packets.
E. When router A fragments packets, router C must reassemble these fragmented packets.
F. When router A fragments packets, endpoint 2 must reassemble these fragmented packets.
-
Question 515:
Refer to the exhibit.
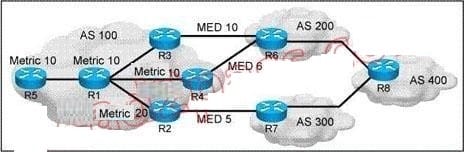
In this BGP setup, 10.1.1.0/24 is advertised by AS 400 to its peers. Border routers in AS 100 reset the next-hop router to themselves. R2, R3, and R4 are route reflector clients of R1 and R5 is a nonclient iBGP peer of R1. What is the BGP next hop on R5 for the address 10.1.1.0/24?
A. R1
B. R2
C. R3
D. R4
E. R6
-
Question 516:
Which network management tool should a network manager consult in order to pinpoint the cause of a routing recursion error?
A. debug (for BGP output)
B. syslog (for BGP errors)
C. RMON events group
D. SNMP routing traps
-
Question 517:
You are designing a traffic monitoring and analysis system for a customer. Which traffic monitoring technique would you recommend to place the least amount of burden on the network infrastructure?
A. SPAN monitor ports
B. NetFlow
C. IP NBAR
D. passive taps
-
Question 518:
You are a network designer and are responsible for ensuring that the network you design is secure. How do you plan to prevent infected devices on your network from sourcing random DDoS attacks using forged source addresses?
A. ACL-based forwarding
B. ACL filtering by destination
C. Unicast RPF loose mode
D. Unicast RPF strict mode
-
Question 519:
A network administrator is in charge of multiple IPsec VPN headend devices that service thousands of remote connectivity, point-to-point, IPsec/GRE tunnels. During a recent power outage, in which it was found that a backup power supply in one of those headend devices was faulty, one of the headend routers suffered a complete shutdown event. When the router was successfully recovered, remote users found intermittent connectivity issues that went away after several hours. Network operations staff accessed the headend devices and found that the recently recovered unit was near 100% CPU for a long period of time. How would you redesign the network VPN headend devices to prevent this from happening again in the future?
A. Move the tunnels more evenly across the headend devices.
B. Implement Call Admission Control.
C. Use the scheduler allocate command to curb CPU usage.
D. Change the tunnels to DMVPN.
-
Question 520:
Your company needs to baseline web traffic on a per-session basis for network application reporting. Which two mechanisms, when combined, fulfill the requirement? (Choose two.)
A. Flexible Netflow
B. Remote Monitoring
C. Cisco IOS IP Service Level Agreement
D. Class-Based Quality of Service Management Information Base
E. Network-Based Application Recognition
Related Exams:
300-915
Developing Solutions using Cisco IoT and Edge Platforms (DEVIOT)300-920
Developing Applications for Cisco Webex and Webex Devices (DEVWBX)352-011
Cisco Certified Design Expert Practical500-052
Cisco Unified Contact Center Express500-173
Designing the FlexPod Solution (FPDESIGN)500-174
Implementing and Administering the FlexPod Solution (FPIMPADM)500-201
Deploying Cisco Service Provider Mobile Backhaul Solutions500-210
SP Optical Technology Field Engineer Representative500-220
Cisco Meraki Solutions Specialist500-230
Cisco Service Provider Routing Field Engineer
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Cisco exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 352-001 exam preparations and Cisco certification application, do not hesitate to visit our Vcedump.com to find your solutions here.