Exam Details
Exam Code
:352-001Exam Name
:CCDE WrittenCertification
:Cisco CertificationsVendor
:CiscoTotal Questions
:705 Q&AsLast Updated
:Jul 03, 2023
Cisco Cisco Certifications 352-001 Questions & Answers
-
Question 101:
A network design engineer is designing a new storage area network that combines multiple separate legacy SAN environments within a data center. Which technology isolates events within one of the SAN environment from the others?
A. FCIP tunnels
B. N-port ID Virtualization
C. N-Port Virtualization
D. Virtual SANs
-
Question 102:
Which two application requirements are mandatory for traffic to receive proper treatment when placed in the priority queue? (Choose two)
A. WRED drop treatment
B. Small transactions (HTTP ?like behavior)
C. Tolerance to packet loss
D. Intolerance to jitter
E. TCP based application
-
Question 103:
Which two options are IoT use cases that require the low-latency and high reliability that 5G networks provide? (Choose two)
A. Sports and Fitness
B. Smart Home
C. Automotive
D. Smart Cities
E. Industrial Automation
F. Health and wellness
-
Question 104:
The enterprise customer ABC Corp will deploy a centralized unified communications application to provide voice, and instant messaging to their branch offices. Some of the branch offices are located in remote locations and are connected via a 1.5 Mb/s Layer 3 VPN connection. Which two ways are the most cost-effective to ensure that this new application is implemented properly? (Choose two)
A. Use a low bitrate codec such as G 711
B. Set voice activity detection to avoid sending packets when the conversations is silent
C. Enable VRF-Lite on the CE router to create a separate voice VRF
D. Set LFI on the WAN connections to interleave the small voice packets with the large data packets
E. Set WAN optimization on the CE router to compress the voice packets for improved bandwidth utilization and performance
F. Use a low bitrate codec such as G 729
-
Question 105:
Which three options are important design functions of IPv6 first-hop security? (Choose three)
A. It prevents rogue DHCP servers farms assigning IPv6 addresses.
B. It prevents IPv6 packets fragmentation.
C. It limits IPv6 route the advertisement in the network.
D. It implements a broadcast-control mechanism.
E. It suppresses excessive multicast neighbor discovery.
F. It implements multihoming security.
-
Question 106:
As part of network design, two geographically separated data centers must be interconnected using Ethernet-over-MPLS pseudowire. The link between the sites is stable, the topology has no apparent loops, and the root bridges for the respective VLANs are stable and unchanging. Which aspect must be the part of the design to mitigate the risk of connectivity issues between the data centers?
A. Enable Spanning Tree on one data center, and Rapid Reconfiguration of Spanning tree on the other
B. Ensure that the spanning tree diameter for one or more VLANs is not too large.
C. Enable UDLD on the link between the data centers.
D. Enable root guard on the link between the data centers.
-
Question 107:
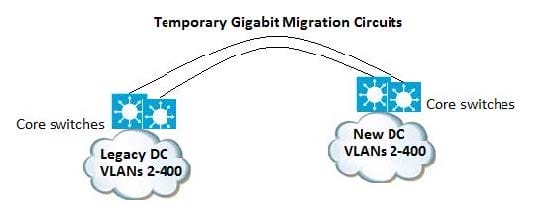
You are designing a data center migration from one location to another, which requires all existing VLANs spanned to the new data center to maintain host IP addressing. Two temporary Gigabit Ethernet circuits are available to extend the
VLANs at Layer 2 to the location as trunk links between core switches in each location.
Which solution provides maximum fault isolation between the two data centers to ensure a Layer Issue in one data center does not affect the other during the migration?
A. Perform BPDU filtering over the trunk links
B. Enable STP PortFast on host ports within each data center
C. Run the dual links as multichassis Etherchannel trunk between core switches within each location
D. Perform HSRP filtering over the trunk links to maintain active HSRP gateways within each data center for each VLAN
-
Question 108:
In a network with dynamic mutual redistribution between multiple OSPFv2 and EIGRP boundaries, which two mechanisms avoid suboptimal routing? (Choose two)
A. Route filtering
B. AD manipulation
C. Matching EIGRP process ID
D. Matching OSPF external routes
E. Route tagging
-
Question 109:
Your customer recently acquired a company with a national WAN of 750 locations consisting of MPLS VPN-based sales, Internet-based sites and sites with direct links to regional hub sites. The existing network has MPLS VPN-based sites. Which solution ensure security and encryption across all sites to meet an audit requirement?
A. Implement a hierarchical DMVPN-based hub-and-spoke network with IPsec encryption
B. Migrate newly acquired sites to the MPLS VPN-based service of the parent company
C. Implement a GETVPN-based solution across all sites with selective traffic encryption
D. Implement a GETVPN-based solution across all sites with redundant key servers
-
Question 110:
Which native mechanism does OSPF use to prevent loops in MPLS VPNs?
A. CE devices that run OSPF set the DN bit toward the PE router
B. PE devices that run OSPF clear the DN bit toward the CE router
C. CE devices that run OSPF clear the DN bit toward the PE router
D. Creation of PE to PE OSPF sham link across the MPLS-created super backbone
E. PE routers verify OSPF domain IDs used by CE OSPF processes
F. PE devices that run OSPF set the DN bit toward the CE router
Related Exams:
300-915
Developing Solutions using Cisco IoT and Edge Platforms (DEVIOT)300-920
Developing Applications for Cisco Webex and Webex Devices (DEVWBX)352-011
Cisco Certified Design Expert Practical500-052
Cisco Unified Contact Center Express500-173
Designing the FlexPod Solution (FPDESIGN)500-174
Implementing and Administering the FlexPod Solution (FPIMPADM)500-201
Deploying Cisco Service Provider Mobile Backhaul Solutions500-210
SP Optical Technology Field Engineer Representative500-220
Cisco Meraki Solutions Specialist500-230
Cisco Service Provider Routing Field Engineer
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Cisco exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 352-001 exam preparations and Cisco certification application, do not hesitate to visit our Vcedump.com to find your solutions here.